Taking on the role of Chief Information Security Officer (CISO) is an exciting yet challenging step in a career, especially when one steps into the position either internally or from outside the organization. The first 100 days are critical for establishing trust, understanding the organization, building relationships, and beginning to align security strategy with business objectives. This guide offers a structured approach, with practical steps and a fictitious example, for making the most of those first 100 days.
Taking on the role of Chief Information Security Officer (CISO) is an exciting yet challenging step in a career, especially when one steps into the position either internally or from outside the organization. The first 100 days are critical for establishing trust, understanding the organization, building relationships, and beginning to align security strategy with business objectives. This guide offers a structured approach, with practical steps and a fictitious example, for making the most of those first 100 days.
Phase 1: Prepare Before You Begin (Days -10 to 0)
Before officially stepping into your role, preparation is key. This includes doing your homework on the organization, understanding its culture, and determining what leadership expects from you.
Steps for Preparation:
- Interview Your Predecessor (if applicable): If your predecessor is still available, schedule an interview to gather insights about their experience, challenges, and what worked for them. Use this opportunity to understand the legacy you’re inheriting. Key questions to ask may include:
- What are the current security risks and challenges?
- How is the security team structured, and what gaps exist?
- What projects are in progress or need immediate attention?
For example, a newly appointed CISO, interviewed his/her predecessor, who was still part of the company in a different role. The conversation revealed key details about ongoing security projects, vendor contracts, and areas where quick wins could be achieved.
2. Understand the Corporate Structure: Familiarize yourself with the company’s organizational structure. Identify key influencers, collaborators, and stakeholders, including the CIO, CEO, board members, and heads of business divisions. Understanding the reporting lines will clarify who influences decision-making and who you will collaborate with to drive security initiatives
3. Gather Company Documentation: Ask for relevant internal documentation such as financial reports, town hall notes, and internal newsletters to familiarize yourself with the business’s strategic priorities or security-related records. Review these to gain a high-level understanding of the company’s business model, strategy, and current state of its security posture.
4. Draft an Introduction Memo: Create a one-page introduction about yourself, including your background, approach to security, and vision for your role. Include this in a memo to send out on your first day to make an immediate connection with your new colleagues.
Deliverables by Day 0:
- A clear understanding of the company’s culture, leadership structure, and key influencers.
- Basic knowledge of existing security policies and frameworks.
Phase 1: Prepare Before You Begin (Days -10 to 0)
Before officially stepping into your role, preparation is key. This includes doing your homework on the organization, understanding its culture, and determining what leadership expects from you.
Steps for Preparation:
- Interview Your Predecessor (if applicable): If your predecessor is still available, schedule an interview to gather insights about their experience, challenges, and what worked for them. Use this opportunity to understand the legacy you’re inheriting. Key questions to ask may include:
- What are the current security risks and challenges?
- How is the security team structured, and what gaps exist?
- What projects are in progress or need immediate attention?
For example, a newly appointed CISO, interviewed his/her predecessor, who was still part of the company in a different role. The conversation revealed key details about ongoing security projects, vendor contracts, and areas where quick wins could be achieved.
2. the Corporate Structure: Familiarize yourself with the company’s organizational structure. Identify key influencers, collaborators, and stakeholders, including the CIO, CEO, board members, and heads of business divisions. Understanding the reporting lines will clarify who influences decision-making and who you will collaborate with to drive security initiatives
3. Gather Company Documentation: Ask for relevant internal documentation such as financial reports, town hall notes, and internal newsletters to familiarize yourself with the business’s strategic priorities or security-related records. Review these to gain a high-level understanding of the company’s business model, strategy, and current state of its security posture.
4. Draft an Introduction Memo: Create a one-page introduction about yourself, including your background, approach to security, and vision for your role. Include this in a memo to send out on your first day to make an immediate connection with your new colleagues.
Deliverables by Day 0:
- A clear understanding of the company’s culture, leadership structure, and key influencers.
- Basic knowledge of existing security policies and frameworks.
Phase 2: Building Relationships (Days 1 to 30)
The first month should be spent building relationships and trust within the organization. Much of your success as a CISO will depend on your ability to collaborate with various stakeholders and create alliances, especially with those beyond the IT and security teams.
Steps to Building Relationships:
- Meet the Team: Set up one-on-one meetings with your direct reports, including security team members and IT staff. This will give you an understanding of their skill sets, goals, and potential gaps within the team. Be transparent about your own leadership style and share your expectations.
According to the earlier example, in the first week, a CISO met with their security team, and through these meetings, they realized that while their team was technically strong, they lacked strategic alignment with the business objectives.
- Connect with Business Leaders: Meet key business leaders and department heads. Ask them about their biggest challenges, security concerns, and expectations of the CISO role. These meetings are more about listening than speaking; Your goal is to understand how security fits into their workflows and identify areas where security can support the business more effectively.
- Build Your Sphere of Influence: Identify influencers both within and outside the organization. Some may not have direct authority but can impact the perception of your department or the adoption of security initiatives.
Example Scenario:
A newly appointed CISO at a mid-sized healthcare company might prioritize relationships with the clinical leadership and compliance teams. During stakeholder interviews, they may uncover gaps in securing patient data, identify concerns about phishing attacks targeting medical staff, and discover potential third-party risks from service providers. Understanding these concerns early on will shape the next steps in the security strategy.
Deliverables by Day 30:
- A clear map of your relationships within the organization.
- Insights into how the business perceives security and what it expects from the CISO role.
- An understanding of the security team’s capabilities and gaps.
Phase 2: Building Relationships (Days 1 to 30)
The first month should be spent building relationships and trust within the organization. Much of your success as a CISO will depend on your ability to collaborate with various stakeholders and create alliances, especially with those beyond the IT and security teams.
Steps to Building Relationships:
- Meet the Team: Set up one-on-one meetings with your direct reports, including security team members and IT staff. This will give you an understanding of their skill sets, goals, and potential gaps within the team. Be transparent about your own leadership style and share your expectations.
According to the earlier example, in the first week, a CISO met with their security team, and through these meetings, they realized that while their team was technically strong, they lacked strategic alignment with the business objectives.
- Connect with Business Leaders: Meet key business leaders and department heads. Ask them about their biggest challenges, security concerns, and expectations of the CISO role. These meetings are more about listening than speaking; Your goal is to understand how security fits into their workflows and identify areas where security can support the business more effectively.
- Build Your Sphere of Influence: Identify influencers both within and outside the organization. Some may not have direct authority but can impact the perception of your department or the adoption of security initiatives.
Example Scenario:
A newly appointed CISO at a mid-sized healthcare company might prioritize relationships with the clinical leadership and compliance teams. During stakeholder interviews, they may uncover gaps in securing patient data, identify concerns about phishing attacks targeting medical staff, and discover potential third-party risks from service providers. Understanding these concerns early on will shape the next steps in the security strategy.
Deliverables by Day 30:
- A clear map of your relationships within the organization.
- Insights into how the business perceives security and what it expects from the CISO role.
- An understanding of the security team’s capabilities and gaps.
Phase 3: Inventory Business Components (Days 30 to 45)
The next step is to gather information on the organization’s assets—both technical and non-technical. Understanding the critical elements of the business is key to developing a solid security strategy.
Steps for Inventorying Business Components:
- Inventory Company Assets: This includes people, processes, technology, and data. Collect information on the company’s critical infrastructure, applications, and databases. This inventory will help you understand what you need to protect.
- Evaluate Existing Security Policies: Review the organization’s security policies, processes, and standards. Pay attention to gaps, outdated documents, and areas where policies may not align with the current business model.
- Assess Team Skill Sets: Evaluate the technical and soft skills of your security team. Identify any gaps in expertise and start planning for necessary training or hiring needs to ensure the team is capable of handling the company’s security requirements.
- Audit Security Tools: Understand the tools in place for managing security operations, such as firewalls, SIEM systems, and endpoint protection. Are they still effective? Do they need upgrades or replacements?
5. Review Third-Party Contracts: Many organizations rely on third-party vendors for critical functions. Review contracts and security-related clauses to ensure the right safeguards are in place, especially in cases of sensitive data or critical infrastructure.
Example Output:
At the 45-day mark, the CISO should produce a comprehensive report listing critical business assets, associated risks, and team capabilities. For instance, the CISO at the aforementioned healthcare company might identify that the company relies on outdated encryption protocols for securing patient information. They may also realize that their security staff lacks expertise in modern cloud security tools, necessitating external training or hiring additional staff.
Deliverables by Day 45:
- A complete inventory of critical assets, technologies, and processes.
- A summary of gaps in existing policies or processes.
- Identification of high-risk areas or legacy systems that need immediate attention.
Phase 3: Inventory Business Components (Days 30 to 45)
The next step is to gather information on the organization’s assets—both technical and non-technical. Understanding the critical elements of the business is key to developing a solid security strategy.
Steps for Inventorying Business Components:
- Inventory Company Assets: This includes people, processes, technology, and data. Collect information on the company’s critical infrastructure, applications, and databases. This inventory will help you understand what you need to protect.
- Evaluate Existing Security Policies: Review the organization’s security policies, processes, and standards. Pay attention to gaps, outdated documents, and areas where policies may not align with the current business model.
- Assess Team Skill Sets: Evaluate the technical and soft skills of your security team. Identify any gaps in expertise and start planning for necessary training or hiring needs to ensure the team is capable of handling the company’s security requirements.
- Audit Security Tools: Understand the tools in place for managing security operations, such as firewalls, SIEM systems, and endpoint protection. Are they still effective? Do they need upgrades or replacements?
- Review Third-Party Contracts: Many organizations rely on third-party vendors for critical functions. Review contracts and security-related clauses to ensure the right safeguards are in place, especially in cases of sensitive data or critical infrastructure.
Example Output:
At the 45-day mark, the CISO should produce a comprehensive report listing critical business assets, associated risks, and team capabilities. For instance, the CISO at the aforementioned healthcare company might identify that the company relies on outdated encryption protocols for securing patient information. They may also realize that their security staff lacks expertise in modern cloud security tools, necessitating external training or hiring additional staff.
Deliverables by Day 45:
- A complete inventory of critical assets, technologies, and processes.
- A summary of gaps in existing policies or processes.
- Identification of high-risk areas or legacy systems that need immediate attention.
Phase 4: Assessing Security Posture (Days 45 to 80)
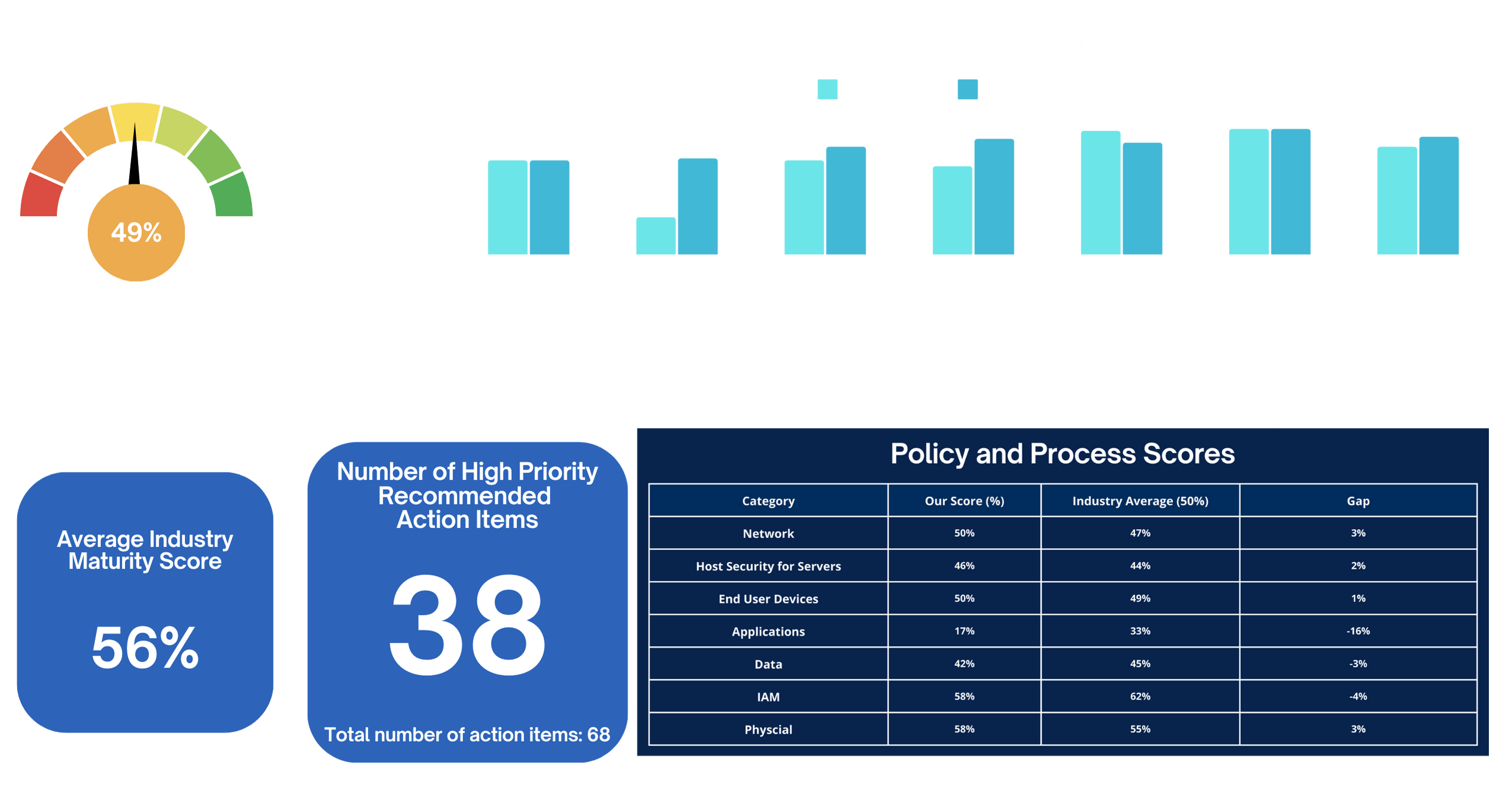
By now, you should have a good understanding of the business, its assets, and potential risks. This is where you will focus on conducting a thorough assessment of the current security posture and comparing it to industry benchmarks.
Steps to Assess Security Posture:
- Perform a Security Gap Analysis: Use frameworks such as ISO 27001, NIST, COBIT, or CIS to assess the current state of the organization’s security posture. Identify areas of strength and areas that need improvement.
- Benchmark Against Industry Standards: Compare the organization’s security practices with industry standards. This can include best practices in threat detection, incident response, and compliance with regulations like GDPR. This benchmarking will reveal where you stand in terms of best practices and help you identify areas that need improvement.
- Conduct Risk Assessments: Assess the company’s vulnerability to various risks, including cyberattacks, data breaches, and third-party vulnerabilities. Involve external auditors or consultants if necessary to ensure an unbiased evaluation.
- Engage the Security Diagnostic Program (if available): Use diagnostic tools to evaluate business satisfaction with security. This can help highlight areas where security may be causing friction for users or where the business may have unrealistic expectations.
Deliverables by Day 80:
- A comprehensive security posture report detailing strengths, weaknesses, and areas of improvement.
- Risk assessments for critical areas, along with potential mitigation strategies.
- Benchmarking data to justify future investments in security.
Phase 4: Assessing Security Posture (Days 45 to 80)

By now, you should have a good understanding of the business, its assets, and potential risks. This is where you will focus on conducting a thorough assessment of the current security posture and comparing it to industry benchmarks.
Steps to Assess Security Posture:
- Perform a Security Gap Analysis: Use frameworks such as ISO 27001, NIST, COBIT, or CIS to assess the current state of the organization’s security posture. Identify areas of strength and areas that need improvement.
- Benchmark Against Industry Standards: Compare the organization’s security practices with industry standards. This can include best practices in threat detection, incident response, and compliance with regulations like GDPR. This benchmarking will reveal where you stand in terms of best practices and help you identify areas that need improvement.
- Conduct Risk Assessments: Assess the company’s vulnerability to various risks, including cyberattacks, data breaches, and third-party vulnerabilities. Involve external auditors or consultants if necessary to ensure an unbiased evaluation.
- Engage the Security Diagnostic Program (if available): Use diagnostic tools to evaluate business satisfaction with security. This can help highlight areas where security may be causing friction for users or where the business may have unrealistic expectations.
Deliverables by Day 80:
- A comprehensive security posture report detailing strengths, weaknesses, and areas of improvement.
- Risk assessments for critical areas, along with potential mitigation strategies.
- Benchmarking data to justify future investments in security.
Phase 5: Deliver the Plan (Days 80 to 100)
The final phase involves consolidating everything you’ve learned and turning it into an actionable security plan that aligns with business objectives. This is where you present your findings and proposed strategies to key stakeholders.
Steps to Delivering the Plan:
1. Develop a High-Level Security Strategy: Based on your assessments, develop a high-level strategy that addresses the organization’s key security risks while aligning with business goals. Ensure that this strategy covers not just technical solutions but also governance, processes, and personnel requirements.
2. Build the Executive Presentation: Create a presentation for executives and key stakeholders. Focus on aligning security goals with business objectives, highlighting potential risks, and justifying the need for future investments in security infrastructure. Be sure to include measurable outcomes and timelines.
Example: In a CISO’s presentation to the board, the CISO showcased their security strategy using the following data:
- Risk exposure: They highlighted that 45% of critical systems were vulnerable due to outdated patch management.
- Strategic alignment: They proposed a roadmap that included updating legacy systems, improving IAM, and conducting quarterly risk assessments.
- Budget projection: The CISO presented a budget of $500,000 for the next 12 months, with $200,000 earmarked for legacy system upgrades.
3. Communicate Your Strategy: Present the security roadmap to your executive stakeholders. Explain the need for each initiative, whether it’s updating outdated policies, implementing new tools, or addressing skills gaps.
Ensure that you have the buy-in from all relevant stakeholders, including executives, department heads, and key business leaders. Tailor your communication to each group’s priorities to gain their support—highlighting how your strategy will reduce risks, ensure compliance, and enable growth.
4. Communicate Key Security Metrics: Establish and communicate the security metrics that will be used to measure success. This could include incident response times, vulnerability remediation times, or security audit scores.
Final Scenario:
Imagine that the CISO at the healthcare company presents a detailed plan to the board, including a budget breakdown for updating encryption protocols, training staff, and upgrading outdated tools. The plan outlines an improvement in the company’s security maturity score from 65 to 80 within the next year, which aligns with the business goal of securing patient data as they expand their operations into new regions.
Deliverables by Day 100:
- A high-level security strategy that aligns with business goals.
- An executive presentation outlining the strategy, key risks, and budget requirements.
- Agreement from stakeholders on the security roadmap for the next 12 months.
Phase 5: Deliver the Plan (Days 80 to 100)

The final phase involves consolidating everything you’ve learned and turning it into an actionable security plan that aligns with business objectives. This is where you present your findings and proposed strategies to key stakeholders.
Steps to Delivering the Plan:
- Develop a High-Level Security Strategy: Based on your assessments, develop a high-level strategy that addresses the organization’s key security risks while aligning with business goals. Ensure that this strategy covers not just technical solutions but also governance, processes, and personnel requirements.
- Build the Executive Presentation: Create a presentation for executives and key stakeholders. Focus on aligning security goals with business objectives, highlighting potential risks, and justifying the need for future investments in security infrastructure. Be sure to include measurable outcomes and timelines.
Example: In a CISO’s presentation to the board, the CISO showcased their security strategy using the following data:
- Risk exposure: They highlighted that 45% of critical systems were vulnerable due to outdated patch management.
- Strategic alignment: They proposed a roadmap that included updating legacy systems, improving IAM, and conducting quarterly risk assessments.
- Budget projection: The CISO presented a budget of $500,000 for the next 12 months, with $200,000 earmarked for legacy system upgradess.
3. Communicate Your Strategy: Present the security roadmap to your executive stakeholders. Explain the need for each initiative, whether it’s updating outdated policies, implementing new tools, or addressing skills gaps. Ensure that you have the buy-in from all relevant stakeholders, including executives, department heads, and key business leaders. Tailor your communication to each group’s priorities to gain their support—highlighting how your strategy will reduce risks, ensure compliance, and enable growth.
4. Communicate Key Security Metrics: Establish and communicate the security metrics that will be used to measure success. This could include incident response times, vulnerability remediation times, or security audit scores.
Final Scenario:
Imagine that the CISO at the healthcare company presents a detailed plan to the board, including a budget breakdown for updating encryption protocols, training staff, and upgrading outdated tools. The plan outlines an improvement in the company’s security maturity score from 65 to 80 within the next year, which aligns with the business goal of securing patient data as they expand their operations into new regions.
Deliverables by Day 100:
- A high-level security strategy that aligns with business goals.
- An executive presentation outlining the strategy, key risks, and budget requirements.
- Agreement from stakeholders on the security roadmap for the next 12 months.
Expected Improvements and Tentative Plan Results
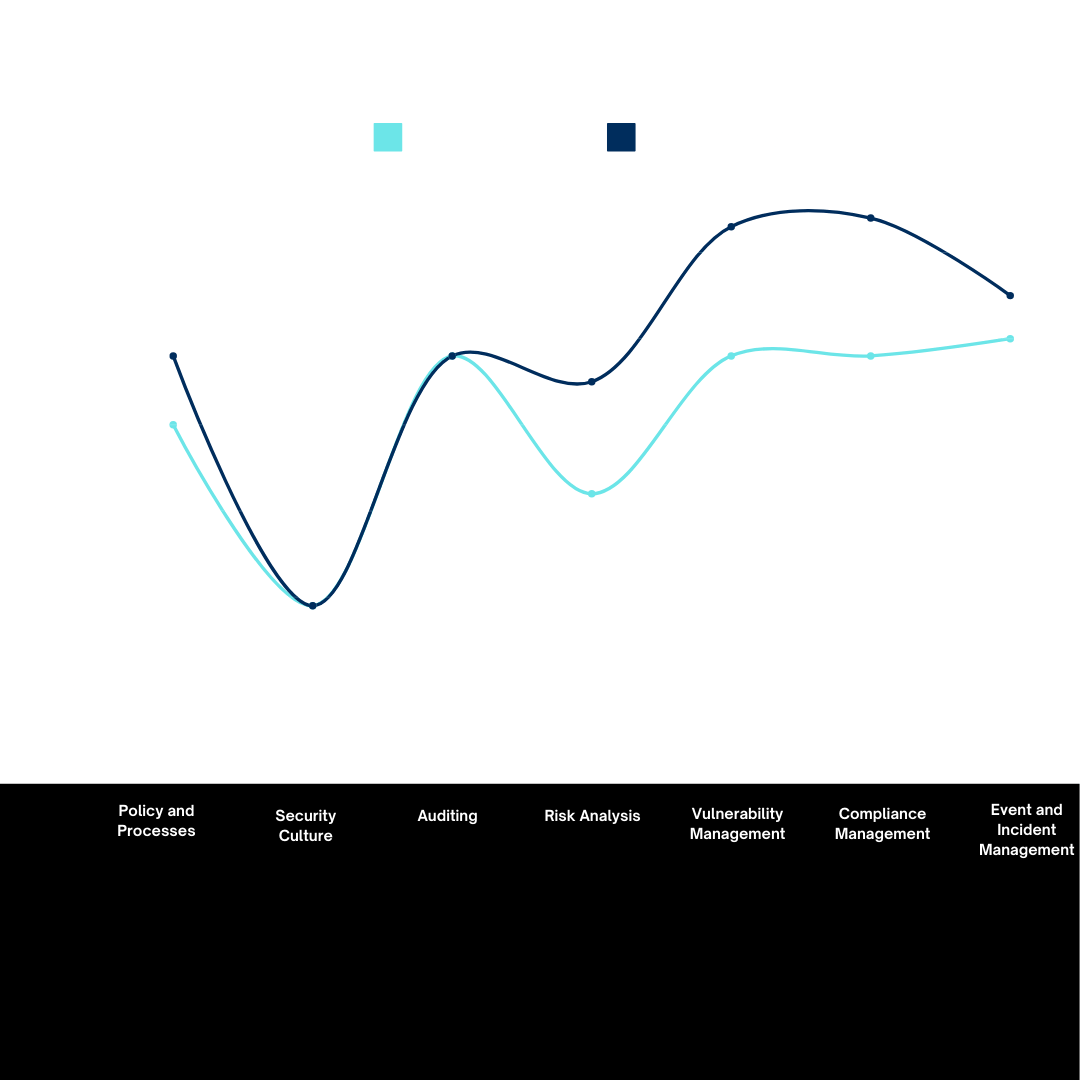
Upon completing the 100 days, based on your strategy and 100-day plan, the output results can be significant in shaping the security posture and business alignment of the organization. These outcomes could come in both tangible and intangible aspects including:
- Overall Security Maturity Improvement
- Enhanced Risk Management and Mitigation
- Incident Response and Monitoring Improvements
- Security Team Upskilling and Alignment
- Governance, Policy, and Compliance Readiness
- Executive and Stakeholder Engagement
- Tangible Security Metrics and Continuous Monitoring
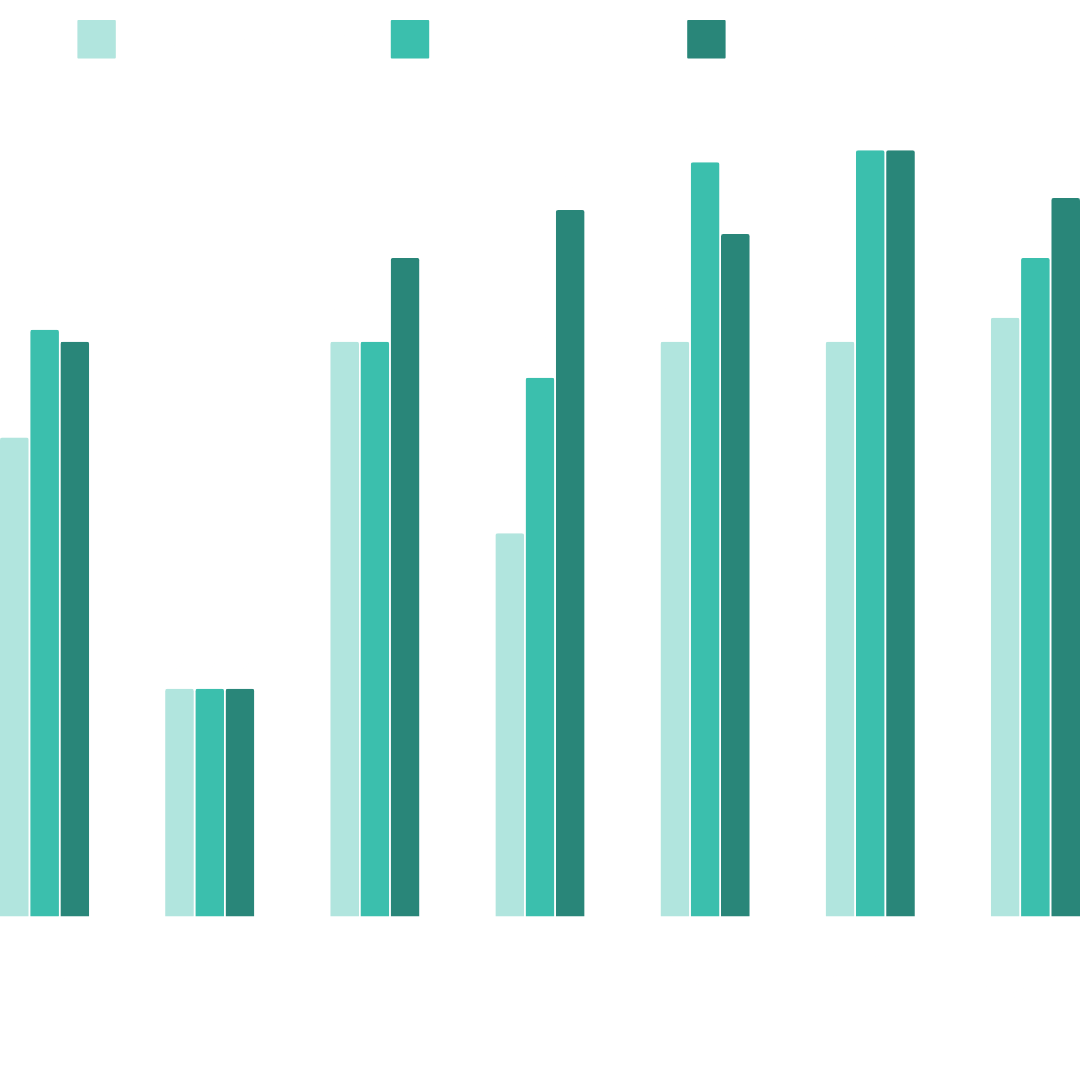
Expected Improvements and Tentative Plan Results


Upon completing the 100 days, based on your strategy and 100-day plan, the output results can be significant in shaping the security posture and business alignment of the organization. These outcomes could come in both tangible and intangible aspects including:
- Overall Security Maturity Improvement
- Enhanced Risk Management and Mitigation
- Incident Response and Monitoring Improvements
- Security Team Upskilling and Alignment
- Governance, Policy, and Compliance Readiness
- Executive and Stakeholder Engagement
- Tangible Security Metrics and Continuous Monitoring

Conclusion: Looking Beyond the First 100 Days
The first 100 days as a CISO are crucial for setting the tone of your leadership and building the foundation for a robust security strategy. While this article has laid out a roadmap, the real work begins after this initial period. A successful CISO will continue to refine strategies, build stronger relationships, and adapt to the ever-changing cybersecurity landscape.
By following the structured approach outlined here—preparation, relationship building, inventorying business components, assessing security posture, and delivering a strategic plan—new CISOs can confidently lead their organizations to a more secure future.
The examples demonstrate how CISOs can apply this methodology, evaluate risks, and secure the necessary budget to strengthen their organization’s security posture. Ultimately, these 100 days serve as a launchpad for long-term success in the role.
Conclusion: Looking Beyond the First 100 Days
The first 100 days as a CISO are crucial for setting the tone of your leadership and building the foundation for a robust security strategy. While this article has laid out a roadmap, the real work begins after this initial period. A successful CISO will continue to refine strategies, build stronger relationships, and adapt to the ever-changing cybersecurity landscape.
By following the structured approach outlined here—preparation, relationship building, inventorying business components, assessing security posture, and delivering a strategic plan—new CISOs can confidently lead their organizations to a more secure future.
The examples demonstrate how CISOs can apply this methodology, evaluate risks, and secure the necessary budget to strengthen their organization’s security posture. Ultimately, these 100 days serve as a launchpad for long-term success in the role.
See also:

