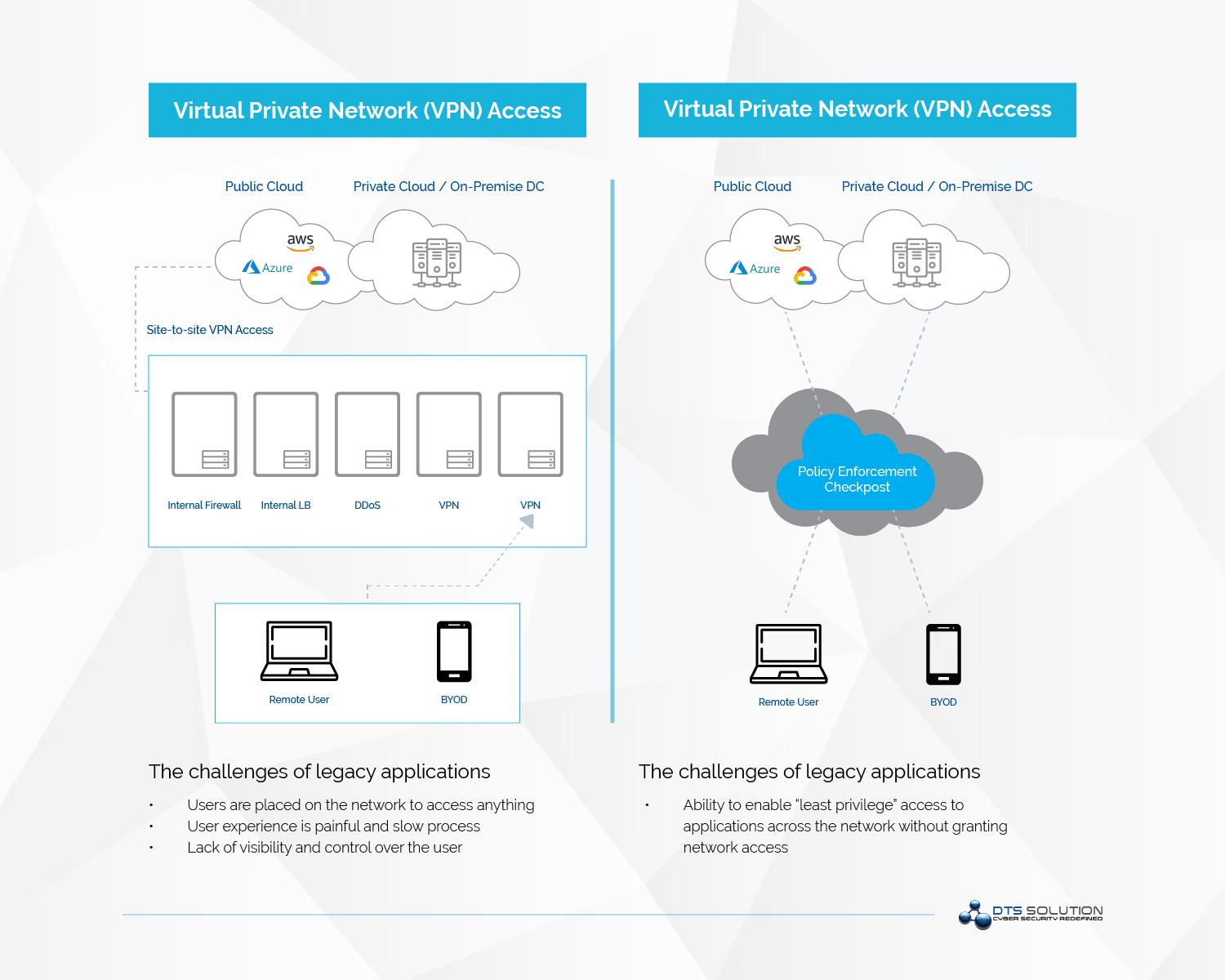
Proliferation of Remote Access
As the modern cyber-attacks have started to evolve, security researchers and recent security incidents have proven that the security controls that are offered by traditional VPN solutions (IPSEC VPN and SSL VPN) are not adequate anymore.
Proliferation of Remote Access
As the modern cyber-attacks have started to evolve, security researchers and recent security incidents have proven that the security controls that are offered by traditional VPN solutions (IPSEC VPN and SSL VPN) are not adequate anymore.
Current Challenges in Remote Access and Traditional VPN Solutions
-
Unauthorized user access and lack of least access privilege: One of the significant challenges that organizations face with a VPN solution is the fact that VPN is IP-based, often providing a user with a local address, as if they were physically on the network, to access any resource.
This access is unnecessarily broad, as an example an employee from the marketing department does not need visibility of financial accounting systems, it's utterly irrelevant to their role, and therefore considered a security risk of unauthorized information disclosure as the organization may store confidential or restricted data that should not be visible to any unauthorized user from another department. -
IP-based Access: Traditional VPN relies on IP addresses to provision network access; this is problematic as an IP address provides no contextual information about the user or device.
Therefore, it shouldn't be implicitly trusted, even if it is a local address or a VPN IP-Pool. User's IP addresses also change frequently with IP-Pool allocation, accessing services from multiple devices, including personal; managing access based on IP becomes challenging to operate and have in-depth visibility. - Endpoint Compliance: No endpoint security posture assessment is performed on the device that tries to establish a remote VPN connection. Just because a worker can prove their identity, this shouldn't vouch for the device's health. The endpoint could be harboring malware or connecting from their personal device, or there may be vulnerabilities such as an out-of-date OS, devices could also become compromised during a session.
- Risk Based Authentication Mechanism: VPN typically authenticate users using domain username and passwords. Multi-factor authentication is always recommended for remote access users. Traditional VPN solutions don’t facilitate for adaptive authentication which is risk-based. For example; if user is known but device is not an approved corporate device and geo-IP location is unknown and has not been previously profiled then access should be blocked as it could indicate a compromised credentials unless they can prove their authenticity through security questions.
- Vulnerability Management: Cyber-attacks that occurred recently have shown us that VPN solutions from security vendors are highly vulnerable. Numerous vulnerabilities and zero-day exploits have been reported. VPN solutions can be easily misconfigured, particularly when integrating with other technologies. Let us review the recent exploitation of vulnerabilities in SSL VPN products from several top-tier vendors;
- Cisco AnyConnect VPN
- Reference:https://www.cvedetails.com/vulnerability-list/vendor_id-16/product_id-20904/Cisco-Anyconnect-Secure-Mobility-Client.html
- Pulse Secure (Secure Connect) SSL VPN
- Reference: https://www.cvedetails.com/vulnerability-list/vendor_id-15824/product_id-33650/year-2020/Pulsesecure-Pulse-Connect-Secure.html
- FortiGate FortiOS SSL VPN
- CVE-2018-13379, CVE-2020-12812, CVE-2019-5591
- Citrix NetScaler
- CVE-2019-19781
- Citrix NetScaler vulnerability existing in Citrix Application Delivery Controller (ADC), Citrix Gateway, and Citrix SD-WAN WANOP appliances
- Palo Alto Global Protect
- CVE-2020-2050
Current Challenges in Remote Access and Traditional VPN Solutions
The challenges that the organizations face while having VPN connections are:
-
Unauthorized user access and lack of least access privilege: One of the significant challenges that organizations face with a VPN solution is the fact that VPN is IP-based, often providing a user with a local address, as if they were physically on the network, to access any resource.
This access is unnecessarily broad, as an example an employee from the marketing department does not need visibility of financial accounting systems, it's utterly irrelevant to their role, and therefore considered a security risk of unauthorized information disclosure as the organization may store confidential or restricted data that should not be visible to any unauthorized user from another department.
-
IP-based Access: Traditional VPN relies on IP addresses to provision network access; this is problematic as an IP address provides no contextual information about the user or device.
Therefore, it shouldn't be implicitly trusted, even if it is a local address or a VPN IP-Pool. User's IP addresses also change frequently with IP-Pool allocation, accessing services from multiple devices, including personal; managing access based on IP becomes challenging to operate and have in-depth visibility.
- Endpoint Compliance: No endpoint security posture assessment is performed on the device that tries to establish a remote VPN connection. Just because a worker can prove their identity, this shouldn't vouch for the device's health. The endpoint could be harboring malware or connecting from their personal device, or there may be vulnerabilities such as an out-of-date OS, devices could also become compromised during a session.
- Risk Based Authentication Mechanism: VPN typically authenticate users using domain username and passwords. Multi-factor authentication is always recommended for remote access users. Traditional VPN solutions don’t facilitate for adaptive authentication which is risk-based. For example; if user is known but device is not an approved corporate device and geo-IP location is unknown and has not been previously profiled then access should be blocked as it could indicate a compromised credentials unless they can prove their authenticity through security questions.
- Vulnerability Management: Cyber-attacks that occurred recently have shown us that VPN solutions from security vendors are highly vulnerable. Numerous vulnerabilities and zero-day exploits have been reported. VPN solutions can be easily misconfigured, particularly when integrating with other technologies. Let us review the recent exploitation of vulnerabilities in SSL VPN products from several top-tier vendors;
- Cisco AnyConnect VPN
- Reference:https://www.cvedetails.com/vulnerability-list/vendor_id-16/product_id-20904/Cisco-Anyconnect-Secure-Mobility-Client.html
- Pulse Secure (Secure Connect) SSL VPN
- Reference: https://www.cvedetails.com/vulnerability-list/vendor_id-15824/product_id-33650/year-2020/Pulsesecure-Pulse-Connect-Secure.html
- FortiGate FortiOS SSL VPN
- CVE-2018-13379, CVE-2020-12812, CVE-2019-5591
- Citrix NetScaler
- CVE-2019-19781
- Citrix NetScaler vulnerability existing in Citrix Application Delivery Controller (ADC), Citrix Gateway, and Citrix SD-WAN WANOP appliances
- Palo Alto Global Protect
- CVE-2020-2050
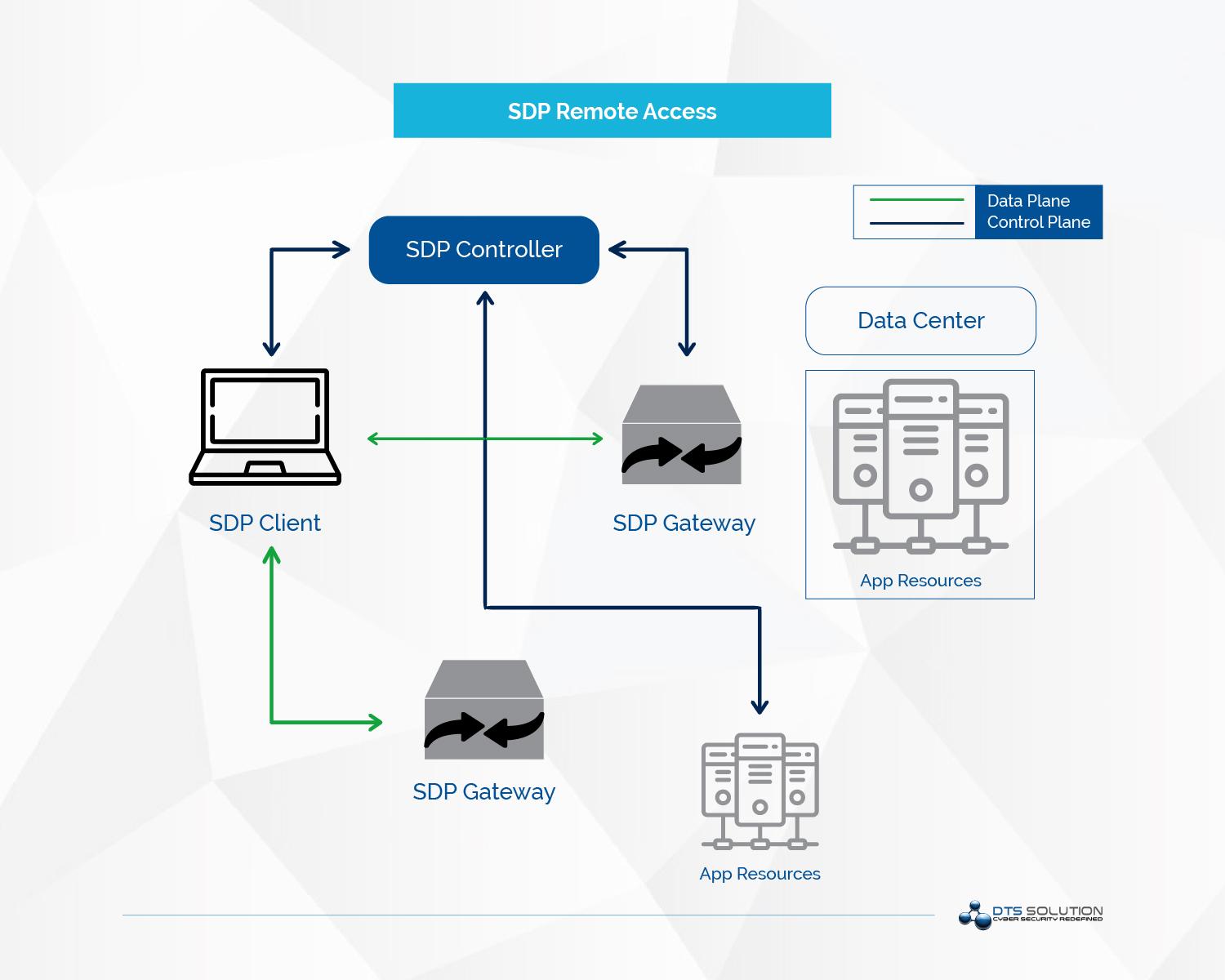
Paradigm Shift: Zero Trust Remote Access using Software Defined Perimeter
-
Risk-Assessment: One of the significant differentiators of SDP-based zero-trust network access over traditional VPN is that it allows contextual risk to be considered during the assessment of the network access request.
The use of adaptive or conditional access controls ensures that an endpoint complies with security policy and assesses other factors like geo-location and time of the request. This is particularly pertinent in the case of BYOD and unmanaged devices (as with third parties), where there is a lack of oversight of the device and no guarantees as to whether baseline security requirements are met. Furthermore, a user's session can be monitored in real-time, if the access policy requirements are no longer being met, access can be dynamically restricted - Risk-Based Identity and Access Management: SDP solutions integrate with IAM services to easily enforce users' identity policies used by the business elsewhere and ensure that each user is assigned the correct permissions for their function and role. The use of Single Packet Authentication (SPA) requires the identity of the user before brokering access to the requested service, so only connection attempts from authorized users are recognized, making applications hidden to everyone else.
-
Vulnerability and Patch Management: With SDP, the burden of infrastructure maintenance sits with the service provider, they are responsible for making sure that any vulnerabilities are patched immediately. Being an overlay technology, the configuration is far simpler and can be neatly integrated with existing technologies like UEBA, SIEM, SOAR, IAM, and so on through the use of APIs.
As access policies are formed and applied based on a user and device identity, administrators can be far more precise about access and apply consistently across devices, platforms, and whether the end-user is sitting in the office or working remotely. -
User and Device Identity-Centric Approach: SDP moves away from a network-centric approach, creating an isolated, private tunnel between each user and application, avoiding the need to configure firewall policies or ACLs.
As SDP is user and device identity-centric, least privilege access can be enforced based on the user's permissions universally due to a centralized policy engine. Rather than providing access to the underlying network, users are routed to the application. This ultimately removes the network location point as a position of advantage and eliminates the excessive implicit trust that IP addresses offer.
Paradigm Shift: Zero Trust Remote Access using Software Defined Perimeter
To address the challenges mentioned above and efficiently eliminating the inherent risks posed by traditional VPN solutions, it is recommended to enhance the control and implement a more modern and secure approach to ensure control over remote user access. In comes Software-Defined Perimeter (SDP), a sophisticated new approach to provide zero-trust secure remote access which combines continuous posture monitoring, user and device validation and seamless network resource access in a frictionless manner across a multi-cloud and on-premises environment.
-
Risk-Assessment: One of the significant differentiators of SDP-based zero-trust network access over traditional VPN is that it allows contextual risk to be considered during the assessment of the network access request.
The use of adaptive or conditional access controls ensures that an endpoint complies with security policy and assesses other factors like geo-location and time of the request. This is particularly pertinent in the case of BYOD and unmanaged devices (as with third parties), where there is a lack of oversight of the device and no guarantees as to whether baseline security requirements are met. Furthermore, a user's session can be monitored in real-time, if the access policy requirements are no longer being met, access can be dynamically restricted
- Risk-Based Identity and Access Management: SDP solutions integrate with IAM services to easily enforce users' identity policies used by the business elsewhere and ensure that each user is assigned the correct permissions for their function and role. The use of Single Packet Authentication (SPA) requires the identity of the user before brokering access to the requested service, so only connection attempts from authorized users are recognized, making applications hidden to everyone else.
-
Vulnerability and Patch Management: With SDP, the burden of infrastructure maintenance sits with the service provider, they are responsible for making sure that any vulnerabilities are patched immediately. Being an overlay technology, the configuration is far simpler and can be neatly integrated with existing technologies like UEBA, SIEM, SOAR, IAM, and so on through the use of APIs.
As access policies are formed and applied based on a user and device identity, administrators can be far more precise about access and apply consistently across devices, platforms, and whether the end-user is sitting in the office or working remotely.
-
User and Device Identity-Centric Approach: SDP moves away from a network-centric approach, creating an isolated, private tunnel between each user and application, avoiding the need to configure firewall policies or ACLs.
As SDP is user and device identity-centric, least privilege access can be enforced based on the user's permissions universally due to a centralized policy engine. Rather than providing access to the underlying network, users are routed to the application. This ultimately removes the network location point as a position of advantage and eliminates the excessive implicit trust that IP addresses offer.
See also: