Businesses have, in recent times, adopted modern methods of working across different devices, locations and web applications. While most of these businesses will list a bunch of advantages that stem from this diversity, they most likely will state that they are aware that cyber-attacks have become increasingly sophisticated and sometimes targeted.
Threat actors now understand that such organizations have the problem of ensuring that only the right people access their data and ensuring that those right people are accessing only what they need to. They know that the modern workforce enjoys the flexibility of working from anywhere and connecting to any network that works. These threat actors know, too, that they need to find the weakest link.
Traditional security measures, often perimeter-based, struggle to keep up with the decentralized nature of today’s work environment. Cyber threats, such as phishing attacks, malware, and ransomware, are increasingly sophisticated.
The attack surface has expanded, making endpoint security more challenging. Enterprises need a solution that can adapt to these evolving threats while supporting the seamless, efficient work processes demanded by modern employees. Good thing most technological efforts in recent times have been channeled towards security. Securing every possible asset from the user to the browser.
Hello, Enterprise Secure Browser.
An Enterprise Secure Browser (ESB) is designed to address these challenges head-on. It offers a secure browsing environment that isolates enterprise data from potential threats, ensuring that employees can work safely from anywhere. It offers a safe, controlled web browsing environment that is tailored to company requirements and gives complete visibility and control over all websites and user activity.
How?
The core of the Enterprise Secure Browser is centralized control over web activities. This unified approach allows the deployment of policies across browsers and even extensions and mobile devices. Administrators can manage the ESB from a centralized console so that activities such as setting security policies, monitoring web activity, and managing user permissions can be controlled. The centralized approach simplifies administration and ensures consistent policy enforcement across the organization.
Some advanced versions incorporate advanced threat detection mechanisms. They continuously monitor web traffic for signs of malicious activity, leveraging threat intelligence and machine learning to identify and mitigate threats in real time.
Businesses have, in recent times, adopted modern methods of working across different devices, locations and web applications. While most of these businesses will list a bunch of advantages that stem from this diversity, they most likely will state that they are aware that cyber-attacks have become increasingly sophisticated and sometimes targeted.
Threat actors now understand that such organizations have the problem of ensuring that only the right people access their data and ensuring that those right people are accessing only what they need to. They know that the modern workforce enjoys the flexibility of working from anywhere and connecting to any network that works. These threat actors know, too, that they need to find the weakest link.
Traditional security measures, often perimeter-based, struggle to keep up with the decentralized nature of today’s work environment. Cyber threats, such as phishing attacks, malware, and ransomware, are increasingly sophisticated. The attack surface has expanded, making endpoint security more challenging. Enterprises need a solution that can adapt to these evolving threats while supporting the seamless, efficient work processes demanded by modern employees. Good thing most technological efforts in recent times have been channeled towards security. Securing every possible asset from the user to the browser.
Hello, Enterprise Secure Browser.
An Enterprise Secure Browser (ESB) is designed to address these challenges head-on. It offers a secure browsing environment that isolates enterprise data from potential threats, ensuring that employees can work safely from anywhere. It offers a safe, controlled web browsing environment that is tailored to company requirements and gives complete visibility and control over all websites and user activity.
How?
The core of the Enterprise Secure Browser is centralized control over web activities. This unified approach allows the deployment of policies across browsers and even extensions and mobile devices. Administrators can manage the ESB from a centralized console so that activities such as setting security policies, monitoring web activity, and managing user permissions can be controlled. The centralized approach simplifies administration and ensures consistent policy enforcement across the organization.
Some advanced versions incorporate advanced threat detection mechanisms. They continuously monitor web traffic for signs of malicious activity, leveraging threat intelligence and machine learning to identify and mitigate threats in real time.
RBI - Secure Rendering vs. ESB - Secure Handling.
This is not to be confused with Remote Browser Isolation (RBI). RBI works by executing web content in a secure, isolated environment, usually on a remote server, rather than on the user’s local device. Each isolated browser session renders web content but sends only a safe, interactive visual stream to the user’s device.
Remote Browser Isolation (RBI) allows the user to interact with websites as if they were local, but the actual web content never reaches the endpoint. This ensures that any malicious content, such as malware disguised as enticing offers or legitimate-looking downloads, encountered during browsing cannot affect the endpoint. By isolating web content in a secure, remote environment, RBI provides robust protection against various cyber threats, enhancing overall security and user confidence while browsing.
So, in essence, RBI works by allowing the user, whose device is most-likely managed by the IT admin, to carry on as usual except that a remote server sits as a knight between the user and the internet. It works in situations where web traffic deemed risky/suspicious need to be isolated, where drive-by downloads are a risk and where other exploits need to be kept at bay.
ESB, on the other hand, is more suited for the modern workforce since they are used to enable secure access to corporate resources by all unmanaged devices. It uses corporate security policies to control how data is handled within the browser. Features such as preventing copy-paste, blocking downloads/uploads, and restricting access to specific websites ensure that sensitive information remains protected.
Depending on the company’s needs or on the solution in use, various use cases can exist to address the secure handling of browser activities.
Some of these include:
- Unmanaged Devices – which generally include devices of remote workers, contractors, business partners, outsourcing partners etc. Organizations can provide access to essential websites, SaaS apps and other resources and employ the principle of least privilege by using ESBs.
- BYOD – ESBs facilitate this flexibility by providing a secure environment that isolates corporate web use from personal activities and protects company data on personal devices.
- VDI – Companies can now retire the delivery of virtual desktop images over networks since every user can use their own endpoint and safely interact with sensitive or corporate resources.
- Zero Trust Access – Controls for checking user identity, location, etc., can easily be deployed.
RBI - Secure Rendering vs. ESB - Secure Handling.
This is not to be confused with Remote Browser Isolation (RBI). RBI works by executing web content in a secure, isolated environment, usually on a remote server, rather than on the user’s local device. Each isolated browser session renders web content but sends only a safe, interactive visual stream to the user’s device.
Remote Browser Isolation (RBI) allows the user to interact with websites as if they were local, but the actual web content never reaches the endpoint. This ensures that any malicious content, such as malware disguised as enticing offers or legitimate-looking downloads, encountered during browsing cannot affect the endpoint. By isolating web content in a secure, remote environment, RBI provides robust protection against various cyber threats, enhancing overall security and user confidence while browsing.
So, in essence, RBI works by allowing the user, whose device is most-likely managed by the IT admin, to carry on as usual except that a remote server sits as a knight between the user and the internet. It works in situations where web traffic deemed risky/suspicious need to be isolated, where drive-by downloads are a risk and where other exploits need to be kept at bay.
ESB, on the other hand, is more suited for the modern workforce since they are used to enable secure access to corporate resources by all unmanaged devices. It uses corporate security policies to control how data is handled within the browser. Features such as preventing copy-paste, blocking downloads/uploads, and restricting access to specific websites ensure that sensitive information remains protected.
Depending on the company’s needs or on the solution in use, various use cases can exist to address the secure handling of browser activities.
Some of these include:
- Unmanaged Devices – which generally include devices of remote workers, contractors, business partners, outsourcing partners etc. Organizations can provide access to essential websites, SaaS apps and other resources and employ the principle of least privilege by using ESBs.
- BYOD – ESBs facilitate this flexibility by providing a secure environment that isolates corporate web use from personal activities and protects company data on personal devices.
- VDI – Companies can now retire the delivery of virtual desktop images over networks since every user can use their own endpoint and safely interact with sensitive or corporate resources.
- Zero Trust Access – Controls for checking user identity, location, etc., can easily be deployed.
ESB solutions have created extensions that allow integration with any browser to deliver just about the same benefits with every browsing session. They can reduce the danger of browser data loss, stop phishing sites from stealing credentials, detect harmful extensions, and much more using its in-house developed Deep Session Analysis engine.
Here’s how this extension works:
Firstly, the platform will give the admin the power to make selections to determine what OS and what browser infrastructure(s) the extension will run on.
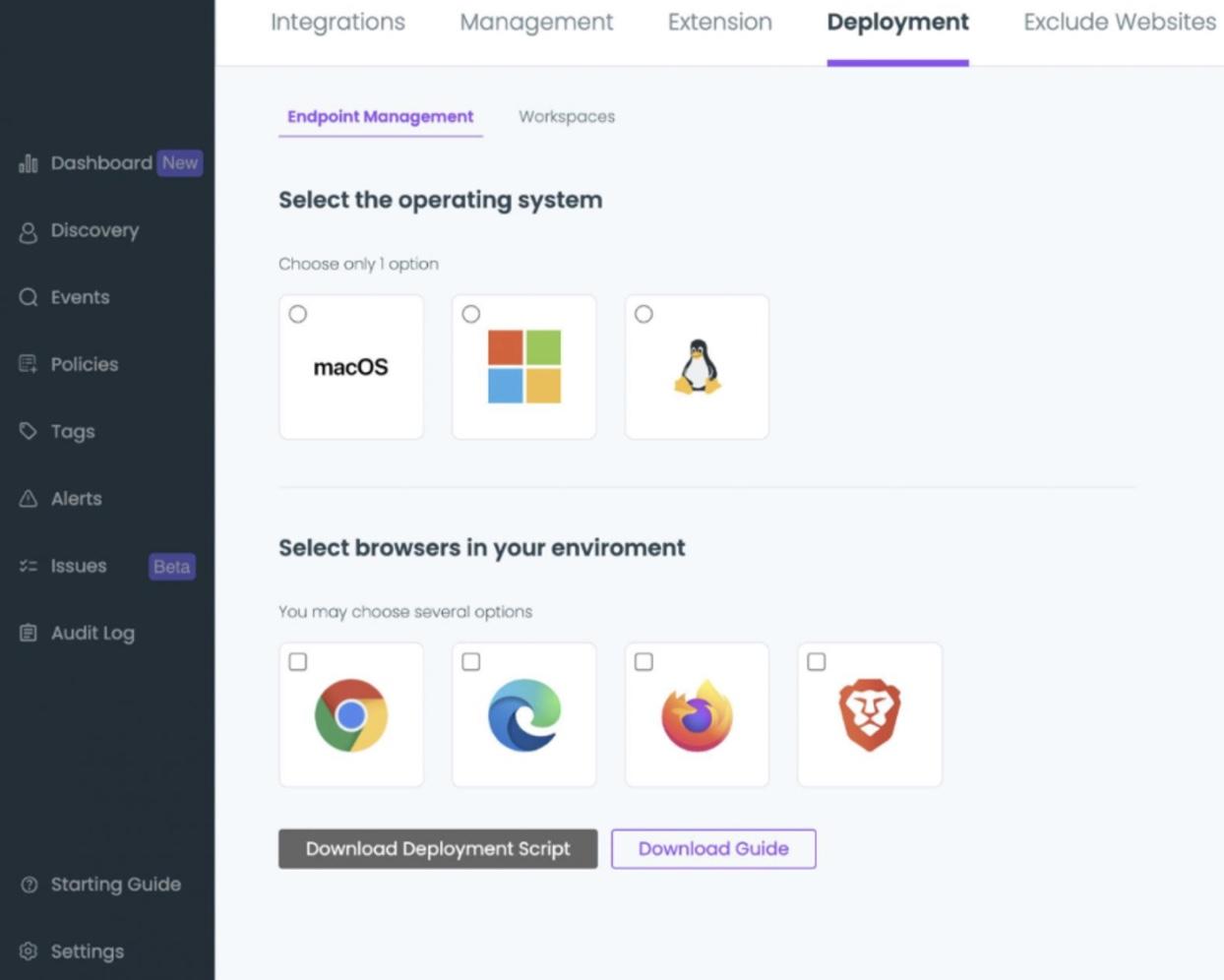
Upon successful deployment using provided scripts and guides, each browser can then be managed from a unified console. The admin exercises such as creating URL filtering, creating alerting and monitoring policies such as for copy and paste.
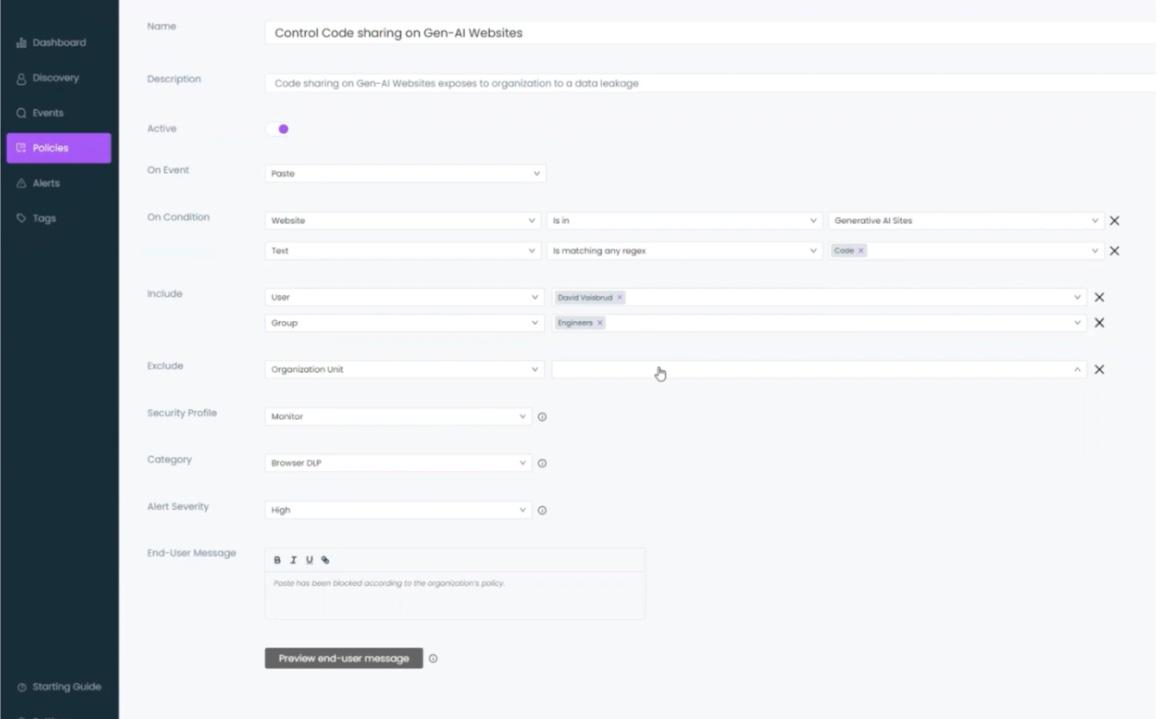
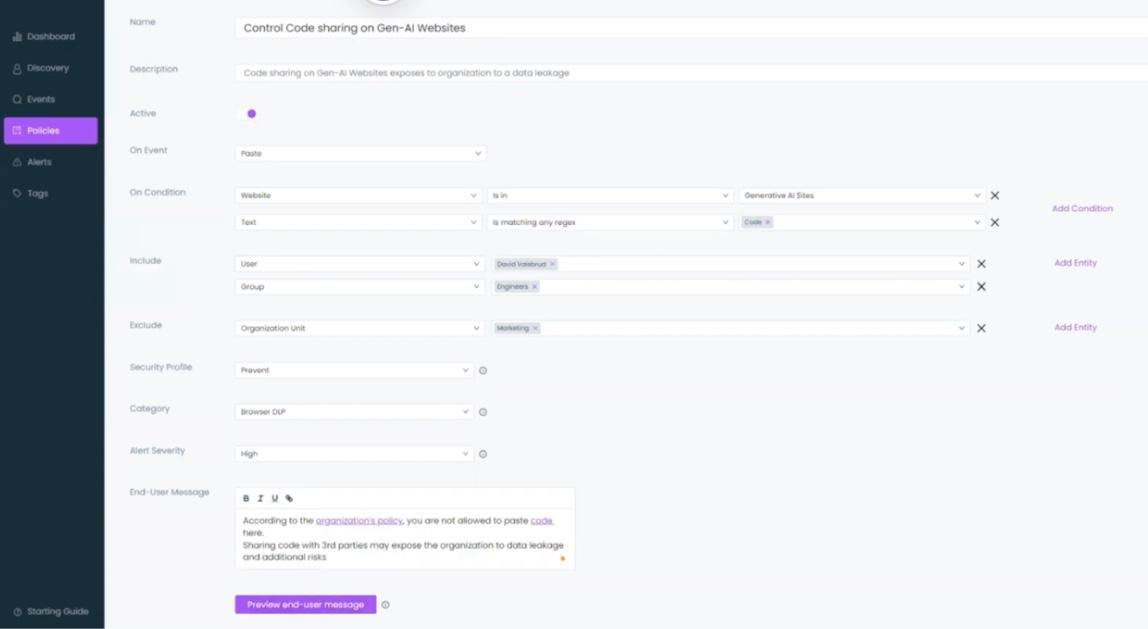
Data leakage prevention to generative AI platforms (e.g. ChatGPT, Bard) or any other LLM based application and blocking the installation of browser extensions using these AI platforms is one of such policies. This can be done by setting conditions which allow the browser extension to either monitor or prevent what data is pasted into these platforms. It also allows the admin to assign these policies to or exclude them from groups or based on roles to allow better management.
ESB solutions have created extensions that allow integration with any browser to deliver just about the same benefits with every browsing session. They can reduce the danger of browser data loss, stop phishing sites from stealing credentials, detect harmful extensions, and much more using its in-house developed Deep Session Analysis engine.
Here’s how this extension works:
Firstly, the platform will give the admin the power to make selections to determine what OS and what browser infrastructure(s) the extension will run on.

Upon successful deployment using provided scripts and guides, each browser can then be managed from a unified console. The admin exercises such as creating URL filtering, creating alerting and monitoring policies such as for copy and paste.
Data leakage prevention to generative AI platforms (e.g. ChatGPT, Bard) or any other LLM based application and blocking the installation of browser extensions using these AI platforms is one of such policies. This can be done by setting conditions which allow the browser extension to either monitor or prevent what data is pasted into these platforms. It also allows the admin to assign these policies to or exclude them from groups or based on roles to allow better management.

If the policy is set to monitor, alerts will be generated whenever users copy information onto a platform, but when it is set to prevent? Well, maximum security measures will provide a pop-up to let the user know that “paste” action is not enabled.
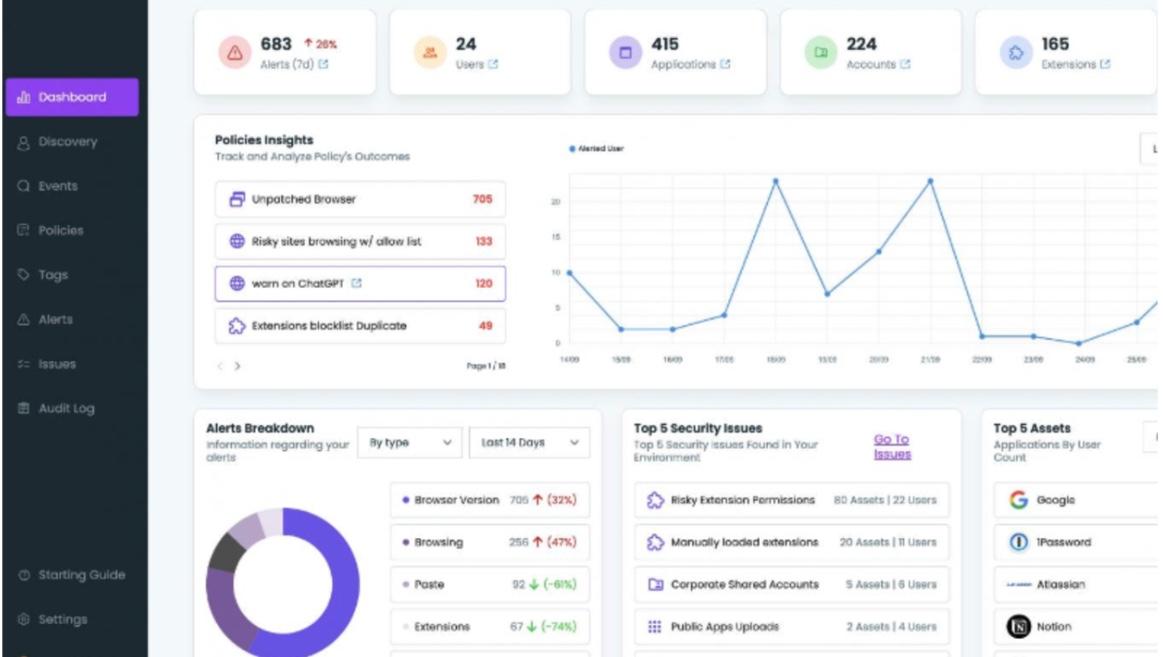
The dashboard can then be used to monitor all these security policies and use cases such as the number of unpatched browsers, security issues, what sites are considered risky even though they are in the “allowed” list, copy and paste activities etc.
To summarize, the benefits of adopting ESB into your cybersecurity strategy is multi-fold.
- Security in the age of GenAI – The ESB enforces strict data protection policies, ensuring that sensitive information is prevented from being leaked in the age of GenAI.
- Unified Security and Zero-Trust Internet Access – IT security and SecOps administrators can manage the ESB from a single, centralized console, simplifying the process of monitoring web activity, enforcing policies, shadow IT, SaaS sprawl and managing zero-trust internet access.
- Scalability – ESBs are scalable, allowing organizations to easily expand their security measures across various workforce devices, without requiring significant changes to the existing infrastructure. The use of ESB, naturally reduces the footprint on your security infrastructure such as Web Filtering, Proxy and parts of CASB functions whilst enforcing security controls irrespective of location.
If the policy is set to monitor, alerts will be generated whenever users copy information onto a platform, but when it is set to prevent? Well, maximum security measures will provide a pop-up to let the user know that “paste” action is not enabled.

The dashboard can then be used to monitor all these security policies and use cases such as the number of unpatched browsers, security issues, what sites are considered risky even though they are in the “allowed” list, copy and paste activities etc.

To summarize, the benefits of adopting ESB into your cybersecurity strategy is multi-fold.
- Security in the age of GenAI – The ESB enforces strict data protection policies, ensuring that sensitive information is prevented from being leaked in the age of GenAI.
- Unified Security and Zero-Trust Internet Access – IT security and SecOps administrators can manage the ESB from a single, centralized console, simplifying the process of monitoring web activity, enforcing policies, shadow IT, SaaS sprawl and managing zero-trust internet access.
- Scalability – ESBs are scalable, allowing organizations to easily expand their security measures across various workforce devices, without requiring significant changes to the existing infrastructure. The use of ESB, naturally reduces the footprint on your security infrastructure such as Web Filtering, Proxy and parts of CASB functions whilst enforcing security controls irrespective of location.
See also:



