Introduction
BlackCat, also known as ALPHV-ng, ALPHV, and Noberus, is a Ransomware-as-a-Service (RaaS) threat that targets organizations across multiple sectors worldwide using the multi-level extortion tactic.
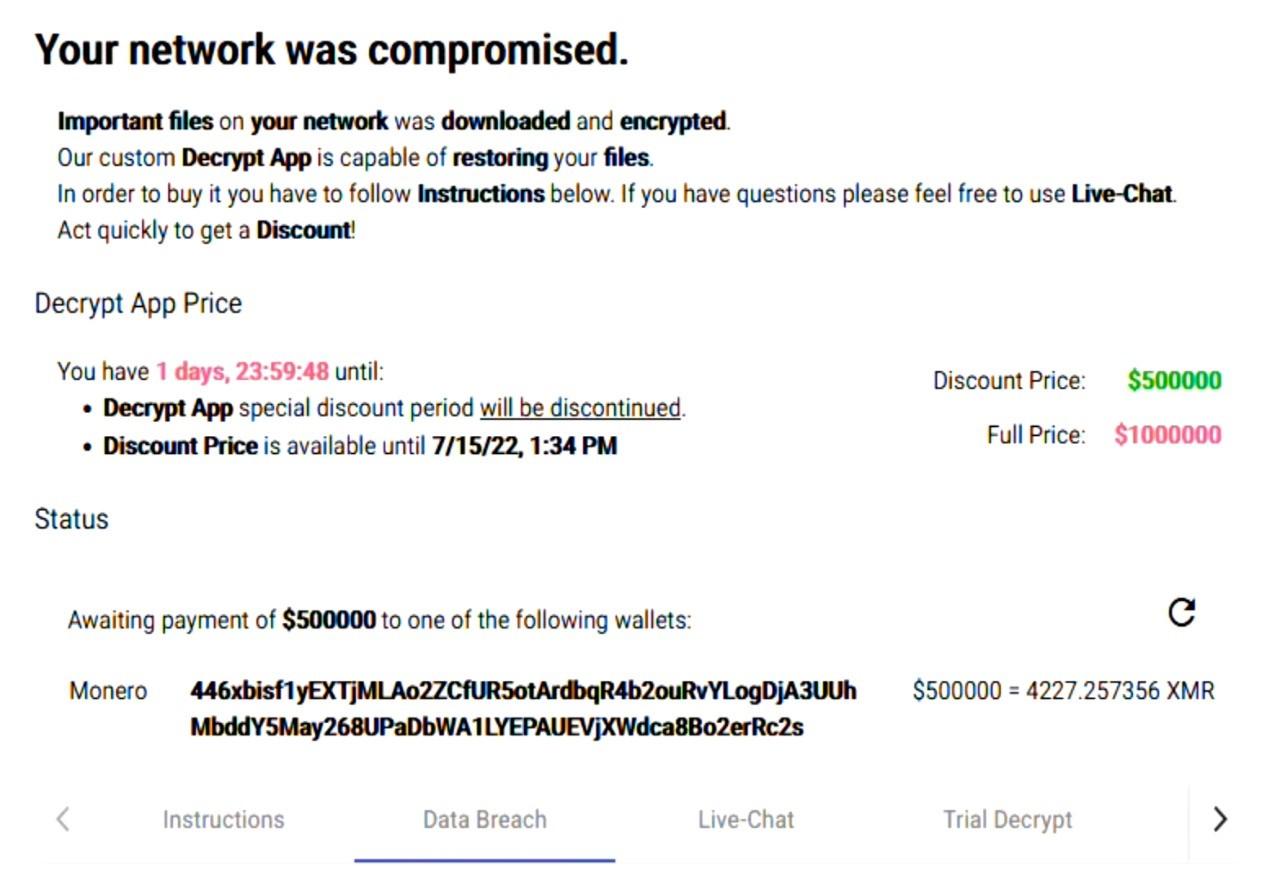
It was first observed in November 2021 and had reportedly been attacking targets in numerous countries, including Middle East, Australia, India, and the U.S, and demanding ransoms up to $2.5M in Bitcoin (BTC) or Monero (XLM).
DTS Solution Managed CSOC and XDR service HawkEye (www.hawk-eye.io) has confirmed RaaS is actively present across the Middle East region.
Blackcat APT group practices quadruple extortion in which after stealing and encryption of corporate data, they perform a DDoS attack on the public services of the victim organization, and sophisticated use of psychological distress techniques by contacting employees and informing customers and business partners of the breach.
In this article, we will be doing a technical analysis of the BlackCat ransomware attack.
Introduction
BlackCat, also known as ALPHV-ng, ALPHV, and Noberus, is a Ransomware-as-a-Service (RaaS) threat that targets organizations across multiple sectors worldwide using the multi-level extortion tactic.
It was first observed in November 2021 and had reportedly been attacking targets in numerous countries, including Middle East, Australia, India, and the U.S, and demanding ransoms up to $2.5M in Bitcoin (BTC) or Monero (XLM).
DTS Solution Managed CSOC and XDR service HawkEye (www.hawk-eye.io) has confirmed RaaS is actively present across the Middle East region.
Blackcat APT group practices quadruple extortion in which after stealing and encryption of corporate data, they perform a DDoS attack on the public services of the victim organization, and sophisticated use of psychological distress techniques by contacting employees and informing customers and business partners of the breach.
In this article, we will be doing a technical analysis of the BlackCat ransomware attack.
Technical Analysis
BlackCat is primarily delivered via 3rd-party framework toolkit (e.g., Cobalt Strike) or via exposed (and vulnerable) applications. As it is developed in the Rust language it has the capability to run on cross platforms like Windows and Linux operating systems.
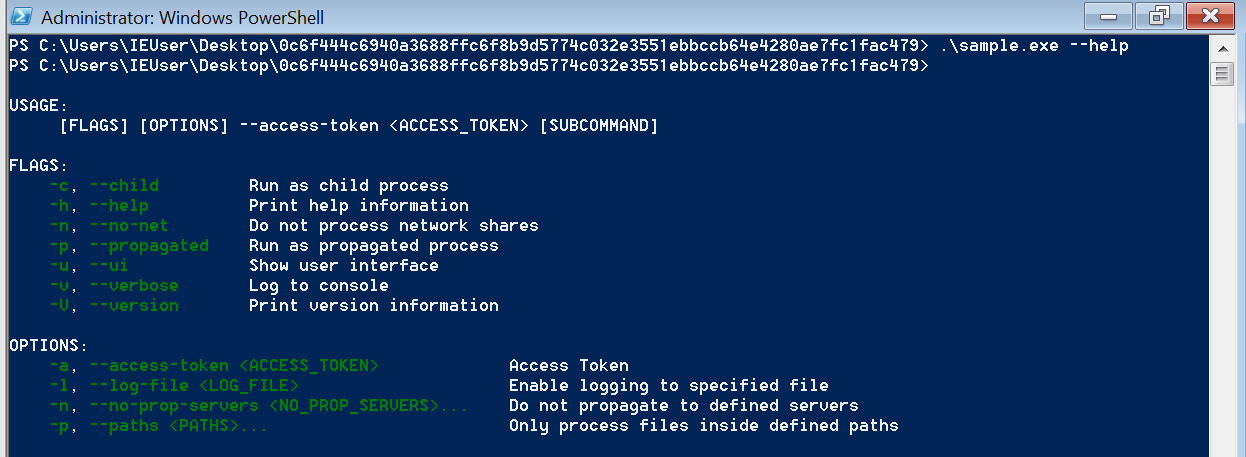
When executed, the ransomware offers several options for customizing its execution. Most arguments are optional, but an access token is a required parameter that can be of any value and it might be used to evade automated sandboxes.
Technical Analysis
BlackCat is primarily delivered via 3rd-party framework toolkit (e.g., Cobalt Strike) or via exposed (and vulnerable) applications. As it is developed in the Rust language it has the capability to run on cross platforms like Windows and Linux operating systems.
When executed, the ransomware offers several options for customizing its execution. Most arguments are optional, but an access token is a required parameter that can be of any value and it might be used to evade automated sandboxes.
The recent Linux variant also provides support for VMware ESXi hosts including the ability to stop virtual machines and, if enabled, wipe virtual machine snapshots to thwart recovery efforts.
In verbose mode (-v) the following output can be observed upon launch of the BlackCat ransomware.
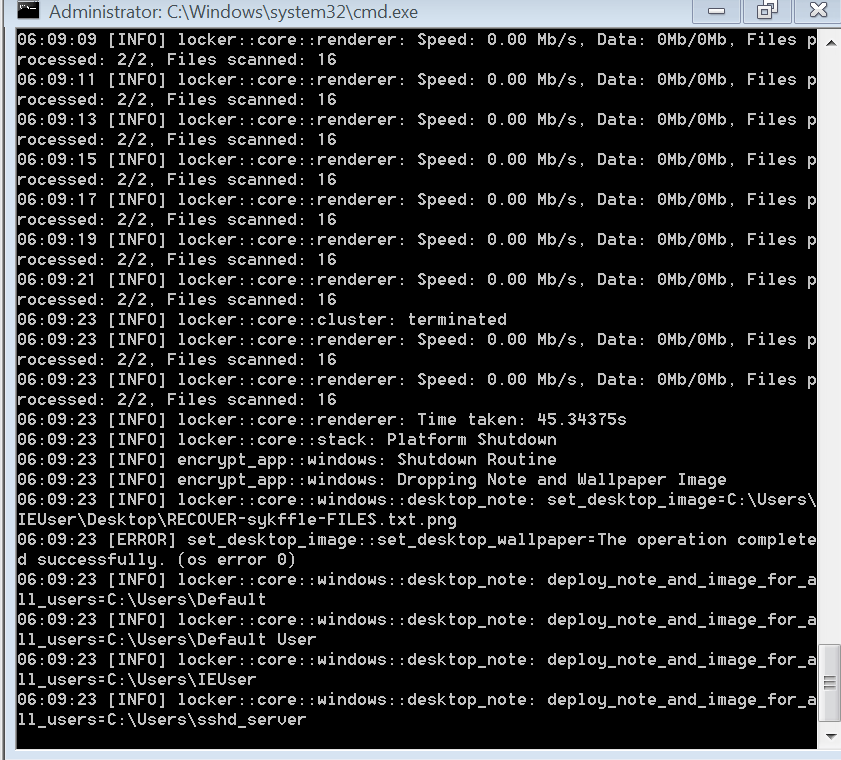
Upon launch, the malware attempts to create an Access Key by concatenating the access token passed as a parameter and the system UUID. This access key is a parameter of the recovery URL displayed in the ransom note. Both the Linux and Windows variants include a multi-threaded worker pool that spawns a ‘file worker pool’ comprised of four workers that are used to open and modify each target file, replacing the original content with encrypted data.
The recent Linux variant also provides support for VMware ESXi hosts including the ability to stop virtual machines and, if enabled, wipe virtual machine snapshots to thwart recovery efforts.
In verbose mode (-v) the following output can be observed upon launch of the BlackCat ransomware.
BlackCat also includes some privilege escalation capabilities like Masquerade_PEB, UAC Bypass, and exploiting CVE-2016-0099. After the initial setup, BlackCat will attempt to terminate any processes or services listed within the configuration such as any processes which may inhibit the encryption process.
“encsvc”,”thebat”,”mydesktopqos”,”xfssvccon”,”firefox”,”infopath”,”winword”,”steam”,”synctime”, “notepad”,”ocomm”,”onenote”,”mspub”,”thunderbird”,”agntsvc”,”sql”,”excel”,”powerpnt”, “outlook”,”wordpad”,”dbeng50″,”isqlplussvc”,”sqbcoreservice”,”oracle”,”ocautoupds”, “dbsnmp”,”msaccess”,”tbirdconfig”,”ocssd”,”mydesktopservice”,”visio”, “sql*”, “mepocs”,”memtas”,”veeam”,”svc$”,”backup”,”sql”,”vss”,”msexchange”
There are also specific files and directories that are excluded from encryption. Much of this is configurable at the time of building the ransomware payloads.
“system volume information”,”intel”,”$windows.~ws”,”application data”,”$recycle.bin”, “mozilla”,”program files (x86)”,”program files”,”$windows.~bt”,”public”,”msocache”,”windows”,”default”,”all users”, “tor browser”, “programdata”,”boot”,”config.msi”,”google”,”perflogs”,”appdata”, “windows.old”, “desktop.ini”,”autorun.inf”,”ntldr”,”bootsect.bak”,”thumbs.db”,”boot.ini”,”ntuser.dat”, “iconcache.db”,”bootfont.bin”,”ntuser.ini”,”ntuser.dat.log”,”themepack”,”nls”,”diagpkg”, “msi”,”lnk”,”exe”,”cab”,”scr”,”bat”,”drv”,”rtp”,”msp”,”prf”,”msc”, “ico”, “key”,”ocx”,”diagcab”,”diagcfg”,”pdb”,”wpx”,”hlp”,”icns”,”rom”,”dll”,”msstyles”,”mod”,”ps1″,”ics”,”hta”,”bin”,”cmd”,”ani”,”386″,”lock”,”cur”,”idx”,”sys”,”com”,”deskthemepack”,”shs”,”ldf”,”theme”,”mpa”,”nomedia”, “spl”,”cpl”,”adv”,”icl”,”msu”
Once the processes and services are killed. BlackCat performs the following functions:
- Enable both ‘remote to local’ and ‘remote to remote’ symbolic links using fsutil to allow the creation of links that redirects to some other file or directory.
- Set the number of network requests the Server Service can make to the maximum.
- Enumerate all local disk partitions and mount the hidden partitions.
- Delete shadow copies using the vssadmin to thwart recovery efforts.
- Drop the predefined ransom note in each folder containing encrypted files as well as an image containing the short ransom note on the desktop.
- Spread and execute the ransomware on a remote host using credentials embedded in the payload.
- Clear all event logs using wevtutil tool.
BlackCat also includes some privilege escalation capabilities like Masquerade_PEB, UAC Bypass, and exploiting CVE-2016-0099. After the initial setup, BlackCat will attempt to terminate any processes or services listed within the configuration such as any processes which may inhibit the encryption process.
“encsvc”,”thebat”,”mydesktopqos”,”xfssvccon”,”firefox”,”infopath”,”winword”,”steam”,”synctime”, “notepad”,”ocomm”,”onenote”,”mspub”,”thunderbird”,”agntsvc”,”sql”,”excel”,”powerpnt”, “outlook”,”wordpad”,”dbeng50″,”isqlplussvc”,”sqbcoreservice”,”oracle”,”ocautoupds”, “dbsnmp”,”msaccess”,”tbirdconfig”,”ocssd”,”mydesktopservice”,”visio”, “sql*”, “mepocs”,”memtas”,”veeam”,”svc$”,”backup”,”sql”,”vss”,”msexchange”
There are also specific files and directories that are excluded from encryption. Much of this is configurable at the time of building the ransomware payloads.
“system volume information”,”intel”,”$windows.~ws”,”application data”,”$recycle.bin”, “mozilla”,”program files (x86)”,”program files”,”$windows.~bt”,”public”,”msocache”,”windows”,”default”,”all users”, “tor browser”, “programdata”,”boot”,”config.msi”,”google”,”perflogs”,”appdata”, “windows.old”, “desktop.ini”,”autorun.inf”,”ntldr”,”bootsect.bak”,”thumbs.db”,”boot.ini”,”ntuser.dat”, “iconcache.db”,”bootfont.bin”,”ntuser.ini”,”ntuser.dat.log”,”themepack”,”nls”,”diagpkg”, “msi”,”lnk”,”exe”,”cab”,”scr”,”bat”,”drv”,”rtp”,”msp”,”prf”,”msc”, “ico”, “key”,”ocx”,”diagcab”,”diagcfg”,”pdb”,”wpx”,”hlp”,”icns”,”rom”,”dll”,”msstyles”,”mod”,”ps1″,”ics”,”hta”,”bin”,”cmd”,”ani”,”386″,”lock”,”cur”,”idx”,”sys”,”com”,”deskthemepack”,”shs”,”ldf”,”theme”,”mpa”,”nomedia”, “spl”,”cpl”,”adv”,”icl”,”msu”
Once the processes and services are killed. BlackCat performs the following functions:
- Enable both ‘remote to local’ and ‘remote to remote’ symbolic links using fsutil to allow the creation of links that redirects to some other file or directory.
- Set the number of network requests the Server Service can make to the maximum.
- Enumerate all local disk partitions and mount the hidden partitions.
- Delete shadow copies using the vssadmin to thwart recovery efforts.
- Drop the predefined ransom note in each folder containing encrypted files as well as an image containing the short ransom note on the desktop.
- Spread and execute the ransomware on a remote host using credentials embedded in the payload.
- Clear all event logs using wevtutil tool.
Ransom Note and Image
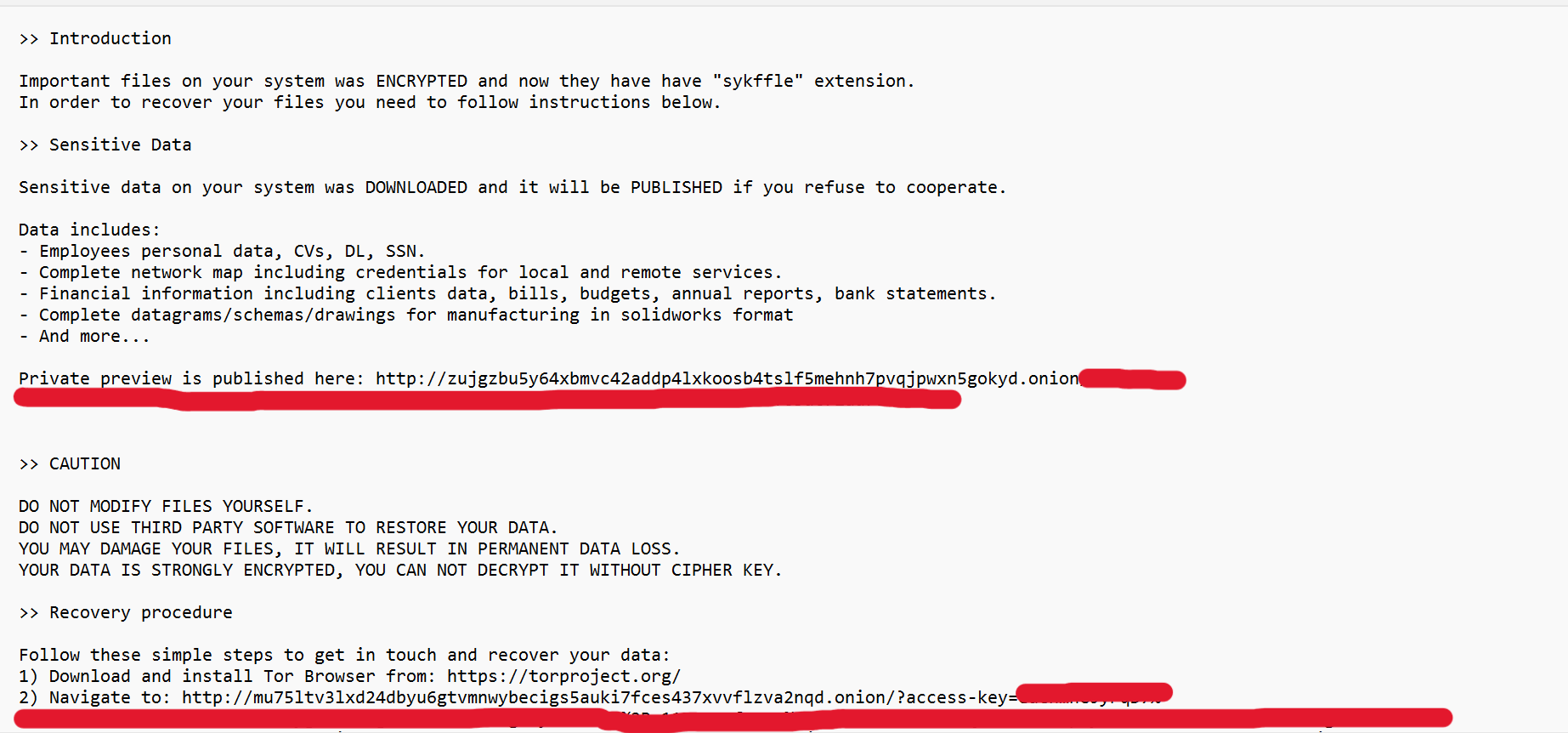
Fig 3. Ransom Note
Ransom Note and Image
Fig 3. Ransom Note
MITRE ATT&CK Technique to Monitor
T1027.002 – Obfuscated Files or Information: Software Packing
T1027 – Obfuscated Files or Information
T1007 – System Service Discovery
T1059 – Command and Scripting Interpreter
TA0010 – Exfiltration
T1082 – System Information Discovery
T1490 – Inhibit System Recovery
T1485 – Data Destruction
T1078 – Valid Accounts
T1486 – Data Encrypted for Impact
T1140 – Encode/Decode Files or Information
T1202 – Indirect Command Execution
T1543.003 – Create or Modify System Process: Windows Service
T1550.002 – Use Alternate Authentication Material: Pass the Hash
MITRE ATT&CK Technique to Monitor
T1027.002 – Obfuscated Files or Information: Software Packing
T1027 – Obfuscated Files or Information
T1007 – System Service Discovery
T1059 – Command and Scripting Interpreter
TA0010 – Exfiltration
T1082 – System Information Discovery
T1490 – Inhibit System Recovery
T1485 – Data Destruction
T1078 – Valid Accounts
T1486 – Data Encrypted for Impact
T1140 – Encode/Decode Files or Information
T1202 – Indirect Command Execution
T1543.003 – Create or Modify System Process: Windows Service
T1550.002 – Use Alternate Authentication Material: Pass the Hash
Recommended Actions
- Maintain software with the latest security updates.
- Deployment of EDR, NGAV, and advanced MDR services for real-time endpoint security monitoring.
- Ensure strong email security scanning and content inspection practices are maintained.
- Monitor and strongly, regularly communicate to employees to not open and report suspicious emails. Frequent cybersecurity awareness sessions.
- Make sure two-factor authentication is enabled in all services.
- Strong network segmentation across the server farm environment whether on-premises or in the cloud.
- Ensure privileged users are managed and continuously monitored.
- Ensure servers do not have unrestricted access to the Internet. Only whitelisted and approved FQDNs or URLs should be allowed for outbound connection.
- Use a backup system to backup server files and vault the backups so they are offline, and ransomware protected.
- Monitor large data transfer outbound to the Internet – user-based data transfer reporting to the cloud/bandwidth monitoring techniques.
- Monitoring Domain Controllers remote access and real-time monitoring of GPOs CRUD.
- Incident Response Playbook for Ransomware.
- Simulate Ransomware Tabletop Exercise – preparation is key.
Recommended Actions
- Maintain software with the latest security updates.
- Deployment of EDR, NGAV, and advanced MDR services for real-time endpoint security monitoring.
- Ensure strong email security scanning and content inspection practices are maintained.
- Monitor and strongly, regularly communicate to employees to not open and report suspicious emails. Frequent cybersecurity awareness sessions.
- Make sure two-factor authentication is enabled in all services.
- Strong network segmentation across the server farm environment whether on-premises or in the cloud.
- Ensure privileged users are managed and continuously monitored.
- Ensure servers do not have unrestricted access to the Internet. Only whitelisted and approved FQDNs or URLs should be allowed for outbound connection.
- Use a backup system to backup server files and vault the backups so they are offline, and ransomware protected.
- Monitor large data transfer outbound to the Internet – user-based data transfer reporting to the cloud/bandwidth monitoring techniques.
- Monitoring Domain Controllers remote access and real-time monitoring of GPOs CRUD.
- Incident Response Playbook for Ransomware.
- Simulate Ransomware Tabletop Exercise – preparation is key.
See also: