Industrial Control Systems (ICS) and Operational Technology (OT) play a critical role in the functioning of essential industries such as energy, transportation, manufacturing, and utilities. These systems are responsible for managing the operations of machinery and equipment used in these sectors. A security breach can have severe consequences, including physical damage and disruption of critical day-life processes of the masses. Therefore, ensuring the security of ICS and OT environments is of utmost importance to maintain the integrity and reliability of these essential services. Managed 24×7 Cyber Threat Detection and Response services are necessary to address these environments’ unique challenges and vulnerabilities. Offering like HawkEye provides specialized solutions to protect against these risks.
This article will explore the challenges organizations face operating ICS/OT environments and how managed 24×7 Cyber Threat Detection and Response services provided by companies like HawkEye can mitigate these risks.
Industrial Control Systems (ICS) and Operational Technology (OT) play a critical role in the functioning of essential industries such as energy, transportation, manufacturing, and utilities. These systems are responsible for managing the operations of machinery and equipment used in these sectors. A security breach can have severe consequences, including physical damage and disruption of critical day-life processes of the masses. Therefore, ensuring the security of ICS and OT environments is of utmost importance to maintain the integrity and reliability of these essential services. Managed 24×7 Cyber Threat Detection and Response services are necessary to address these environments’ unique challenges and vulnerabilities. Offering like HawkEye provides specialized solutions to protect against these risks.
This article will explore the challenges organizations face operating ICS/OT environments and how managed 24×7 Cyber Threat Detection and Response services provided by companies like HawkEye can mitigate these risks.
The Need for Cybersecurity in ICS/OT Environments
In recent years, there has been a growing awareness of the potential risks associated with cyberattacks in ICS/OT systems. These systems are critical to the operation of various industry sectors, including utilities, energy, manufacturing, airports, railways, telecommunications, and smart cities.
The cyber-physical nature of ICS/OT systems means that a successful cyberattack can lead to actual critical process failure or physical damage. This was demonstrated by the high-profile the attack on Saudi Aramco in 2012, which was one of the most destructive attacks ever launched against a single company. The attack used malware known as Shamoon to wipe out data on tens of thousands of computers, causing a shutdown of company operations for several days. A more recent example is the TRISIS cyberattack targeting a safety instrumentation system (SIS) in the Middle East, aiming to shut down the plant.
The consequences of a successful cyberattack can be severe, and organizations must take proactive measures to protect against such threats. It is essential to continuously monitor and detect threats in ICS/OT environments to ensure the security and safety of critical infrastructure.
Common Techniques Used by Malicious Actors to Exploit XIoT Devices
In recent years, there has been a growing awareness of the potential risks associated with cyberattacks in ICS/OT systems. These systems are critical to the operation of various industry sectors, including utilities, energy, manufacturing, airports, railways, telecommunications, and smart cities.
The cyber-physical nature of ICS/OT systems means that a successful cyberattack can lead to actual critical process failure or physical damage. This was demonstrated by the high-profile the attack on Saudi Aramco in 2012, which was one of the most destructive attacks ever launched against a single company. The attack used malware known as Shamoon to wipe out data on tens of thousands of computers, causing a shutdown of company operations for several days. A more recent example is the TRISIS cyberattack targeting a safety instrumentation system (SIS) in the Middle East, aiming to shut down the plant.
The consequences of a successful cyberattack can be severe, and organizations must take proactive measures to protect against such threats. It is essential to continuously monitor and detect threats in ICS/OT environments to ensure the security and safety of critical infrastructure.
HawkEye's Managed Cybersecurity Services for ICS/OT
As a leading provider of cybersecurity solutions, DTS Solution understands the unique cybersecurity challenges faced by organizations that operate ICS/OT environments. To help address these challenges, the cybersecurity organization has developed a range of managed cybersecurity services under the umbrella of HawkEye that is specifically designed to meet the needs of ICS and OT environments.
One of the key services HawkEye offers is “scheduled managed cybersecurity services.” To deliver these services, HawkEye’s team of SOC analysts specializing in ICS and OT will come on-site monthly to perform a complete cybersecurity review of logs, events, and audit trails across the environment.
HawkEye defines specific monitoring use cases prior to the agreement to ensure that necessary monitoring activities are carried out. The team also provides an “ICS/OT Cybersecurity Status Dashboard” with a monthly report that includes:
- patch management status level
- vulnerability status level
- user activity audit trail status
- removable media usage status
- network anomaly detection status
- access switch port status
- remote access monitoring status
- firewall logs review status, and
- industrial protocol violation status.
HawkEye's Managed Cybersecurity Services for ICS/OT
As a leading provider of cybersecurity solutions, DTS Solution understands the unique cybersecurity challenges faced by organizations that operate ICS/OT environments. To help address these challenges, the cybersecurity organization has developed a range of managed cybersecurity services under the umbrella of HawkEye that is specifically designed to meet the needs of ICS and OT environments.
One of the key services HawkEye offers is “scheduled managed cybersecurity services.” To deliver these services, HawkEye’s team of SOC analysts specializing in ICS and OT will come on-site monthly to perform a complete cybersecurity review of logs, events, and audit trails across the environment.
HawkEye defines specific monitoring use cases prior to the agreement to ensure that necessary monitoring activities are carried out. The team also provides an “ICS/OT Cybersecurity Status Dashboard” with a monthly report that includes:
- patch management status level
- vulnerability status level
- user activity audit trail status
- removable media usage status
- network anomaly detection status
- access switch port status
- remote access monitoring status
- firewall logs review status, and
- industrial protocol violation status.

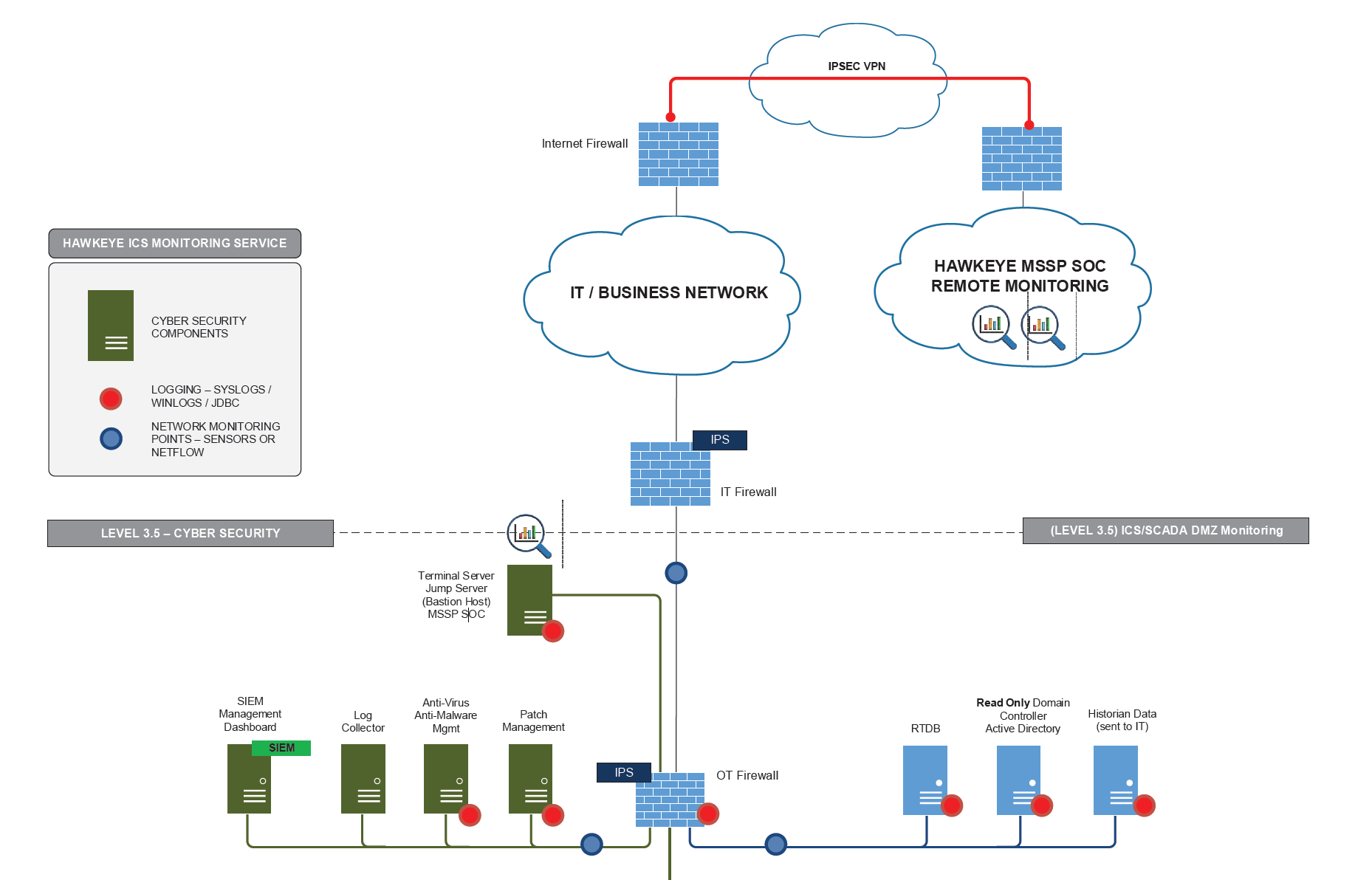
HawkEye also offers a “Secure Remote Monitoring Service” where all activities down to the threads of each process in the environment are monitored.
With this service, security events and logs are kept on the premises, and HawkEye’s SIEM platform log collection for remote monitoring resides in L3.75 DMZ, sandwiched between L3.5 and L4. HawkEye deploys two layers of firewalls managed by the client, including an IPSEC VPN Termination Firewall and an L3.5 DMZ Firewall (as shown in the image below).
Each Network is provided with a firewall of its own for the control of communication only in the secure direction.
Communication between L3, L3.5 DMZ, and L3.75 is outbound-only (SYSLOG UDP), and the reverse connection is impossible.
HawkEye also offers a “Secure Remote Monitoring Service” where all activities down to the threads of each process in the environment are monitored.
With this service, security events and logs are kept on the premises, and HawkEye’s SIEM platform log collection for remote monitoring resides in L3.75 DMZ, sandwiched between L3.5 and L4. HawkEye deploys two layers of firewalls managed by the client, including an IPSEC VPN Termination Firewall and an L3.5 DMZ Firewall (as shown in the image below).

Each Network is provided with a firewall of its own for the control of communication only in the secure direction.
Communication between L3, L3.5 DMZ, and L3.75 is outbound-only (SYSLOG UDP), and the reverse connection is impossible.
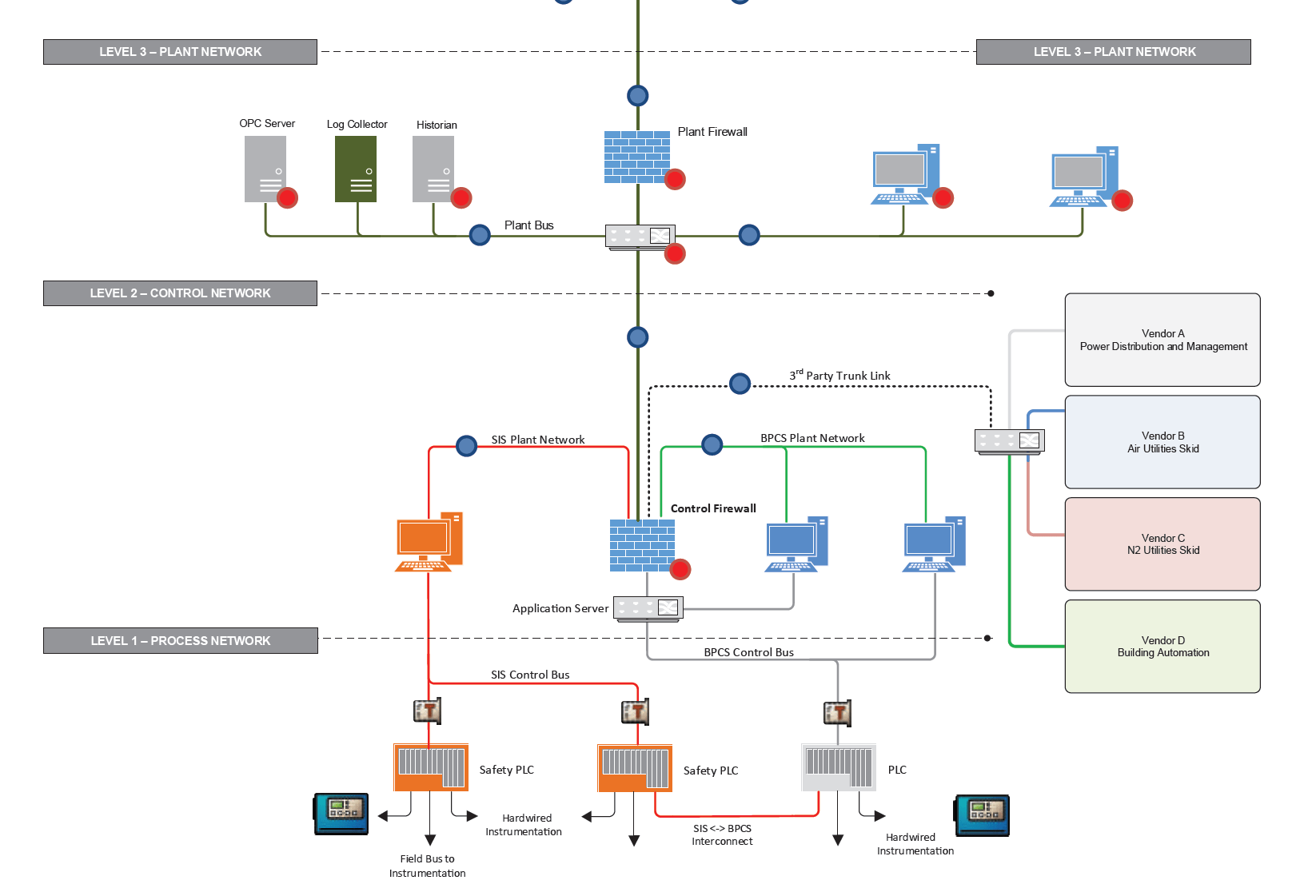
The HawkEye offshore monitoring team only has view functionality (READ-MONITOR mode) on the Terminal Server (Bastion Host), ensuring that data flows are highly secured.
To provide unparalleled visibility into the security posture of industrial networks, HawkEye has developed an “ICS MITRE ATT&CK Model.” This model is specifically tailored to critical infrastructure protection and emphasizes the importance of detection (with less to no false positives) rather than prevention.
HawkEye’s tools and techniques for developing monitoring controls within ICS/OT environments allow CISO/ICS Cyber Security Specialists and OT Operations Teams to gain unparalleled visibility into the security posture of their industrial networks. With HawkEye’s Managed Cybersecurity Services for ICS and OT, organizations can be confident that their critical infrastructure is protected from cyber threats.

The HawkEye offshore monitoring team only has view functionality (READ-MONITOR mode) on the Terminal Server (Bastion Host), ensuring that data flows are highly secured.
To provide unparalleled visibility into the security posture of industrial networks, HawkEye has developed an “ICS MITRE ATT&CK Model.” This model is specifically tailored to critical infrastructure protection and emphasizes the importance of detection (with less to no false positives) rather than prevention.
HawkEye’s tools and techniques for developing monitoring controls within ICS/OT environments allow CISO/ICS Cyber Security Specialists and OT Operations Teams to gain unparalleled visibility into the security posture of their industrial networks. With HawkEye’s Managed Cybersecurity Services for ICS and OT, organizations can be confident that their critical infrastructure is protected from cyber threats.
Benefits of Using HawkEye's Managed Cybersecurity Services for ICS/OT
By leveraging HawkEye’s Managed Cybersecurity Services, organizations can enjoy increased cybersecurity protection, enhanced visibility into their security posture, and compliance with industry standards and regulations.
Other benefits of using HawkEye’s managed cybersecurity services for ICS/OT environments include the following:
- 24/7 Monitoring: HawkEye’s team of experts continuously monitors and manages your ICS/OT assets and environment, meaning any potential security threat can be identified and addressed in real time.
- Real-time Threat Detection and Response: With HawkEye’s cybersecurity services, organizations can expect real-time detection of existing or newly emerging security threats with the help of HawkEyes’ cyber-threat intelligence feature, enabling a rapid response to contain and mitigate the threat before it causes significant damage to the ICS/OT environment.
- Comprehensive Cybersecurity Status Dashboard with Monthly Reports: HawkEye provides a comprehensive cybersecurity status dashboard that gives organizations a detailed overview of their security posture, including network topology, vulnerability status, and security alerts. The monthly reports provide further analysis and insights into security trends and any areas that need improvement.
- Compliance with Relevant Industry Standards and Regulations: HawkEye’s services are designed to help organizations meet relevant industry standards and regulations, such as UAE IA, NCA OTCC, IEC 62443, and ISA/IEC 62443, by providing ongoing risk assessments, security audits, and compliance reporting.
Visit the HawkEye website to get started with efficient clock-round ICS/OT security monitoring.
Benefits of Using HawkEye's Managed Cybersecurity Services for ICS/OT
By leveraging HawkEye’s Managed Cybersecurity Services, organizations can enjoy increased cybersecurity protection, enhanced visibility into their security posture, and compliance with industry standards and regulations.
Other benefits of using HawkEye’s managed cybersecurity services for ICS/OT environments include the following:
- 24/7 Monitoring: HawkEye’s team of experts continuously monitors and manages your ICS/OT assets and environment, meaning any potential security threat can be identified and addressed in real time.
- Real-time Threat Detection and Response: With HawkEye’s cybersecurity services, organizations can expect real-time detection of existing or newly emerging security threats with the help of HawkEyes’ cyber-threat intelligence feature, enabling a rapid response to contain and mitigate the threat before it causes significant damage to the ICS/OT environment.
- Comprehensive Cybersecurity Status Dashboard with Monthly Reports: HawkEye provides a comprehensive cybersecurity status dashboard that gives organizations a detailed overview of their security posture, including network topology, vulnerability status, and security alerts. The monthly reports provide further analysis and insights into security trends and any areas that need improvement.
- Compliance with Relevant Industry Standards and Regulations: HawkEye’s services are designed to help organizations meet relevant industry standards and regulations, such as UAE IA, NCA OTCC, IEC 62443, and ISA/IEC 62443, by providing ongoing risk assessments, security audits, and compliance reporting.
Visit the HawkEye website to get started with efficient clock-round ICS/OT security monitoring.
See also:
