Introduction
Both detection and response are essential elements of a strong cybersecurity strategy. But depending just on automatic detections is no longer sufficient to keep your organization online.
Security teams must operationalize threat intelligence by carrying out proactive, hypothesis-driven threat hunts to lower the likelihood that sophisticated and unknown threats may affect business. You may strengthen your defenses against the most sophisticated cyber threats by actively seeking for, looking into, and eliminating risks early in the attack chain.
By coordinating your cybersecurity strategy with an established risk management framework, you may create an organized method for handling cyber threats
Because of its extensive set of risk management techniques that are in line with other cybersecurity laws and standards like HIPAA, PCI DSS, Systems and Organization Controls (SOC) 2, and International Organization for Standardization (ISO) 27001, the NIST Cybersecurity Framework (NIST CSF) stands out as a particularly well-liked choice.
We discuss in this article how implementing NIST CSF into practice may enhance your threat detection and response capabilities and show customers, auditors, regulators, and other stakeholders that your organization is compliant.
Introduction
Both detection and response are essential elements of a strong cybersecurity strategy. But depending just on automatic detections is no longer sufficient to keep your organization online.
Security teams must operationalize threat intelligence by carrying out proactive, hypothesis-driven threat hunts to lower the likelihood that sophisticated and unknown threats may affect business. You may strengthen your defenses against the most sophisticated cyber threats by actively seeking for, looking into, and eliminating risks early in the attack chain.
By coordinating your cybersecurity strategy with an established risk management framework, you may create an organized method for handling cyber threats. Because of its extensive set of risk management techniques that are in line with other cybersecurity laws and standards like HIPAA, PCI DSS, Systems and Organization Controls (SOC) 2, and International Organization for Standardization (ISO) 27001, the NIST Cybersecurity Framework (NIST CSF) stands out as a particularly well-liked choice.
We discuss in this article how implementing NIST CSF into practice may enhance your threat detection and response capabilities and show customers, auditors, regulators, and other stakeholders that your organization is compliant.
Benefits of the NIST framework:
Many businesses, governments, and industries have embraced the NIST Cybersecurity Framework, commonly known as the Cybersecurity Framework or simply CSF, as a set of guidelines to enhance their cybersecurity procedures. Here are some of the CSF’s main advantages and seven reasons to employ it in your cybersecurity efforts, in addition to the many helpful tools and best practices it offers.
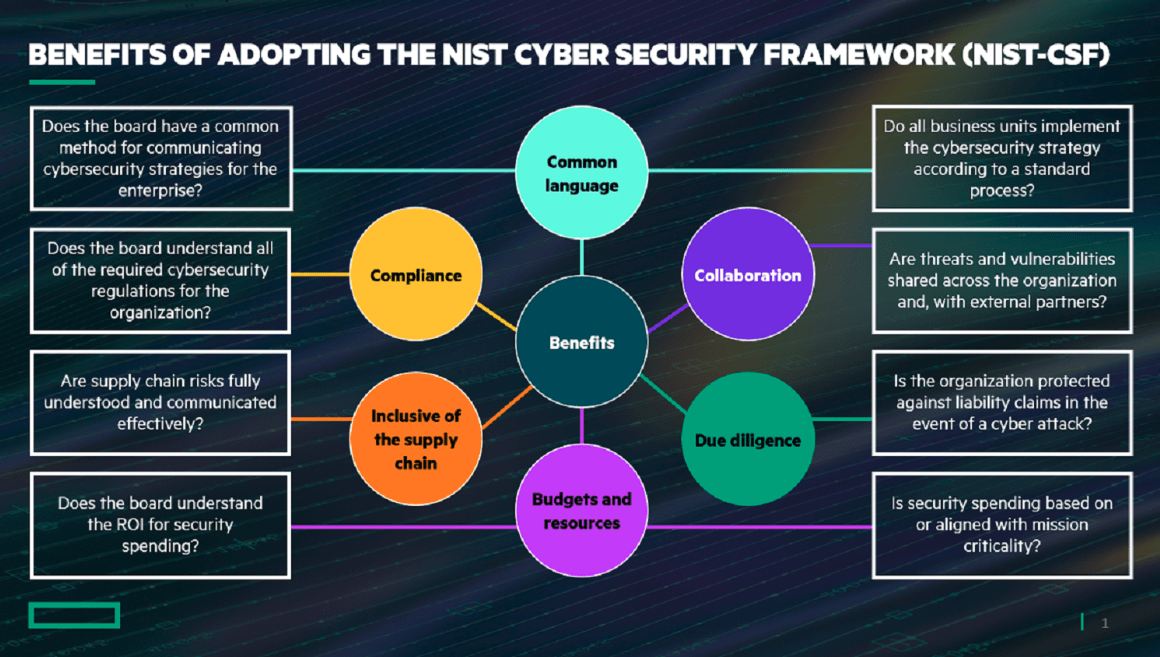
- Helps Organizations Understand Their Risks.
- Facilitates Communication between Stakeholders.
- Improves an Organization’s Cybersecurity Posture.
- Encourages the Use of Proven and Tested Solutions.
- Scalable and Flexible.
- Improves an Organization’s Incident Response Capabilities.
- The Framework Facilitates Regulatory Compliance.
Benefits of the NIST framework
Many businesses, governments, and industries have embraced the NIST Cybersecurity Framework, commonly known as the Cybersecurity Framework or simply CSF, as a set of guidelines to enhance their cybersecurity procedures. Here are some of the CSF’s main advantages and seven reasons to employ it in your cybersecurity efforts, in addition to the many helpful tools and best practices it offers.
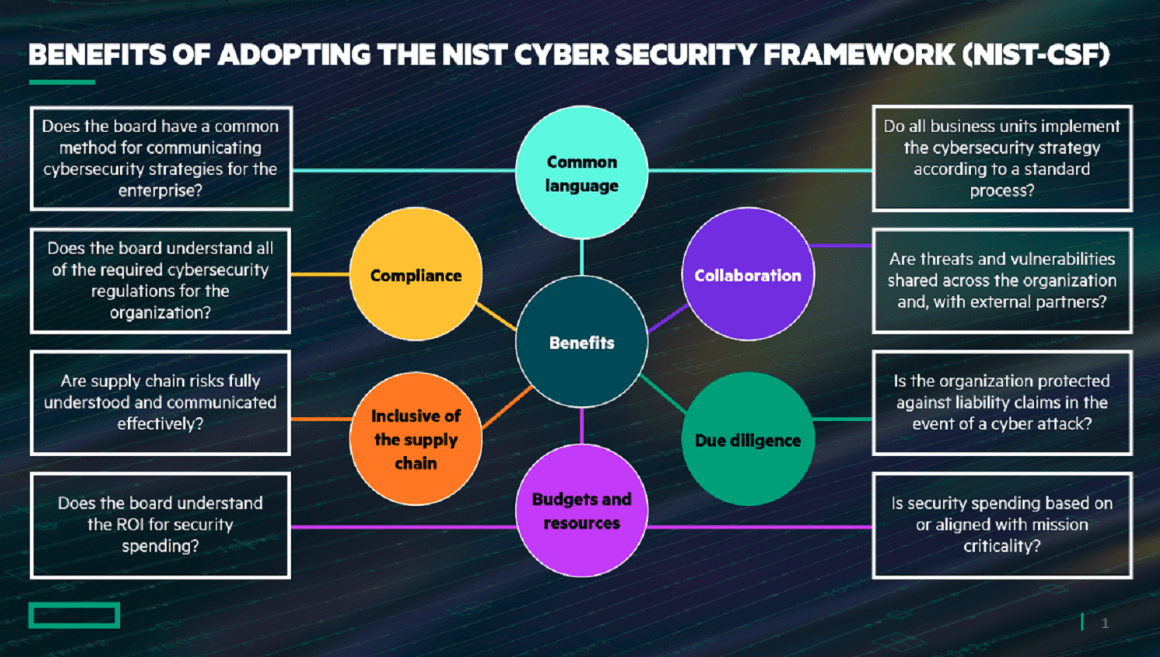
- Helps Organizations Understand Their Risks.
- Facilitates Communication between Stakeholders.
- Improves an Organization’s Cybersecurity Posture.
- Encourages the Use of Proven and Tested Solutions.
- Scalable and Flexible.
- Improves an Organization’s Incident Response Capabilities.
- The Framework Facilitates Regulatory Compliance.
The six pillars:
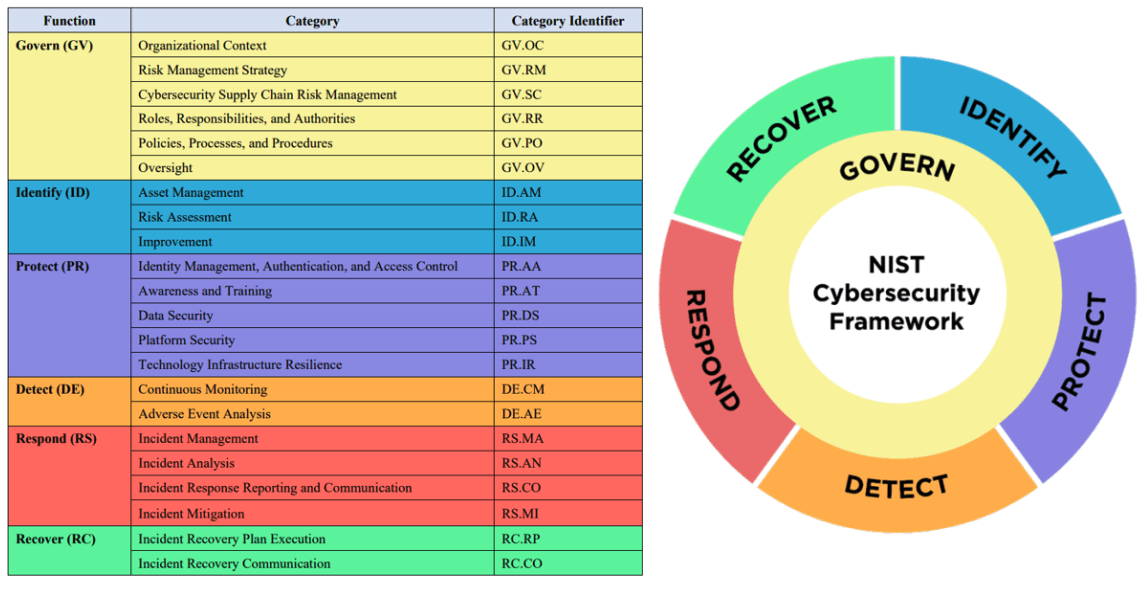
Six functional areas comprise the structure of the framework: Identify, Protect, Detect, Respond, Recover, and Govern. Every function lays out suggested cybersecurity actions, results, and sources.
- Identify: Gain knowledge about controlling cybersecurity risk to resources, capabilities, data, and systems.
- Protect: Create and implement the required measures to guarantee the provision of essential infrastructure services.
- Detect: Put in place the proper safeguards to spot malicious activity.
- Respond: Deal with an incident in cybersecurity that has been noticed.
- Recover: Uphold resilience plans and restore compromised services or capabilities.
- Govern: Create and maintain suitable risk management procedures and governance frameworks.
The six pillars:
Six functional areas comprise the structure of the framework: Identify, Protect, Detect, Respond, Recover, and Govern. Every function lays out suggested cybersecurity actions, results, and sources.
- Identify: Gain knowledge about controlling cybersecurity risk to resources, capabilities, data, and systems.
- Protect: Create and implement the required measures to guarantee the provision of essential infrastructure services.
- Detect: Put in place the proper safeguards to spot malicious activity.
- Respond: Deal with an incident in cybersecurity that has been noticed.
- Recover: Uphold resilience plans and restore compromised services or capabilities.
- Govern: Create and maintain suitable risk management procedures and governance frameworks.

Threat Detection
The NIST Cybersecurity Framework’s Detect function is all about setting up measures to spot malicious activities on your network. A proactive cybersecurity posture relies heavily on your capacity to identify threats early, which enables you to launch a swift, well-coordinated response.
Utilizing security tools and capabilities strategically concerning the three main types of anomalies and events, detection processes, and continuous monitoring is necessary to implement the Detect function. This entails integrating security information and event management (SIEM) platforms to collect and analyze data from various signals inside your environment, setting up anomaly detection tools, and ensuring continuous monitoring of your environment.
24/7 visibility and round-the-clock coverage throughout your attack surface, supported by the most recent threat intelligence, are necessary for effective threat detection. You may identify undiscovered or emerging threats before they have an opportunity to cause disruptions to your business by combining data about Indicators of Compromise (IOCs), malicious IPs, and attacker tactics, methods, and procedures (TTPs) with multi-signal telemetry and visibility across your environment.
Threat Detection
The NIST Cybersecurity Framework’s Detect function is all about setting up measures to spot malicious activities on your network. A proactive cybersecurity posture relies heavily on your capacity to identify threats early, which enables you to launch a swift, well-coordinated response.
Utilizing security tools and capabilities strategically concerning the three main types of anomalies and events, detection processes, and continuous monitoring is necessary to implement the Detect function. This entails integrating security information and event management (SIEM) platforms to collect and analyze data from various signals inside your environment, setting up anomaly detection tools, and ensuring continuous monitoring of your environment.
24/7 visibility and round-the-clock coverage throughout your attack surface, supported by the most recent threat intelligence, are necessary for effective threat detection. You may identify undiscovered or emerging threats before they have an opportunity to cause disruptions to your business by combining data about Indicators of Compromise (IOCs), malicious IPs, and attacker tactics, methods, and procedures (TTPs) with multi-signal telemetry and visibility across your environment.
Threat Response
The NIST Cybersecurity Framework’s respond function lays forth suggestions for what should be done right away when a cybersecurity event is discovered. Sustaining and quickly recovering from cyber events is made possible by efficient response mechanisms, which also minimize business disturbance and save downtime expenses. Furthermore, a well-planned threat response shows a high degree of readiness and adaptability.
Create a thorough Incident Response Plan (IRP) before implementing the Respond function. Containment measures to stop threats from spreading laterally, recovery procedures to recover compromised systems and data, and communications plans for managing messages both during and after an incident should all be part of this plan. To make sure that response measures are efficient and specific to the threats that have been discovered, data gathered from operationalizing threat intelligence and threat hunting should be used as a basis.
Additionally, proactive risk management requires that your IRP include a comprehensive post-incident recovery and analysis. Procedures for post-incident digital forensics investigation to ascertain the attack’s origin, extent, and attacker paths should be included in your incident response plan (IRP). Your ability to respond to attacks will be improved, and your security posture will be strengthened against novel threats.
Threat Response
The NIST Cybersecurity Framework’s respond function lays forth suggestions for what should be done right away when a cybersecurity event is discovered. Sustaining and quickly recovering from cyber events is made possible by efficient response mechanisms, which also minimize business disturbance and save downtime expenses. Furthermore, a well-planned threat response shows a high degree of readiness and adaptability.
Create a thorough Incident Response Plan (IRP) before implementing the Respond function. Containment measures to stop threats from spreading laterally, recovery procedures to recover compromised systems and data, and communications plans for managing messages both during and after an incident should all be part of this plan. To make sure that response measures are efficient and specific to the threats that have been discovered, data gathered from operationalizing threat intelligence and threat hunting should be used as a basis.
Additionally, proactive risk management requires that your IRP include a comprehensive post-incident recovery and analysis. Procedures for post-incident digital forensics investigation to ascertain the attack’s origin, extent, and attacker paths should be included in your incident response plan (IRP). Your ability to respond to attacks will be improved, and your security posture will be strengthened against novel threats.
Importance of the Detect and Respond Functions:
Attacks using ransomware and malware nowadays are more adaptable and difficult to identify. The proliferation of Malware-as-a-Service (MaaS) and Ransomware-as-a-Service (RaaS) models has made it easier for untrained threat actors to buy malware toolkits, tailor them to individual victims, and launch attacks more often.
Traditional signature-based security controls frequently fail to identify and stop attacks because of the volume and variety of these threats.
An organization’s recovery time and downtime costs can be greatly reduced by promptly identifying and mitigating cyber threats early in the attack chain, which is made possible by having effective threat detection and response capabilities.
Timely response and preventing minor occurrences from turning into significant breaches are dependent on rapid detection. Robust reaction mechanisms enable you to quickly neutralize and contain threats, reducing their impact on business operations, as soon as they are recognized.
Importance of the Detect and Respond Functions:
Attacks using ransomware and malware nowadays are more adaptable and difficult to identify. The proliferation of Malware-as-a-Service (MaaS) and Ransomware-as-a-Service (RaaS) models has made it easier for untrained threat actors to buy malware toolkits, tailor them to individual victims, and launch attacks more often.
Traditional signature-based security controls frequently fail to identify and stop attacks because of the volume and variety of these threats.
An organization’s recovery time and downtime costs can be greatly reduced by promptly identifying and mitigating cyber threats early in the attack chain, which is made possible by having effective threat detection and response capabilities. Timely response and preventing minor occurrences from turning into significant breaches are dependent on rapid detection. Robust reaction mechanisms enable you to quickly neutralize and contain threats, reducing their impact on business operations, as soon as they are recognized.
Importance of proactive threat hunting:
Integrating proactive, hypothesis-driven threat hunting is crucial for effective threat detection and response as cyber threats get more sophisticated and evasive.
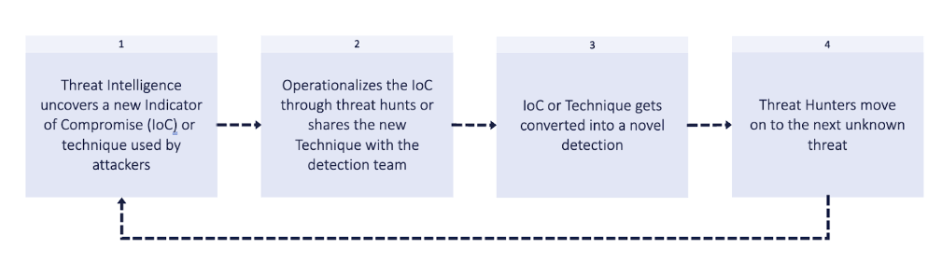
The process of actively looking for indications of malicious activity or IOCs that are not yet picked up by current security solutions is known as “proactive threat hunting.” It proactively searches your environment for new and unknown threats using automated or manual procedures.
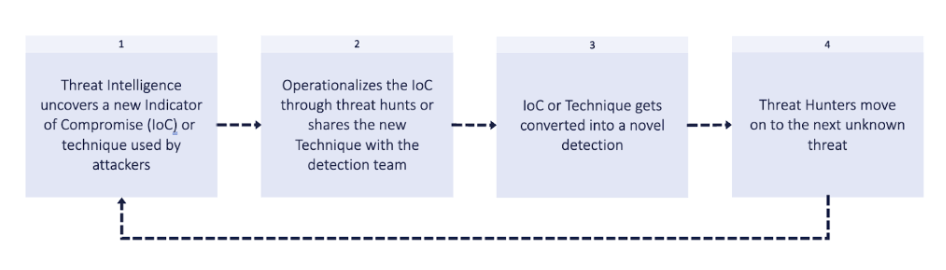
Proactive threat hunting reduces the average time it takes to detect an attack and the average time it takes to respond (MTTR). You can lower your total security risk by proactively addressing vulnerabilities by actively searching for IOCs and unusual behaviors.
Importance of proactive threat hunting:
Integrating proactive, hypothesis-driven threat hunting is crucial for effective threat detection and response as cyber threats get more sophisticated and evasive.
The process of actively looking for indications of malicious activity or IOCs that are not yet picked up by current security solutions is known as “proactive threat hunting.” It proactively searches your environment for new and unknown threats using automated or manual procedures.
See also: