Robotic Process Automation (RPA) Security and Review
Seid Yassin, our Senior Red Team and Application Security Lead Consultant, delivered a compelling presentation on Robotic Process Automation (RPA) security and review at the esteemed Black Hat MEA 2022. Taking place at the Black Hat MEA briefing stage 2 on November 17th, Seid shared his expertise and insights on the subject.
As a key member of DTS Solution’s Red Team, Seid Yassin provides both public and private sector clients in the MENA region with valuable assurance regarding the security posture of their products and infrastructure. With approximately 8 years of professional information security experience in offensive and defensive fields, Seid is well-equipped to address the intricacies of RPA security.
During the presentation, Seid Yassin shared key takeaways and highlighted crucial aspects of RPA security.
Robotic Process Automation (RPA) involves automating business operations by leveraging digital robots to streamline tasks across applications and systems, thereby reducing human intervention. RPA finds application in various areas, including workflow automation, infrastructure management, and labour-intensive back-office processes.
While RPA offers organizations increased efficiency and cost optimization by orchestrating robots to handle high-volume tasks, it is crucial to recognize the security implications that accompany the adoption of this technology. Implementing RPA introduces new attack surfaces and potential data breaches, necessitating a structured approach to evaluating RPA processes effectively.
Robotic Process Automation (RPA) Security and Review
Seid Yassin, our Senior Red Team and Application Security Lead Consultant, delivered a compelling presentation on Robotic Process Automation (RPA) security and review at the esteemed Black Hat MEA 2022. Taking place at the Black Hat MEA briefing stage 2 on November 17th, Seid shared his expertise and insights on the subject.
As a key member of DTS Solution’s Red Team, Seid Yassin provides both public and private sector clients in the MENA region with valuable assurance regarding the security posture of their products and infrastructure. With approximately 8 years of professional information security experience in offensive and defensive fields, Seid is well-equipped to address the intricacies of RPA security.
During the presentation, Seid Yassin shared key takeaways and highlighted crucial aspects of RPA security.
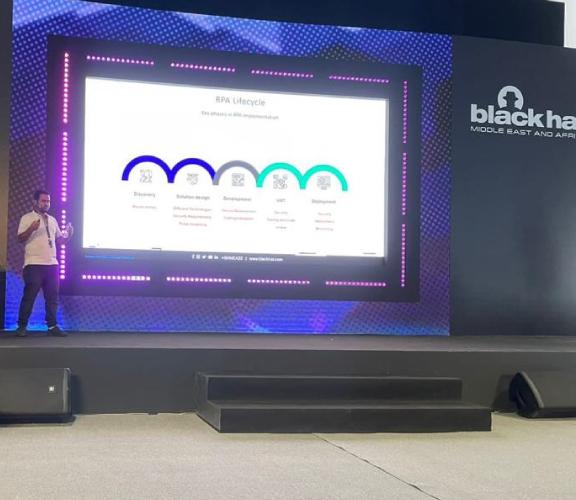
Robotic Process Automation (RPA) involves automating business operations by leveraging digital robots to streamline tasks across applications and systems, thereby reducing human intervention. RPA finds application in various areas, including workflow automation, infrastructure management, and labor-intensive back-office processes.
While RPA offers organizations increased efficiency and cost optimization by orchestrating robots to handle high-volume tasks, it is crucial to recognize the security implications that accompany the adoption of this technology. Implementing RPA introduces new attack surfaces and potential data breaches, necessitating a structured approach to evaluating RPA processes effectively.
To evaluate RPA processes, organizations should embark on a process description review, which entails understanding where RPA is implemented, assessing the level of automation, and conducting interviews with key stakeholders such as business owners, application owners, and development teams. This review aids in the identification of risks and controls associated with RPA processes.
Furthermore, it is essential to identify and comprehend business and security concerns related to RPA through the use of use cases and abuse case scenarios. This involves creating such cases based on requirements, reviewing existing process design documents, analyzing interactions between bots and orchestrator machines, and assessing roles and responsibilities within the RPA ecosystem. Additionally, testing the storage and retrieval of sensitive information, verifying the security of transactions executed by bots, and assessing whether the application supports project security requirements are integral steps in evaluating RPA security.
By employing Threat Modelling techniques, organizations can systematically identify potential risks and vulnerabilities within RPA processes. This allows for the implementation of appropriate security controls and safeguards, further enhancing the overall security of RPA environments.
The importance of RPA security cannot be overstated. RPA systems interact with various applications, databases, and user interfaces, making them potential targets for cyber threats. Failure to address security concerns may result in data breaches, unauthorized access, and malicious activities, compromising the integrity and confidentiality of critical business information. Therefore, it is paramount to implement robust RPA security measures to mitigate these risks effectively.
To evaluate RPA processes, organizations should embark on a process description review, which entails understanding where RPA is implemented, assessing the level of automation, and conducting interviews with key stakeholders such as business owners, application owners, and development teams. This review aids in the identification of risks and controls associated with RPA processes.
Furthermore, it is essential to identify and comprehend business and security concerns related to RPA through the use of use cases and abuse case scenarios. This involves creating such cases based on requirements, reviewing existing process design documents, analyzing interactions between bots and orchestrator machines, and assessing roles and responsibilities within the RPA ecosystem. Additionally, testing the storage and retrieval of sensitive information, verifying the security of transactions executed by bots, and assessing whether the application supports project security requirements are integral steps in evaluating RPA security.
By employing Threat Modelling techniques, organizations can systematically identify potential risks and vulnerabilities within RPA processes. This allows for the implementation of appropriate security controls and safeguards, further enhancing the overall security of RPA environments.
The importance of RPA security cannot be overstated. RPA systems interact with various applications, databases, and user interfaces, making them potential targets for cyber threats. Failure to address security concerns may result in data breaches, unauthorized access, and malicious activities, compromising the integrity and confidentiality of critical business information. Therefore, it is paramount to implement robust RPA security measures to mitigate these risks effectively.
Organizations commonly face specific challenges when it comes to RPA security. These include the lack of secure coding practices, which can lead to exploitable vulnerabilities in poorly developed bots. Additionally, proper credential management is crucial for storing and securing login credentials for the various systems that bots interact with. Access control is another challenge, as organizations need to ensure appropriate user access and permissions for RPA systems. Compliance with relevant regulations such as GDPR, HIPAA, or PCI DSS poses yet another challenge. Lastly, monitoring and auditing the activities of bots, detecting anomalies, and conducting regular security audits are ongoing concerns.
To address these challenges, organizations should adhere to RPA security best practices. These include following secure development practices, conducting code reviews to identify and fix vulnerabilities, and encrypting sensitive data during storage, transmission, and processing. Safely storing login credentials using encrypted password vaults and implementing multi-factor authentication are essential for effective credential management. Implementing role-based access control ensures proper access levels for bots and limits user privileges. Staying updated with relevant regulations and incorporating necessary controls within RPA.
See also:

