DIFC Data Protection Law – How to Achieve Compliance?
1. Introduction to the Data Privacy Act
On July 1, 2020, the Dubai International Financial Centre (“DIFC”) Data Protection Law No. 5 of 2020 came into effect (“New DP Law”). The Data Protection Law (DPL) prescribes rules and regulations regarding the collection, handling, disclosure and use of personal data in the DIFC, the rights of individuals to whom the personal data relates and the power of the Commissioner of Data Protection in performing their duties in respect of matters related to the processing of personal data as well as the administration and application of the Data Protection Law.
The Data Protection Law embodies international best practice standards, and is consistent with EU regulations and OECD guidelines and is designed to balance the legitimate needs of businesses and organizations to process personal information while upholding an individual’s right to privacy.
2. What are High Risk Processing Activities for Organizations?
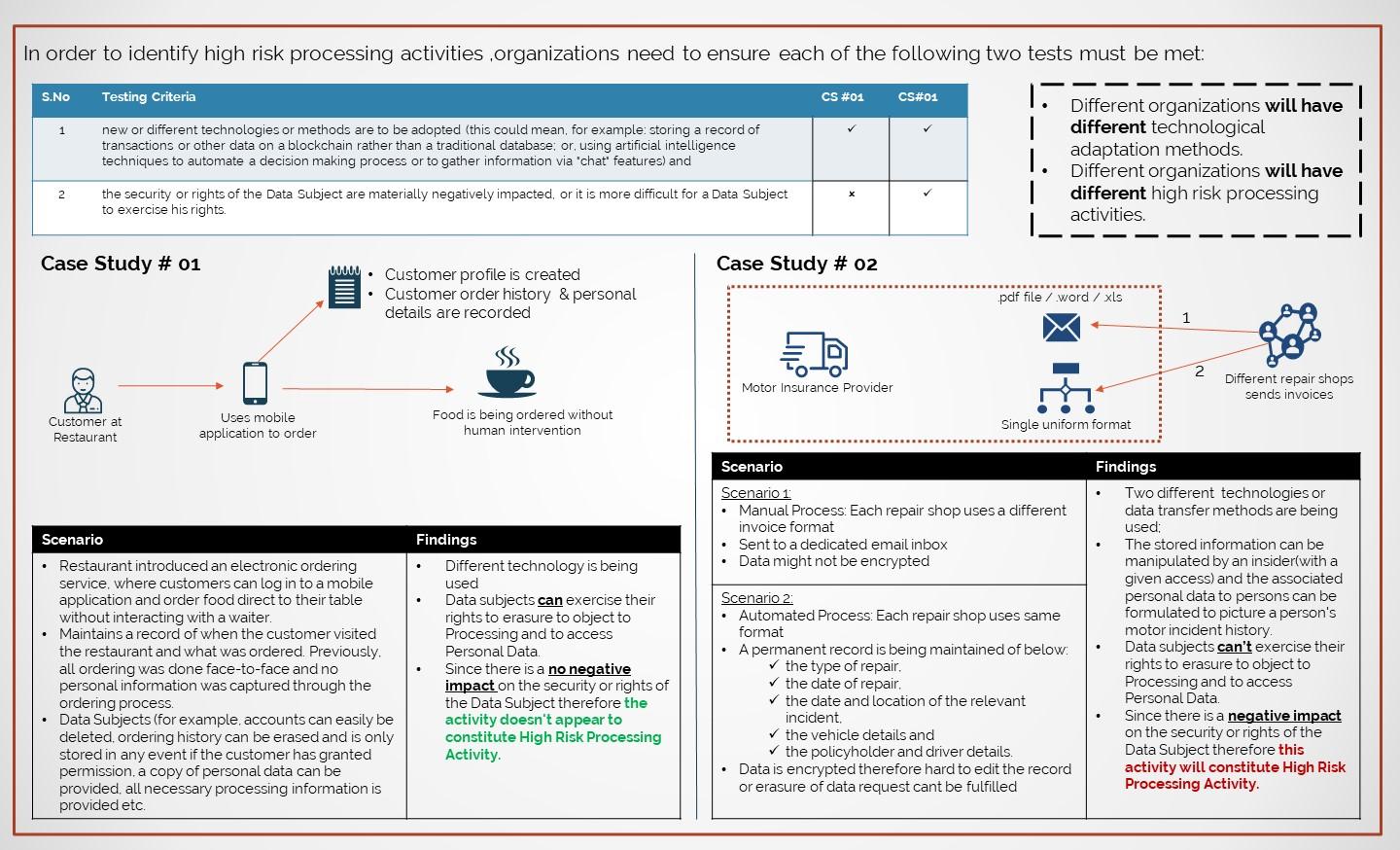
The DPL defines High Risk Processing Activity as:
“Processing of Personal Data where one (1) or more of the following applies:
a) Processing that includes the adoption of new or different technologies or methods, which creates a materially increased risk to the security or rights of a Data Subject or renders it more difficult for a Data Subject to exercise his rights;
b) a considerable amount of Personal Data will be Processed (including staff and contractor Personal Data) and where such Processing is likely to result in a high risk to the Data Subject, including due to the sensitivity of the Personal Data or risks relating to the security, integrity or privacy of the Personal Data;
c) the Processing will involve a systematic and extensive evaluation of personal aspects relating to natural persons, based on automated Processing, including Profiling, and on which decisions are based that produce legal effects concerning the natural person or similarly significantly affect the natural person; or
d) a material amount of Special Categories of Personal Data is to be Processed.”
DIFC Data Protection Law, Schedule 1, Article 3
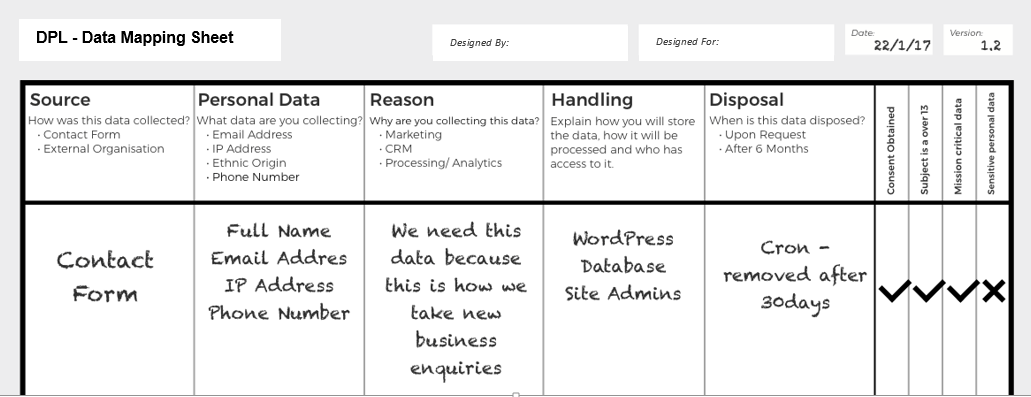
3. Does your Organization is involved in High Risk Processing activities?
For the very first step organizations need to evaluate their activities as per the DPL:
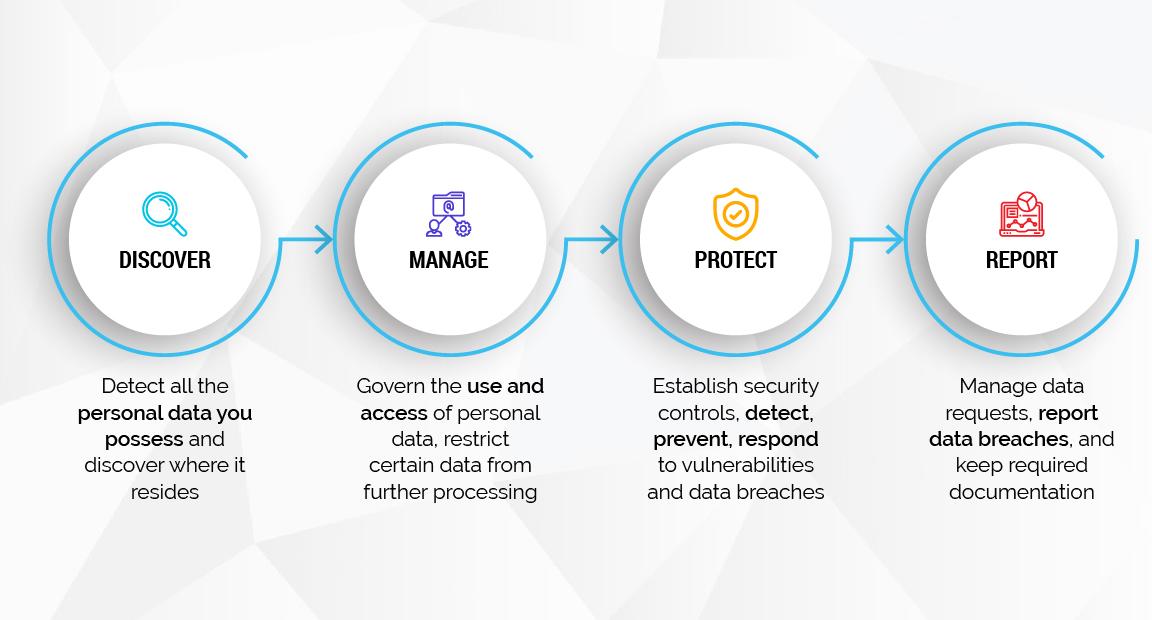
4. How Organizations Can Address and Maintain Compliance towards Data Privacy Issues?
For organizations who are seeking DPL compliance, they need to work and focus on key areas to achieve and maintain compliance status:
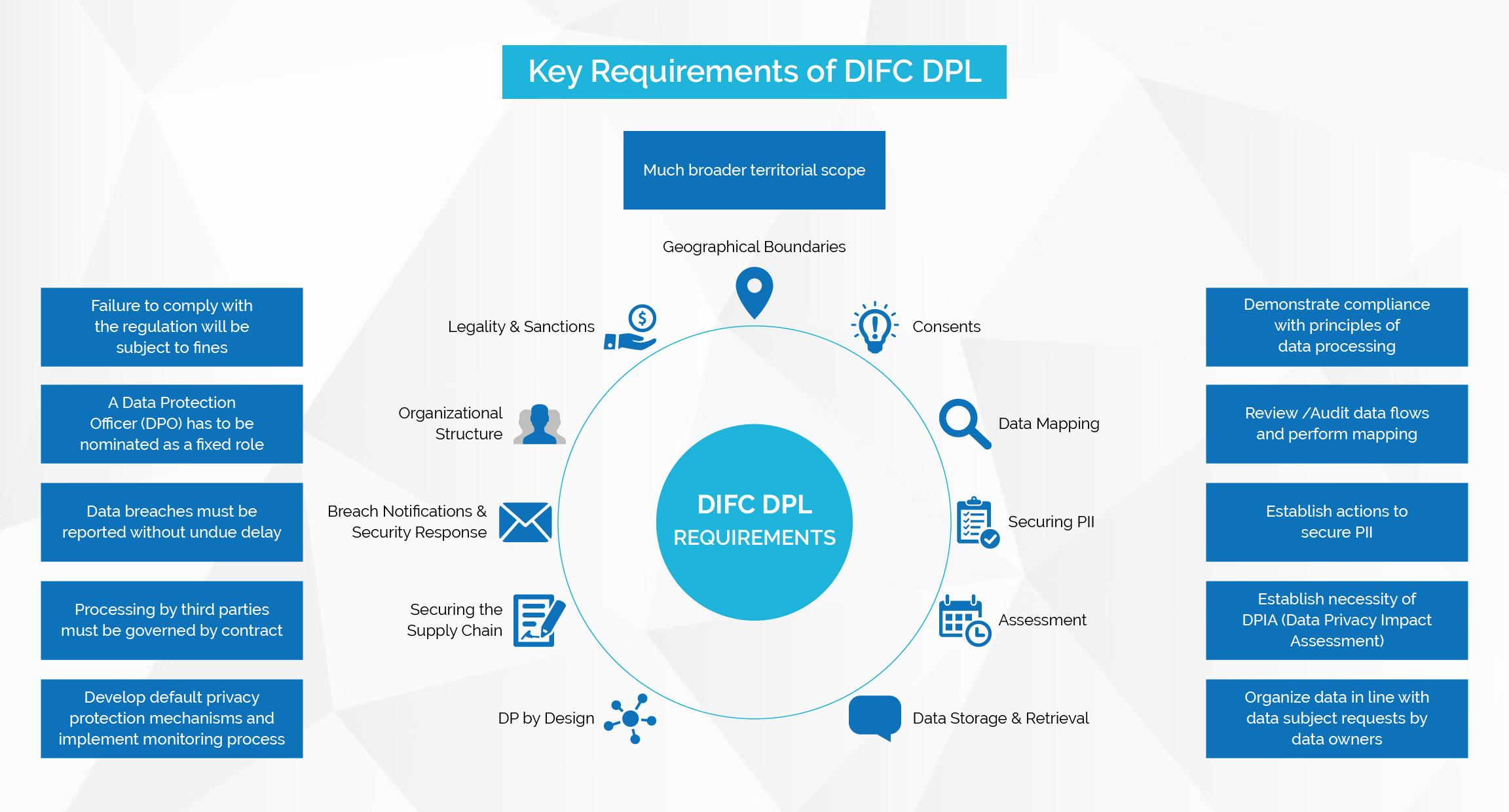
5. Some of the Key Requirements of DIFC DPL
Listed below are some key requirements of DIFC DPL:
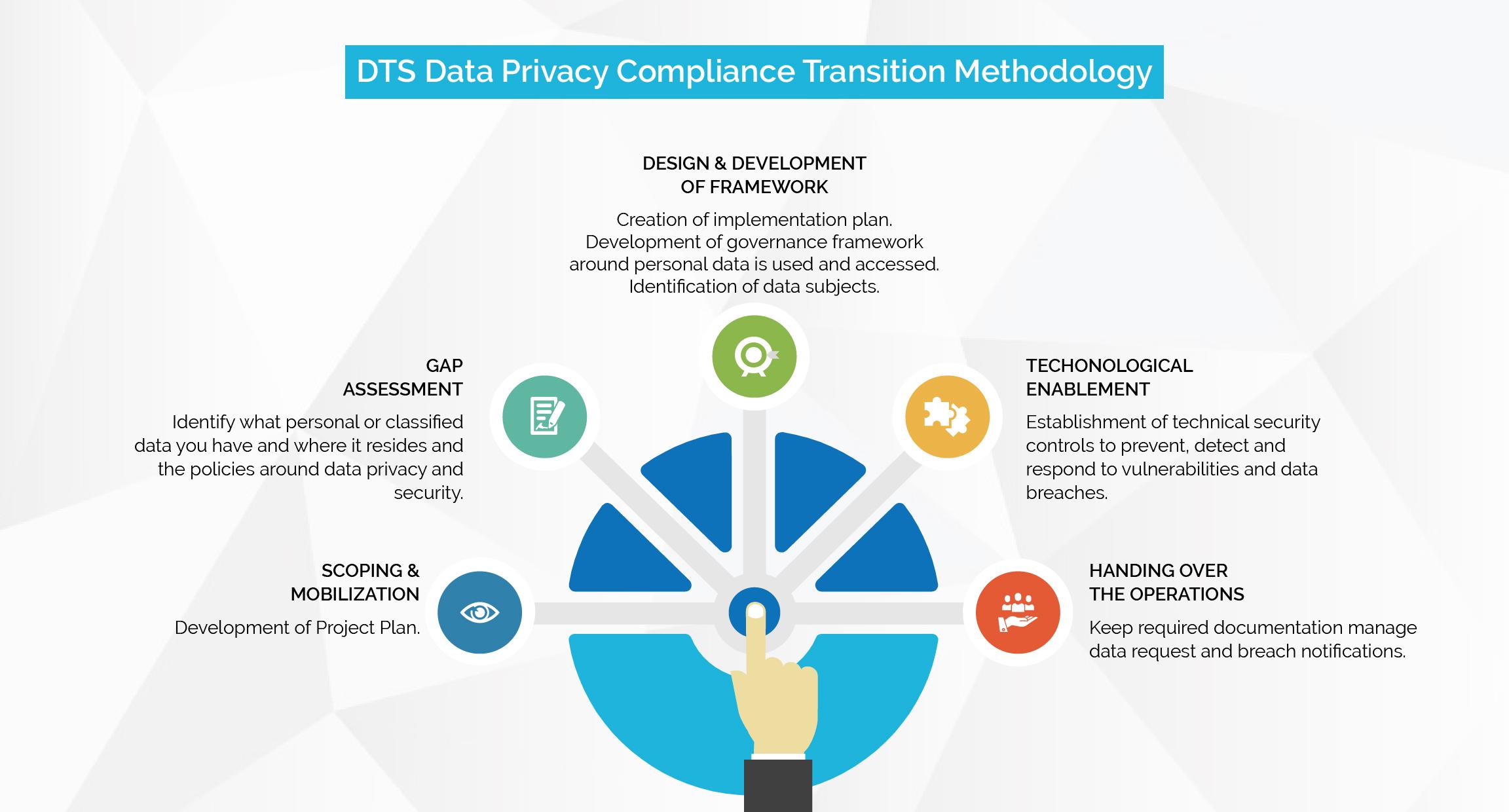
1. Scoping & Mobilization
The DTS team works with you to build a project plan that meets your timetable and team needs. You’re assigned a dedicated project manager who will oversee day-to-day activities and ensure your project stays on track.
- Creation of project plan to implement DIFC DPL
- Identification & inclusion of the right stakeholders in your project
- Communication plan
2. Gap Assessment
Our assessments seek to determine what, how, where and why sensitive data is being stored and collected – and compare the effectiveness of your privacy controls against compliance mandates and industry best practices. Comprehensive assessment of current state people, process, and technology of Data Loss Prevention environment.
3. Design & Development of Framework
Development of framework will start from identification of PII data or sensitive data or Critical Data Elements (CDE), for this DTS adopts systematic approach by collecting information from various divisions within an organization
The other activities includes the following:
- Creation of an internal Data Protection Policy for personal data.
- Creation of Data Classification Policy for personal data.
- Creation of other top-level policies as needed – e.g., the Data Retention Policy.
- Creation of Data Flow Diagram’s (DFD’s) based on collected data for different business units.
- Providing awareness to employees about key DIFD DPL requirements.
4. Technological Enablement
Based on leading-edge best practices, DTS provides a repeatable mature method of properly protecting a company’s sensitive data and integrating fully in the security ecosystem ensuring that DLP does not operate in a silo fashion. The key activities includes the following:
- Implementation of Data Loss Prevention Program
- Implementation of strategic DLP, integration with Finance, Supply Chain, Customer Relationship Management, Human Resources, Corporate Communications, Legal, Compliance , IT processes
- Provide reports, dashboards and recommendations for improved corporate security practices
- Mature the DLP program to a maintainable, repeatable and operational state
5. Handing Over the Operations
The last step of our methodology includes the following:
- Demonstration of effectiveness of Personal Data handling practices.
- Handing over the operational environment of DLP.
- Providing Training program that enables your staff to conduct re-assessments using the same methodology.
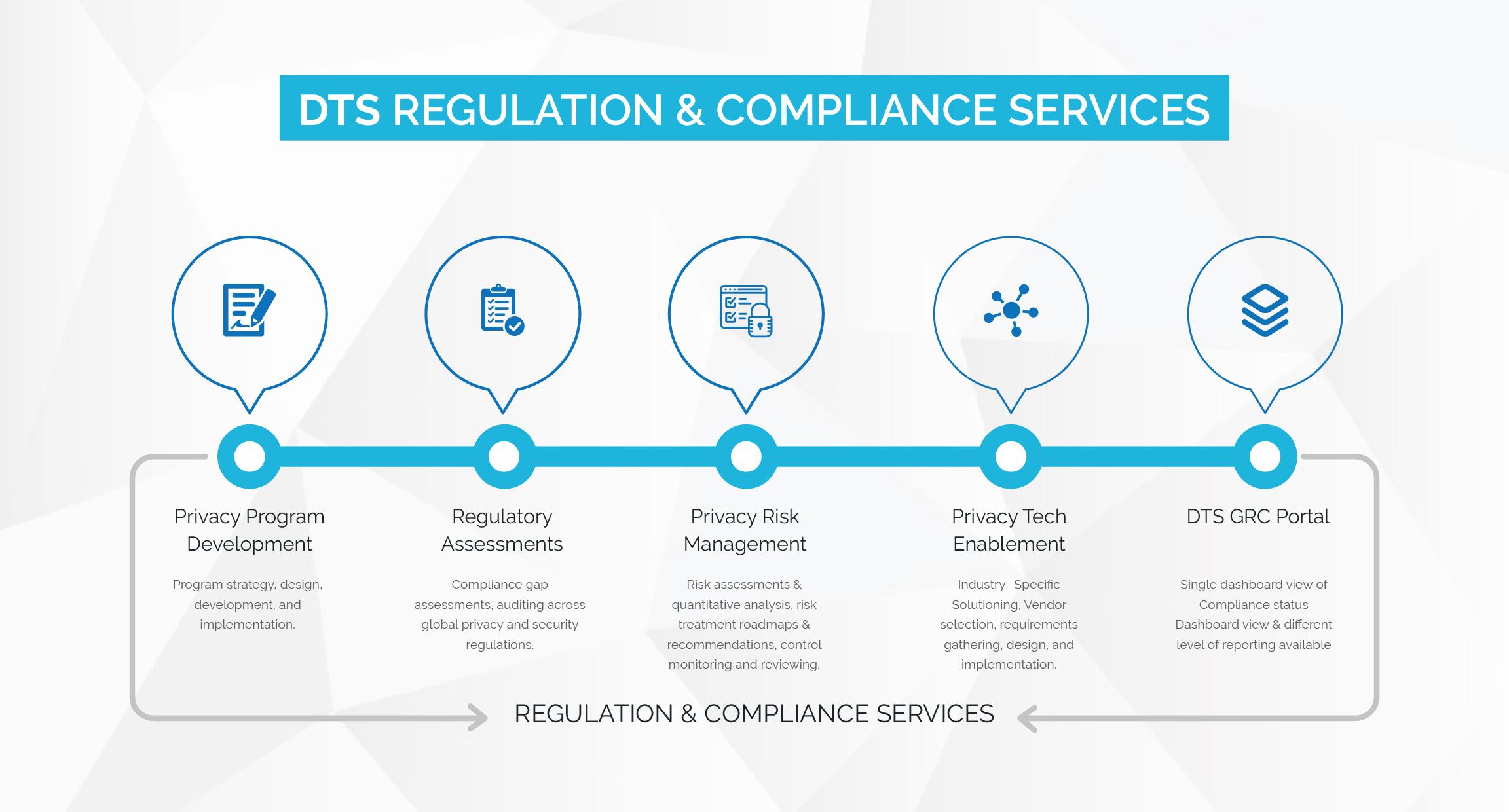
8. Overview of our Services
For clients who are seeking privacy regulation compliance, DTS offers the following services that will assist in key areas.
Privacy Program Development: Program strategy, design, development, and implementation.
Regulatory Assessments: Compliance gap assessments, auditing across global privacy and security regulations.
Privacy Risk Management: Risk assessments & quantitative analysis, risk treatment roadmaps & recommendations, control monitoring and reviewing.
Privacy Tech Enablement: Industry- Specific Solutioning, Vendor selection, requirements gathering, design, and implementation.
DTS GRC Portal: Single dashboard view of Compliance status, Dashboard view & different level of reporting available
DIFC Data Protection Law – How to Achieve Compliance?
1. Introduction to the Data Privacy Act
On July 1, 2020, the Dubai International Financial Centre (“DIFC”) Data Protection Law No. 5 of 2020 came into effect (“New DP Law”). The Data Protection Law (DPL) prescribes rules and regulations regarding the collection, handling, disclosure and use of personal data in the DIFC, the rights of individuals to whom the personal data relates and the power of the Commissioner of Data Protection in performing their duties in respect of matters related to the processing of personal data as well as the administration and application of the Data Protection Law.
The Data Protection Law embodies international best practice standards, and is consistent with EU regulations and OECD guidelines and is designed to balance the legitimate needs of businesses and organizations to process personal information while upholding an individual’s right to privacy.
2. What are High Risk Processing Activities for Organizations?
The DPL defines High Risk Processing Activity as:
“Processing of Personal Data where one (1) or more of the following applies:
a) Processing that includes the adoption of new or different technologies or methods, which creates a materially increased risk to the security or rights of a Data Subject or renders it more difficult for a Data Subject to exercise his rights;
b) a considerable amount of Personal Data will be Processed (including staff and contractor Personal Data) and where such Processing is likely to result in a high risk to the Data Subject, including due to the sensitivity of the Personal Data or risks relating to the security, integrity or privacy of the Personal Data;
c) the Processing will involve a systematic and extensive evaluation of personal aspects relating to natural persons, based on automated Processing, including Profiling, and on which decisions are based that produce legal effects concerning the natural person or similarly significantly affect the natural person; or
d) a material amount of Special Categories of Personal Data is to be Processed.”
DIFC Data Protection Law, Schedule 1, Article 3
3. Does your Organization is involved in High Risk Processing activities?
For the very first step organizations need to evaluate their activities as per the DPL:
4. How Organizations Can Address and Maintain Compliance towards Data Privacy Issues?
For organizations who are seeking DPL compliance, they need to work and focus on key areas to achieve and maintain compliance status:
5. Some of the Key Requirements of DIFC DPL
Listed below are some key requirements of DIFC DPL:
6. How Do We Help? DTS Data Privacy Compliance Transition Methodology
DTS defines its five steps methodology as a roadmap to achieve compliance towards the DPL.
7. Snippet of Practical Implementation by DTS
In order to make it easier for your business to follow the DPL compliance requirements, DTS provides its comprehensive approach which has been outlined below:
“Privacy is not only a regulatory compliance issue, but also a strategic business issue.”
1. Scoping & Mobilization
The DTS team works with you to build a project plan that meets your timetable and team needs. You’re assigned a dedicated project manager who will oversee day-to-day activities and ensure your project stays on track.
- Creation of project plan to implement DIFC DPL
- Identification & inclusion of the right stakeholders in your project
- Communication plan
2. Gap Assessment
Our assessments seek to determine what, how, where and why sensitive data is being stored and collected – and compare the effectiveness of your privacy controls against compliance mandates and industry best practices. Comprehensive assessment of current state people, process, and technology of Data Loss Prevention environment.
3. Design & Development of Framework
Development of framework will start from identification of PII data or sensitive data or Critical Data Elements (CDE), for this DTS adopts systematic approach by collecting information from various divisions within an organization.
The other activities includes the following:
- Creation of an internal Data Protection Policy for personal data.
- Creation of Data Classification Policy for personal data.
- Creation of other top-level policies as needed – e.g., the Data Retention Policy.
- Creation of Data Flow Diagram’s (DFD’s) based on collected data for different business units.
- Providing awareness to employees about key DIFD DPL requirements.
4. Technological Enablement
Based on leading-edge best practices, DTS provides a repeatable mature method of properly protecting a company’s sensitive data and integrating fully in the security ecosystem ensuring that DLP does not operate in a silo fashion. The key activities includes the following:
- Implementation of Data Loss Prevention Program
- Implementation of strategic DLP, integration with Finance, Supply Chain, Customer Relationship Management, Human Resources, Corporate Communications, Legal, Compliance , IT processes
- Provide reports, dashboards and recommendations for improved corporate security practices
- Mature the DLP program to a maintainable, repeatable and operational state
5. Handing Over the Operations
The last step of our methodology includes the following:
- Demonstration of effectiveness of Personal Data handling practices.
- Handing over the operational environment of DLP.
- Providing Training program that enables your staff to conduct re-assessments using the same methodology.
8. Overview of our Services
For clients who are seeking privacy regulation compliance, DTS offers the following services that will assist in key areas.
Privacy Program Development: Program strategy, design, development, and implementation.
Regulatory Assessments: Compliance gap assessments, auditing across global privacy and security regulations.
Privacy Risk Management: Risk assessments & quantitative analysis, risk treatment roadmaps & recommendations, control monitoring and reviewing.
Privacy Tech Enablement: Industry- Specific Solutioning, Vendor selection, requirements gathering, design, and implementation.
DTS GRC Portal: Single dashboard view of Compliance status, Dashboard view & different level of reporting available
See also: