AWS Security Assessment
- Compute
- Storage
- Database
- Migration
- Network and Content Delivery
- Management Tools
- Security & Identity Compliance
- Messaging
AWS Security Assessment
- Compute
- Storage
- Database
- Migration
- Network and Content Delivery
- Management Tools
- Security & Identity Compliance
- Messaging
Why AWS Security Assessment is different than VAPT Engagement?
- AWS EC2 instance excluding tactics related to disruption of business continuity such as launching Denial of Service (DOS) attacks
- The implementation and configuration of Vendor Operated Services,
- AWS services such as Cloudfront and the API Gateway configuration may be pentested but the hosting infrastructure is off limits.
- Areas of the AWS Elastic Cloud Computing (EC2) service including:
- The Application Programming Interface (API) (e.g. HTTP/HTTPS)
- Various Web and mobile applications that hosted by your organization
- The application server and associated stack (e.g. programming languages such Python, React)
- Virtual machines and operating systems
- Testing S3 bucket configuration and permissions flaws
- Targeting and compromising AWS IAM keys
- Cloudfront/WAF Misconfiguration Bypasses
- Establishing private-cloud access through Lambda backdoor functions
- Cover tracks by obfuscating CloudTrail logs
Why AWS Security Assessment is different than VAPT Engagement?
- AWS EC2 instance excluding tactics related to disruption of business continuity such as launching Denial of Service (DOS) attacks
- The implementation and configuration of Vendor Operated Services,
- AWS services such as Cloudfront and the API Gateway configuration may be pentested but the hosting infrastructure is off limits.
- Areas of the AWS Elastic Cloud Computing (EC2) service including:
- The Application Programming Interface (API) (e.g. HTTP/HTTPS)
- Various Web and mobile applications that hosted by your organization
- The application server and associated stack (e.g. programming languages such Python, React)
- Virtual machines and operating systems
- Testing S3 bucket configuration and permissions flaws
- Targeting and compromising AWS IAM keys
- Cloudfront/WAF Misconfiguration Bypasses
- Establishing private-cloud access through Lambda backdoor functions
- Cover tracks by obfuscating CloudTrail logs
- Defining the scope, including the AWS environment and target systems
- Run your own preliminary
- Determine the type of pentest you would like conducted (e.g. black box, white box, gray box)
- Outline expectations for both internal stakeholders and the pentesting company
- Establishing a timeline for the technical assessment to occur, receive formal reports, and potential remediation and follow-up testing
- Developing the protocol and rules of engagement if the pentest reveals the client may already have been breached or is under an ongoing (live) attack
- Obtaining written approval to conduct the test by the client (and other third parties that may be involved)
DevSecOps Pipelines Considerations in AWS
- Cloud9 SDK which is a cloud-based IDE where you can write, run and debug your code from a browser.
- AWS CodeCommit is a fully-managed source control service that hosts secure Git-based repositories. It makes it easy for teams to collaborate on code in a secure and highly scalable ecosystem.
- AWS CodeBuild is a service where developers can compile their source code , perform integration from multiple SCMs and create build artifacts.
- AWS S3 buckets are used for storing the final build artifacts and binaries.
- AWS CodeDeploy is a service that pulls the binary artifacts from S3 buckets and deploys them in pre-provisioned AWS environments like EC2, ElasticBeanstalk and ECS.
- Finally, we have the AWS CodePipeline which orchestrates the various builds and deploy stages defined in CodeBuild and CodeDeploy giving you a fully managed continuous delivery service.
These tools will be needed to be updated regularly for which we can employ a Lambda function which would periodically check for new versions. If the tool is compatible with the AWS Lambda specifications, then converting the tool as a Lambda service would be an exceptionally great task and for vulnerability management. Refer to “Tools” section for suitable tools.
DevSecOps Pipelines Considerations in AWS
- Cloud9 SDK which is a cloud-based IDE where you can write, run and debug your code from a browser.
- AWS CodeCommit is a fully-managed source control service that hosts secure Git-based repositories. It makes it easy for teams to collaborate on code in a secure and highly scalable ecosystem.
- AWS CodeBuild is a service where developers can compile their source code , perform integration from multiple SCMs and create build artifacts.
- AWS S3 buckets are used for storing the final build artifacts and binaries.
- AWS CodeDeploy is a service that pulls the binary artifacts from S3 buckets and deploys them in pre-provisioned AWS environments like EC2, ElasticBeanstalk and ECS.
- Finally, we have the AWS CodePipeline which orchestrates the various builds and deploy stages defined in CodeBuild and CodeDeploy giving you a fully managed continuous delivery service.
These tools will be needed to be updated regularly for which we can employ a Lambda function which would periodically check for new versions. If the tool is compatible with the AWS Lambda specifications, then converting the tool as a Lambda service would be an exceptionally great task and for vulnerability management. Refer to “Tools” section for suitable tools.
Threat Landscape in AWS DevOps Environment
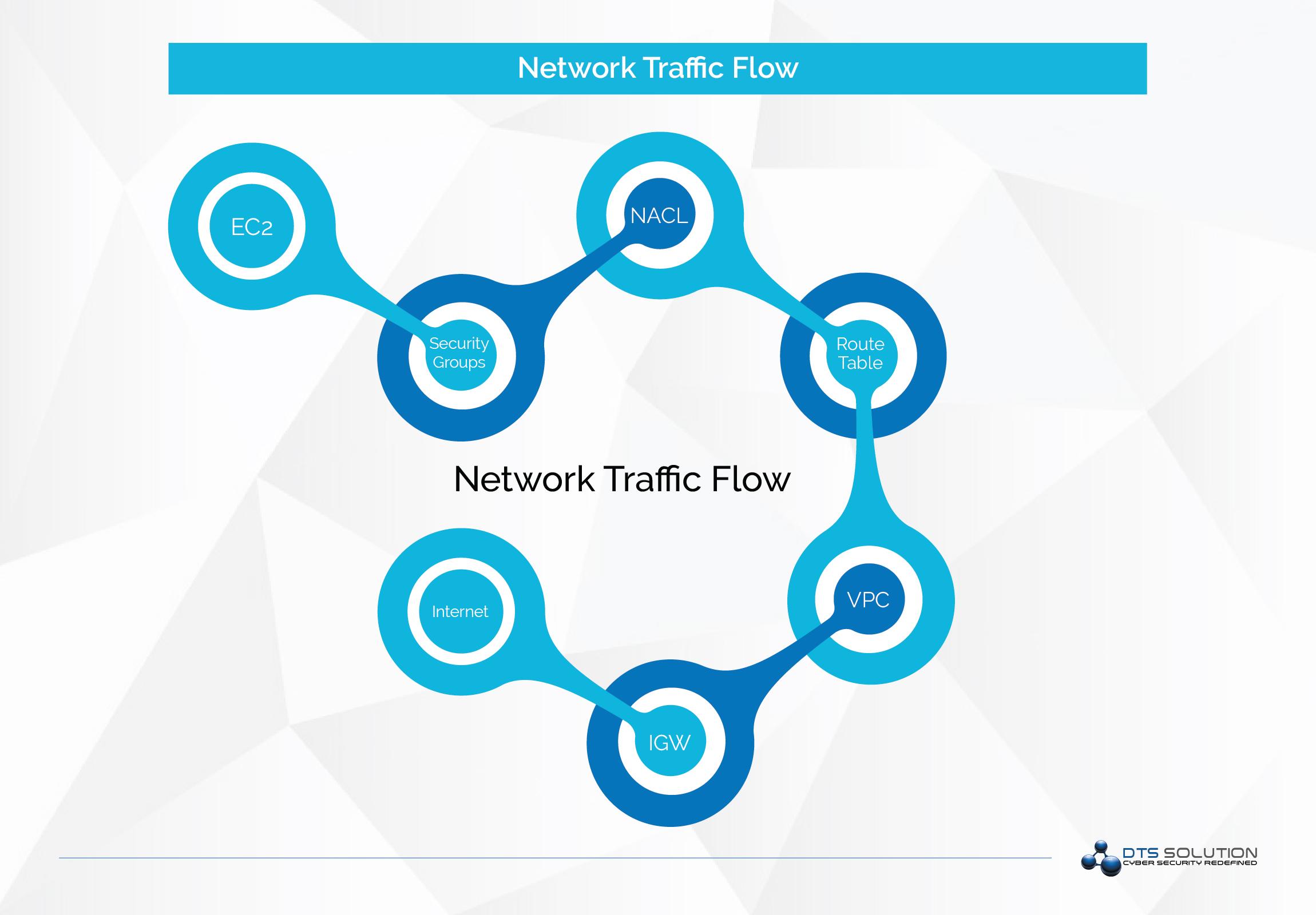
The diagram on the right shows a typical flow of network traffic and the different places where it can be tapped. Security Groups are like host-based firewalls for individual EC2 instances. Network Access Control Lists (NACL) can be configured for a group of EC2 instances. Route Tables are configured for routing traffic amongst different networks and finally we have VPC’s which are the final overarching network segmentation module connected to an Internet Gateway.
It is very much possible to have misconfiguration in such complex infrastructure.
| Tool | Category | Description |
|---|---|---|
| AWS CloudWatch | Logging and Monitoring |
|
| AWS CloudTrail | Logging and Auditing |
|
| AWS Config | Compliance and Configuration Management |
|
| AWS Inspector | Security and Compliance |
|
| Prowler | Security Hardening |
|
| Security Monkey | Configuration Management |
|
| ScoutSuite | Security and Compliance |
|
| AWS Secrets Manager | Secrets Management |
|
| AWS WAF | Firewall |
|
- If an application deployed on an EC2 instance is having an RCE or an SSRF vulnerability then an attacker can request the URL, obtain the AWS Access Keys and gain access to all available AWS resources.
- Accidentally committing source code containing the AWS Keys, exposed in publicly accessible folders etc.
- Archery, Open source vulnerability assessment and management tool which can be utilized in a DevOps CI/CD environment
- AWS Recipes by NCCGroup, helpful CloudFront and IAM templates and policies to lock down your environment
Threat Landscape in AWS DevOps Environment
The diagram on the right shows a typical flow of network traffic and the different places where it can be tapped. Security Groups are like host-based firewalls for individual EC2 instances. Network Access Control Lists (NACL) can be configured for a group of EC2 instances. Route Tables are configured for routing traffic amongst different networks and finally we have VPC’s which are the final overarching network segmentation module connected to an Internet Gateway.
It is very much possible to have misconfiguration in such complex infrastructure.
| Tool | Category | Description |
|---|---|---|
| AWS CloudWatch | Logging and Monitoring |
|
| AWS CloudTrail | Logging and Auditing |
|
| AWS Config | Compliance and Configuration Management |
|
| AWS Inspector | Security and Compliance |
|
| Prowler | Security Hardening |
|
| Security Monkey | Configuration Management |
|
| ScoutSuite | Security and Compliance |
|
| AWS Secrets Manager | Secrets Management |
|
| AWS WAF | Firewall |
|
- If an application deployed on an EC2 instance is having an RCE or an SSRF vulnerability then an attacker can request the URL, obtain the AWS Access Keys and gain access to all available AWS resources.
- Accidentally committing source code containing the AWS Keys, exposed in publicly accessible folders etc.
- Archery, Open source vulnerability assessment and management tool which can be utilized in a DevOps CI/CD environment
-
AWS Recipes by NCCGroup, helpful CloudFront and IAM templates and policies to lock down your environment
AWS Security benchmark by AWSLabs, contains benchmark governance rules
See also: