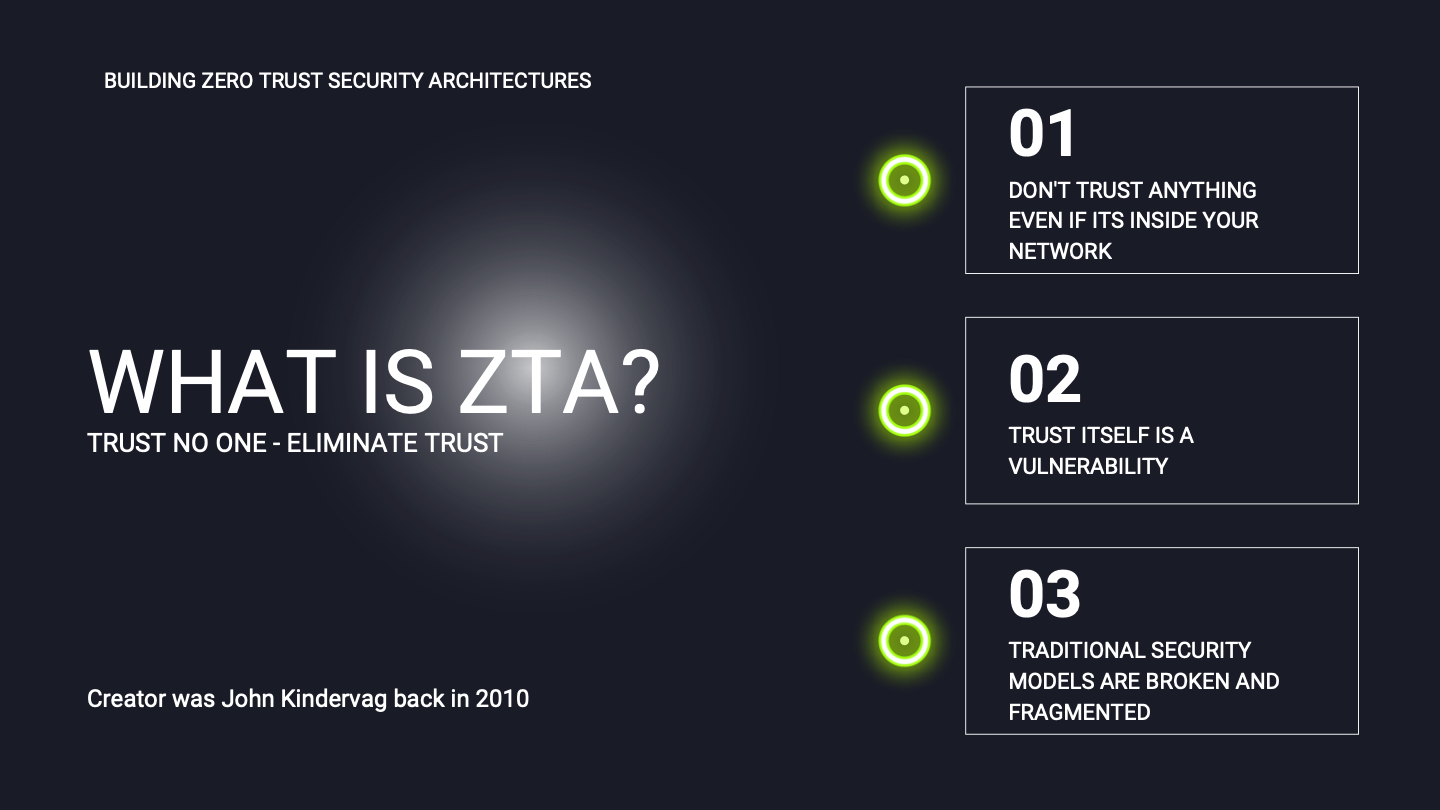
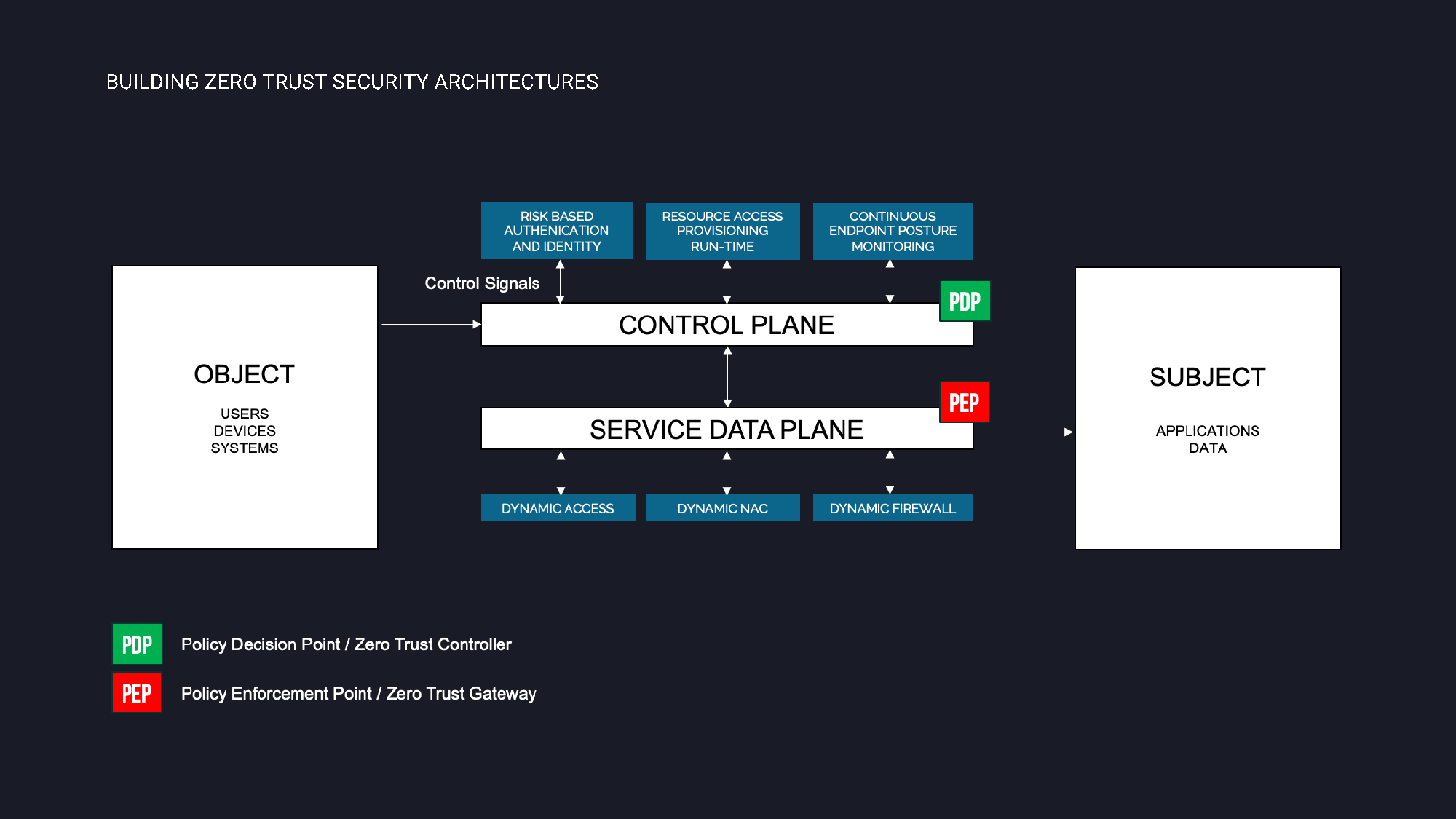
Trust itself is a vulnerability
Organizations are increasingly moving away from the traditional perimeter defense security. The old notion was that a company has a perimeter where defenses are deployed and consequently safeguarding the entire organization. Today, remote working and mixed hybrid cloud environments complicate this notion, and therefore, establishing a perimeter as the main security defense has become impossible.
One of the most important principles in the Zero Trust model is the removal of implicit trust in users, devices, or applications. This is the first principle of the Zero Trust model “Never trust, always verify”. By removing the traditional perimeter of the defense, each user, device, and app must earn trust on an ongoing basis.
The second core principle of the Zero Trust architecture focuses on the level of privileges that are assigned to users and other devices and objects. The “Least Privilege” principle states that each user or device should only be granted just enough privileges to be able to perform their function. This way, the company limits the amount of possible damage that any subject can make.
The third principle of the Zero Trust Model states that a company should always assume a breach. This encourages cybersecurity teams to plan for the worst-case scenarios by building detailed and tested incident response plans. The team is thus better prepared for actual security incidents. Another key improvement that this principle provides companies is that assuming a breach entails that other security measures have been taken to reduce the impact of a breach. For example, the network security team might implement the concepts of micro segmentation to limit the amount of damage from the breach.
The Zero Trust model represents a fundamental shift in the network functionality, especially with user authentication. It simplifies the user experience in terms of how the login process works, while also providing increased security with constant verification. This is the first step towards the actual Zero Trust security model.
Trust itself is a vulnerability
Organizations are increasingly moving away from the traditional perimeter defense security. The old notion was that a company has a perimeter where defenses are deployed and consequently safeguarding the entire organization. Today, remote working and mixed hybrid cloud environments complicate this notion, and therefore, establishing a perimeter as the main security defense has become impossible.
One of the most important principles in the Zero Trust model is the removal of implicit trust in users, devices, or applications. This is the first principle of the Zero Trust model “Never trust, always verify”. By removing the traditional perimeter of the defense, each user, device, and app must earn trust on an ongoing basis.
The second core principle of the Zero Trust architecture focuses on the level of privileges that are assigned to users and other devices and objects. The “Least Privilege” principle states that each user or device should only be granted just enough privileges to be able to perform their function. This way, the company limits the amount of possible damage that any subject can make.
The third principle of the Zero Trust Model states that a company should always assume a breach. This encourages cybersecurity teams to plan for the worst-case scenarios by building detailed and tested incident response plans. The team is thus better prepared for actual security incidents. Another key improvement that this principle provides companies is that assuming a breach entails that other security measures have been taken to reduce the impact of a breach. For example, the network security team might implement the concepts of micro segmentation to limit the amount of damage from the breach.
The Zero Trust model represents a fundamental shift in the network functionality, especially with user authentication. It simplifies the user experience in terms of how the login process works, while also providing increased security with constant verification. This is the first step towards the actual Zero Trust security model.
Zero Trust Strategies
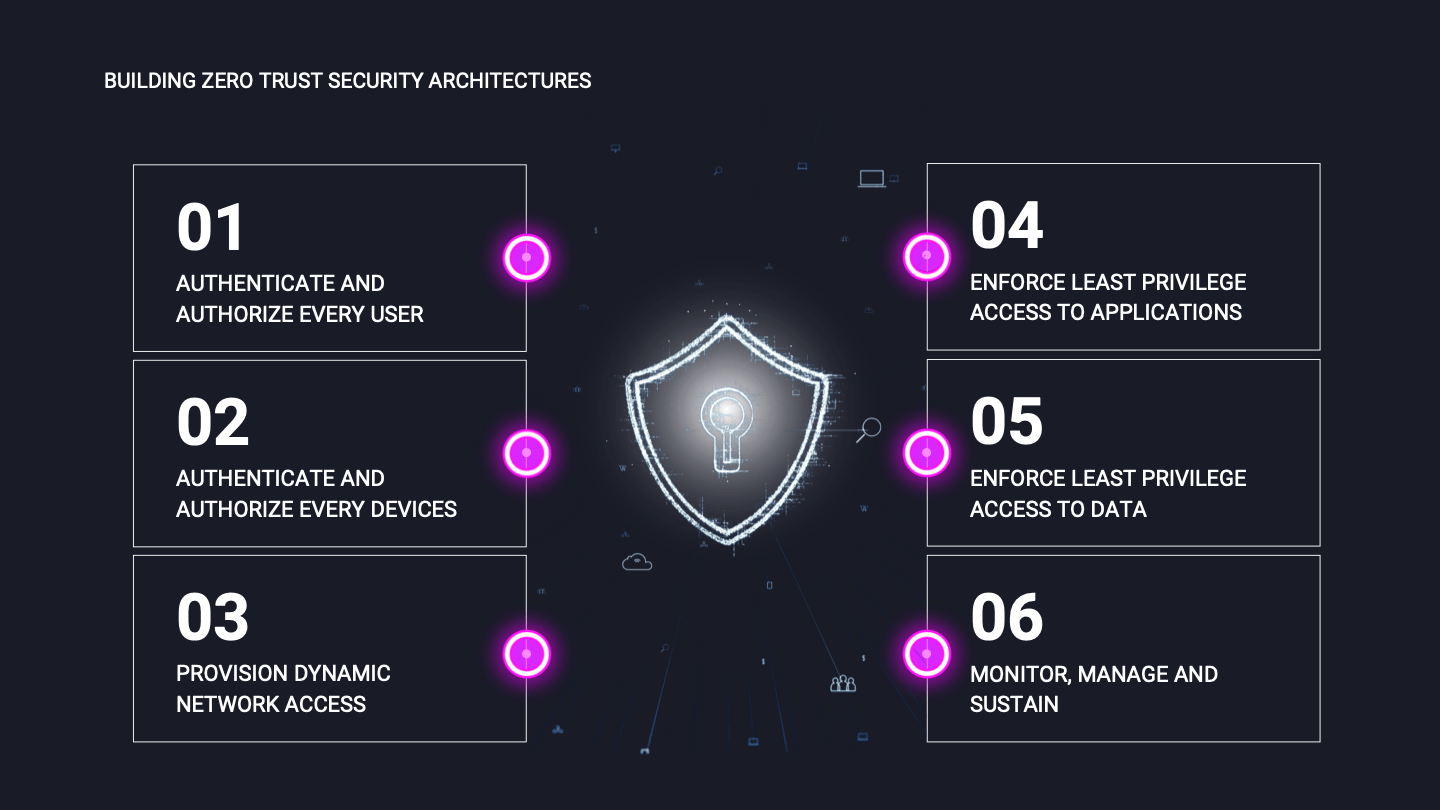
To implement the Zero Trust model, companies need to implement specific security controls and technology solutions to achieve the end goal. The strategies focus on users or identities, devices, applications, infrastructure, and networks.
Treat The User or Identity as the New Perimeter
Since user accounts and IoT device accounts function as the primary source of entry and access to the network, applying the “always verify” principle to each identity will effectively push the old network perimeter towards the identities trying to access your network and data.
Improve Authentication
By deploying MFA or multi-factor authentication into identity management, along with continuous authentication, companies can increase their security posture by using additional security measures. Many options can be applied from device compliance, location, and IP address to verify an identity.
Deploy Passwordless Authentication
Since Microsoft’s recent announcement regarding the adoption of passwordless authentication, companies are beginning to shift away from passwords as the main authentication mechanism towards using PINs and fingerprint technology. Additionally, user devices could create cryptographic keys that can be unlocked with biometric technology, allowing the user to access the company’s resources.
Segmenting the Network
In today’s mobile hybrid cloud environment, all data is accessed over the network infrastructure. It is necessary to perform micro segmentation and conduct a deeper analysis of the network to better safeguard the critical data point. This will improve network visibility and prevent hackers from moving laterally throughout the network.
Securing Devices
Just as important as the previous steps, securing devices that are on-premises or in remote locations is important in order to facilitate the Zero Trust model. Therefore, security policies should be applied to all devices trying to access any network resources regardless of location or status. Whether a user is authenticating with a corporate laptop or his mobile device, the same security measures need to be taken to ensure secure access. Security policies can apply conditions such as device patch status, device compliance, MFA, and much more.
Application Segmentation
Perhaps the least talked about step is the segmentation of all applications in the company’s environment. A company needs to have application control mechanisms in place in order to provide apps with the right level of access, balancing between functionality and access control. The app control should be able to discover any unwanted application use, have access restrictions in place and monitor for any abnormal behavior.
Define Access Control and Roles
Since remote work has become the primary mode of working, defining the appropriate roles for each authorization purpose can be difficult. Since the number of remote workers has increased dramatically, companies need to find a better way to create proper security controls. One practical method is to define roles and connect them with specific authorization policies. The only thing that companies should be wary about is creating too many granular roles and not being able to manage them in the future.
The Future of Zero Trust Models is here. Many companies are moving their infrastructure to the cloud and allowing employees to work from home. Given this massive shift, the only way to properly secure their networks and data is to implement the Zero Trust principles and strategies. A lot of effort needs to be put into establishing The Zero Trust model, but it is arguably the only way into the future of doing business in a secure way.
Zero Trust Strategies
To implement the Zero Trust model, companies need to implement specific security controls and technology solutions to achieve the end goal. The strategies focus on users or identities, devices, applications, infrastructure, and networks.
Treat The User or Identity as the New Perimeter
Since user accounts and IoT device accounts function as the primary source of entry and access to the network, applying the “always verify” principle to each identity will effectively push the old network perimeter towards the identities trying to access your network and data.
Improve Authentication
By deploying MFA or multi-factor authentication into identity management, along with continuous authentication, companies can increase their security posture by using additional security measures. Many options can be applied from device compliance, location, and IP address to verify an identity.
Deploy Passwordless Authentication
Since Microsoft’s recent announcement regarding the adoption of passwordless authentication, companies are beginning to shift away from passwords as the main authentication mechanism towards using PINs and fingerprint technology. Additionally, user devices could create cryptographic keys that can be unlocked with biometric technology, allowing the user to access the company’s resources.
Segmenting the Network
In today’s mobile hybrid cloud environment, all data is accessed over the network infrastructure. It is necessary to perform micro segmentation and conduct a deeper analysis of the network to better safeguard the critical data point. This will improve network visibility and prevent hackers from moving laterally throughout the network.
Securing Devices
Just as important as the previous steps, securing devices that are on-premises or in remote locations is important in order to facilitate the Zero Trust model. Therefore, security policies should be applied to all devices trying to access any network resources regardless of location or status. Whether a user is authenticating with a corporate laptop or his mobile device, the same security measures need to be taken to ensure secure access. Security policies can apply conditions such as device patch status, device compliance, MFA, and much more.
Application Segmentation
Perhaps the least talked about step is the segmentation of all applications in the company’s environment. A company needs to have application control mechanisms in place in order to provide apps with the right level of access, balancing between functionality and access control. The app control should be able to discover any unwanted application use, have access restrictions in place and monitor for any abnormal behavior.
Define Access Control and Roles
Since remote work has become the primary mode of working, defining the appropriate roles for each authorization purpose can be difficult. Since the number of remote workers has increased dramatically, companies need to find a better way to create proper security controls. One practical method is to define roles and connect them with specific authorization policies. The only thing that companies should be wary about is creating too many granular roles and not being able to manage them in the future.
The Future of Zero Trust Models is here. Many companies are moving their infrastructure to the cloud and allowing employees to work from home. Given this massive shift, the only way to properly secure their networks and data is to implement the Zero Trust principles and strategies. A lot of effort needs to be put into establishing The Zero Trust model, but it is arguably the only way into the future of doing business in a secure way.
See also: