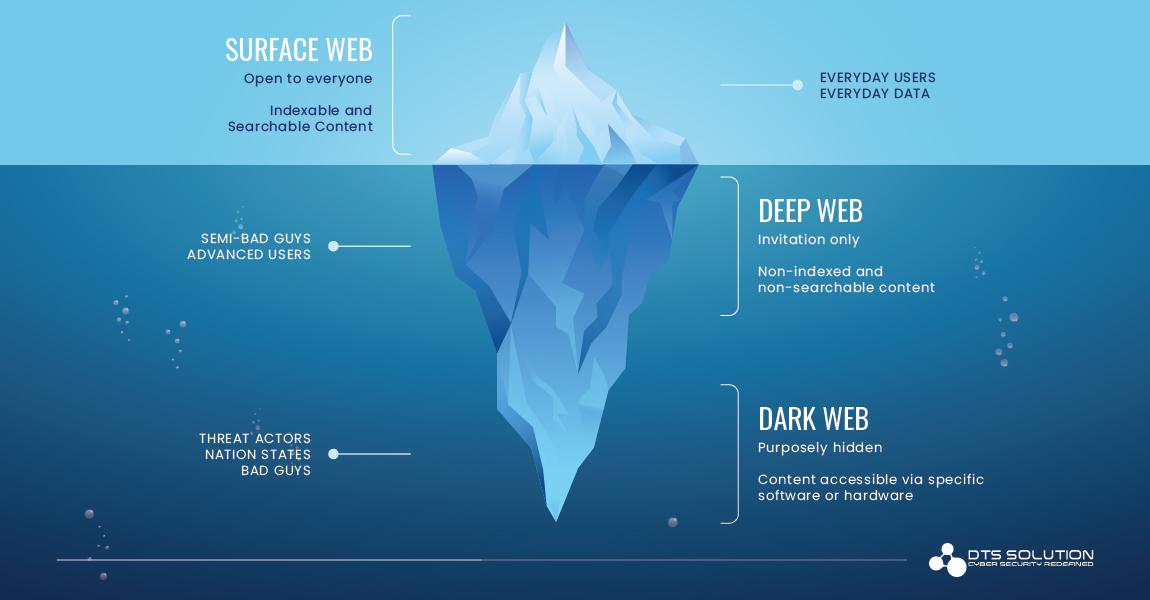
Dark Web and Threat Intelligence (DARKINT)
Since more and more sites and information are always being added to Deep web, we are not able to compute the size of the Deep Web, and the Dark web also keeps on growing with the exponential growth of Deep web. Accessing Dark Web and finding the hidden websites is comparatively easy, but the challenging part is to specifically query the search for finding the relevant and worthwhile threat intelligence data, that will improve our organization’s security aspect.
How the Dark Web Threat Intelligence (DARKINT) allows organizations to detect and prevent threats of all kinds?
If your organization is breached and sensitive information is stolen, there is a higher chance that it will show up on the Dark Web before you know an attack has taken place.
The Value of Dark Web Sources for Threat Intelligence
- Data validation and data verification can be done in early stages to reduce risks associated with the data.
- Identify any data breaches, data leaks, compromised credentials and trade secrets
- Being pro-active against different cyber threats and crimes
- Detection of TTP’s (Techniques Tactics Procedures) used by Attackers
- Detection of exploits, vulnerabilities and other IOC’s (Indicator of Compromise)
- Knowledge about different malwares and tools that Threat Actors use, with their working knowledge, and methods of implementing the attack in typical cases
- Figure out the motivation behind attacks
Dark Web and Threat Intelligence (DARKINT)
Since more and more sites and information are always being added to Deep web, we are not able to compute the size of the Deep Web, and the Dark web also keeps on growing with the exponential growth of Deep web. Accessing Dark Web and finding the hidden websites is comparatively easy, but the challenging part is to specifically query the search for finding the relevant and worthwhile threat intelligence data, that will improve our organization’s security aspect.
How the Dark Web Threat Intelligence (DARKINT) allows organizations to detect and prevent threats of all kinds?
If your organization is breached and sensitive information is stolen, there is a higher chance that it will show up on the Dark Web before you know an attack has taken place.
The Value of Dark Web Sources for Threat Intelligence
- Data validation and data verification can be done in early stages to reduce risks associated with the data.
- Identify any data breaches, data leaks, compromised credentials and trade secrets
- Being pro-active against different cyber threats and crimes
- Detection of TTP’s (Techniques Tactics Procedures) used by Attackers
- Detection of exploits, vulnerabilities and other IOC’s (Indicator of Compromise)
- Knowledge about different malwares and tools that Threat Actors use, with their working knowledge, and methods of implementing the attack in typical cases
- Figure out the motivation behind attacks
See also: