Summary

Introduction and Facts
- Creeper was the first known computer virus and it targeted TENEX OS back in 1971.
- Ray Tomlinson created what people believed the first antivirus to delete Creeper.
- Executables can be infected without getting their size nor functionality altered.
- NextGen antiviruses miss the obvious with high rate of false-positive detections.
- Malwares adapt an average of ten evasion techniques apart from sophistication.
- Antiviruses nowadays became dead and useless regardless the vendor or technology.
" What you just pull code from Rapid9 or some sh*t? since when did you become a script kiddie? "Elliot on Mr. Robot
Bypassing Signature-Based Detection
Binary execution is one of the most reliable ways to compromise a system but not the most covert one since executables are suspicious by reputation also antiviruses and other host security controls will always inspect them for malicious functions by signature and/or behavior.
Summary

In this presentation I will explain how modern antiviruses really work, how easily to trick and bypass them from the lowest possible level, I will also highlight the process of manually injecting the most evil payloads in the most innocent files while bypassing the most strict security controls.
Introduction and Facts
- Creeper was the first known computer virus and it targeted TENEX OS back in 1971.
- Ray Tomlinson created what people believed the first antivirus to delete Creeper.
- Executables can be infected without getting their size nor functionality altered.
- NextGen antiviruses miss the obvious with high rate of false-positive detections.
- Malwares adapt an average of ten evasion techniques apart from sophistication.
-
Antiviruses nowadays became dead and useless regardless the vendor or technology.
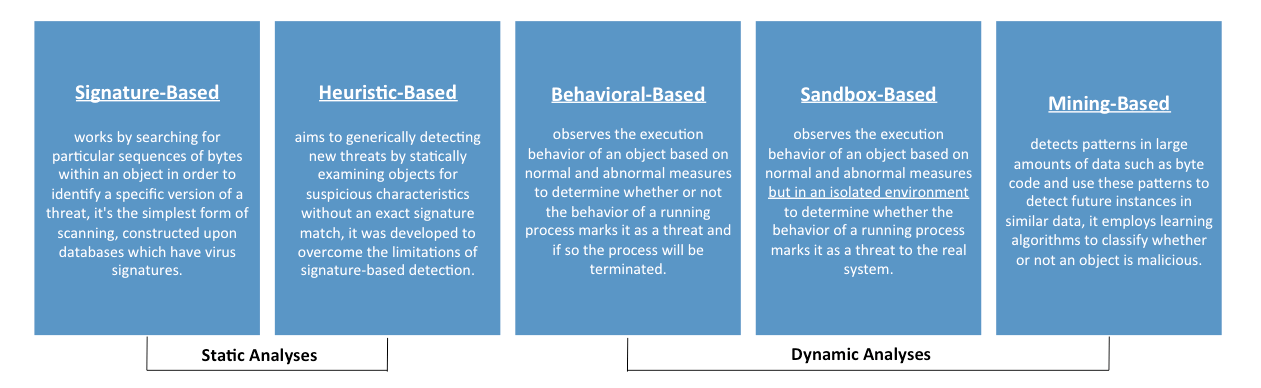
Virus Detection Techniques
" What you just pull code from Rapid9 or some sh*t? since when did you become a script kiddie? "Elliot on Mr. Robot
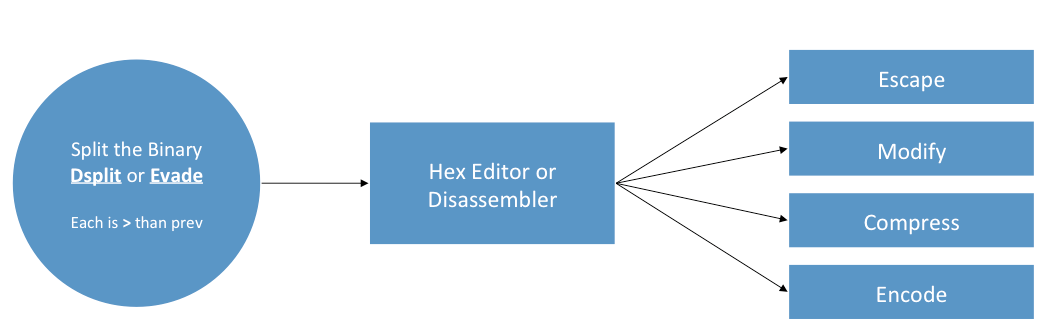
Bypassing Signature-Based Detection
- Find the signature that the antivirus is looking for inside the executable in question.
- Modify the found signature without affecting the execution flow of the executable.
Binary execution is one of the most reliable ways to compromise a system but not the most covert one since executables are suspicious by reputation also antiviruses and other host security controls will always inspect them for malicious functions by signature and/or behavior.
See also: