API Security Assessment
What is API?
An Application Programming Interface (API) is a software intermediary that allows your applications to communicate with one another. It provides routines, protocols, and tools for developers building software applications, while enabling the extraction and sharing of data in an accessible manner.
APIs are represented in different protocols like SOAP, RESTful API and SAML along with other protocols
Why API Security is Important?
As the world around us becomes more and more connected via internet connections, the need to build secure networks grows infinitely. APIs continue to be an integral business strategy across industries, and it doesn’t appear to be slowing down anytime soon, especially with the rise of IoT.
API plays a huge role as industry is moving towards Open banking. Open banking is a system under which banks open up their application programming interfaces (APIs), allowing third parties to access financial information needed to develop new apps and services and providing account holders greater financial transparency options. And this system is set to shake up the financial experiences for customers across the region – in a good way.
While open banking allows third parties to develop better personal finance management (PFM) applications, it places pressure on incumbents to improve their own offerings. Open banking services cultivate competition in the banking industry – forcing incumbents to either enhance their financial services or partner with fintechs.
APIs have been used to connect developers to payment networks as well as display billing details on a bank’s website. Through open banking, APIs are now being used to issue commands to third party providers.
APIs are also necessary for the functionality of Banking-as-a-Service (BaaS) – a key component of open banking. BaaS is an end-to-end process that connects fintechs and other third parties to banks’ systems directly through the use of APIs. It helps to build up banks’ offerings on top of financial providers’ regulated infrastructure.
API Security Threats
In traditional web applications, data processing is done on the server side, and the resulting web page is then sent to client browsers simply be rendered. Because of this, the entry points to the network architecture of the business were relatively few and straightforward to protect by setting up a web-application firewall (WAF) in front of the application server.
Modern API-based applications are very different. More and more, the UI uses APIs to send and receive the data from the backend servers to provide the functions of the application. It is now the clients that do the rendering and maintain the state.
With so many entry points often widespread in the network architecture, putting a firewall in front of a server is no longer enough to ensure all entry points are protected. In addition, a traditional WAF-based solution has no means to distinguish hacking API calls from legitimate API traffic. All this means that API security needs its own brand of security that focuses on strategies and solutions to understand and mitigate the unique vulnerabilities and security risks of APIs.
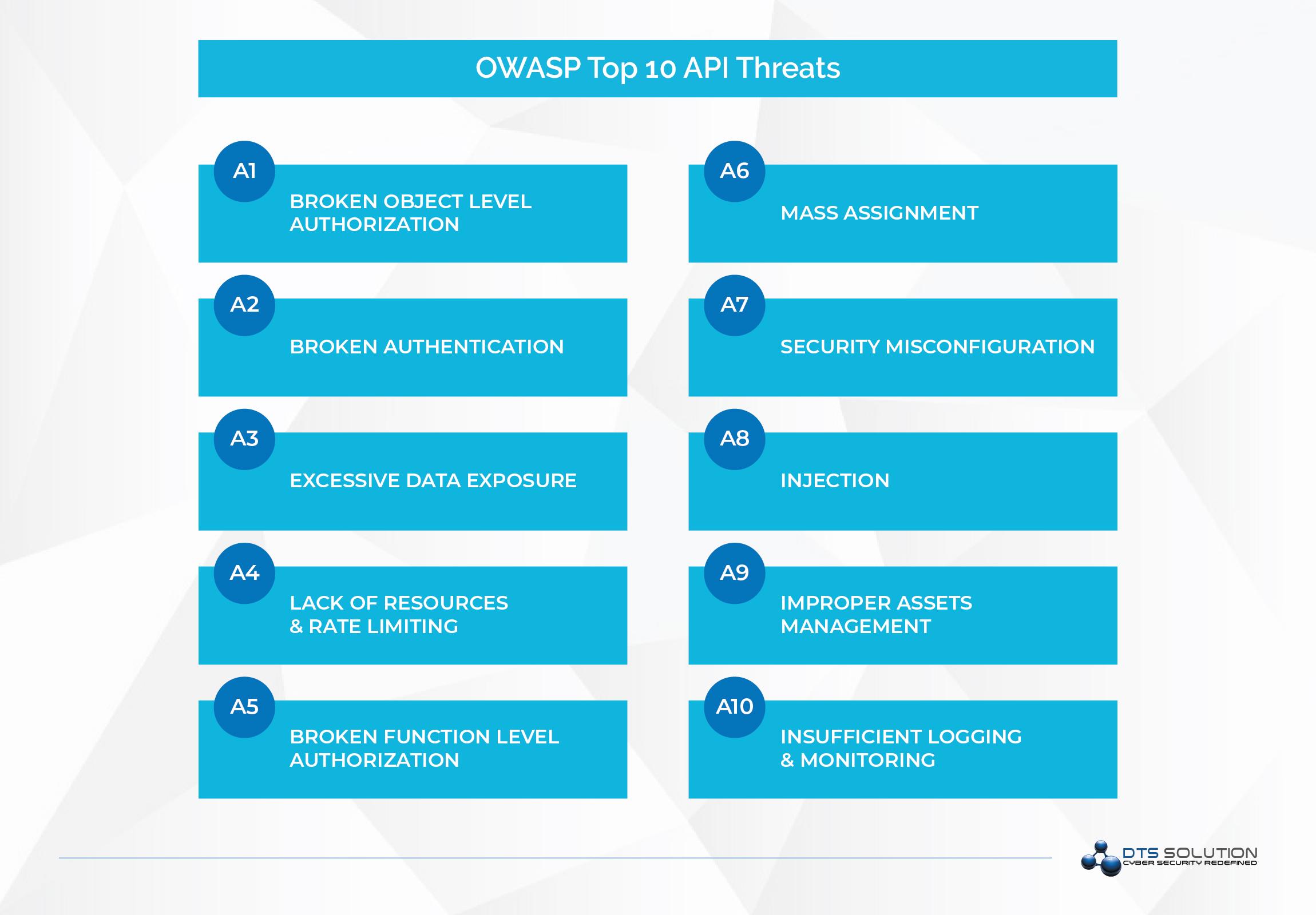
OWASP Top 10 API Threats:
- Broken object level authorization
- Broken authentication
- Excessive data exposure
- Lack of resources and rate limiting
- Broken function level authorization
- Mass assignment
- Security misconfiguration
- Injection
- Improper assets management
- Insufficient logging and monitoring
API Security Best Practices
Securing your API mostly depends on how your environment is setup and the purpose of you API, however here are general guidelines to follow the best practice when creating your API
- REST secure design principles
- Least privileges concept
- Fail safe defaults
- Use tokens, encryption and signatures
- Always use encryption in transmission (HTTPS)
- Never expose information on URLs
- Consider Oauth2 for RESTful API
- Follow Authentication and Authorization religiously
- Validate user input
- Use quotas and throttling
- Use API gateway when possible
API Gateway Roles in Security
Access control is the number-one security driver for API Gateway technology, serving as a governor of sorts so an organization can manage who can access an API and establish rules around how data requests are handled.
Access control almost always extends to establish other policies, including rate limits on API calls from certain sources, or even payment requirements for accessing all or certain resources through an API.
A typical API Gateway includes:
- Security (authentication and potentially authorization)
- Managing access quotas and throttling
- Caching (proxy statements and cache)
- API composition and processing
- Routing (possibly processing) to an "internal" API
- API health monitoring (performance monitoring)
- Versioning (possibly automation)
API Security Assessment
An Application Programming Interface (API) is a software intermediary that allows your applications to communicate with one another. It provides routines, protocols, and tools for developers building software applications, while enabling the extraction and sharing of data in an accessible manner.
APIs are represented in different protocols like SOAP, RESTful API and SAML along with other protocols
Why API Security is Important?
As the world around us becomes more and more connected via internet connections, the need to build secure networks grows infinitely. APIs continue to be an integral business strategy across industries, and it doesn’t appear to be slowing down anytime soon, especially with the rise of IoT.
API plays a huge role as industry is moving towards Open banking. Open banking is a system under which banks open up their application programming interfaces (APIs), allowing third parties to access financial information needed to develop new apps and services and providing account holders greater financial transparency options. And this system is set to shake up the financial experiences for customers across the region – in a good way.
While open banking allows third parties to develop better personal finance management (PFM) applications, it places pressure on incumbents to improve their own offerings. Open banking services cultivate competition in the banking industry – forcing incumbents to either enhance their financial services or partner with fintechs.
APIs have been used to connect developers to payment networks as well as display billing details on a bank’s website. Through open banking, APIs are now being used to issue commands to third party providers.
APIs are also necessary for the functionality of Banking-as-a-Service (BaaS) – a key component of open banking. BaaS is an end-to-end process that connects fintechs and other third parties to banks’ systems directly through the use of APIs. It helps to build up banks’ offerings on top of financial providers’ regulated infrastructure.
API Security Threats
In traditional web applications, data processing is done on the server side, and the resulting web page is then sent to client browsers simply be rendered. Because of this, the entry points to the network architecture of the business were relatively few and straightforward to protect by setting up a web-application firewall (WAF) in front of the application server.
Modern API-based applications are very different. More and more, the UI uses APIs to send and receive the data from the backend servers to provide the functions of the application. It is now the clients that do the rendering and maintain the state.
With so many entry points often widespread in the network architecture, putting a firewall in front of a server is no longer enough to ensure all entry points are protected. In addition, a traditional WAF-based solution has no means to distinguish hacking API calls from legitimate API traffic. All this means that API security needs its own brand of security that focuses on strategies and solutions to understand and mitigate the unique vulnerabilities and security risks of APIs.
OWASP Top 10 API Threats:
- Broken object level authorization
- Broken authentication
- Excessive data exposure
- Lack of resources and rate limiting
- Broken function level authorization
- Mass assignment
- Security misconfiguration
- Injection
- Improper assets management
- Insufficient logging and monitoring

API Security Best Practices
Securing your API mostly depends on how your environment is setup and the purpose of you API, however here are general guidelines to follow the best practice when creating your API
- REST secure design principles
- Least privileges concept
- Fail safe defaults
- Use tokens, encryption and signatures
- Always use encryption in transmission (HTTPS)
- Never expose information on URLs
- Consider Oauth2 for RESTful API
- Follow Authentication and Authorization religiously
- Validate user input
- Use quotas and throttling
- Use API gateway when possible
API Gateway Roles in Security
Access control is the number-one security driver for API Gateway technology, serving as a governor of sorts so an organization can manage who can access an API and establish rules around how data requests are handled.
Access control almost always extends to establish other policies, including rate limits on API calls from certain sources, or even payment requirements for accessing all or certain resources through an API.
A typical API Gateway includes:
- Security (authentication and potentially authorization)
- Managing access quotas and throttling
- Caching (proxy statements and cache)
- API composition and processing
- Routing (possibly processing) to an "internal" API
- API health monitoring (performance monitoring)
- Versioning (possibly automation)
See also:
