Privileged access management (PAM) and identity and access management (IAM) are two essential components of any security strategy. They help organizations control who can access what, when, where, and how, and protect sensitive data and critical infrastructure from unauthorized access or malicious actions. However, traditional PAM and IAM policies are often static, complex, and inefficient, especially in the face of dynamic and diverse environments such as remote work, DevOps, and the cloud. That’s why more and more organizations are adopting just-in-time (JIT) and just-enough-administration (JEA) approaches to PAM and IAM.
In this blog post, we will explore how JIT and JEA are transforming privileged access workflows in different scenarios and what benefits they offer for security, productivity, and compliance.
Privileged access management (PAM) and identity and access management (IAM) are two essential components of any security strategy. They help organizations control who can access what, when, where, and how, and protect sensitive data and critical infrastructure from unauthorized access or malicious actions. However, traditional PAM and IAM policies are often static, complex, and inefficient, especially in the face of dynamic and diverse environments such as remote work, DevOps, and the cloud. That’s why more and more organizations are adopting just-in-time (JIT) and just-enough-administration (JEA) approaches to PAM and IAM.
In this blog post, we will explore how JIT and JEA are transforming privileged access workflows in different scenarios and what benefits they offer for security, productivity, and compliance.
What is JIT and JEA?
JIT is a borrowed concept from business, representing an inventory management method that focuses on keeping as little inventory on hand as possible. Instead of stockpiling products and raw materials, JIT orders small shipments to replace inventory as it forecasts and fulfills orders. Similarly, JIT for PAM means that users request and receive privileges only when they need them and only for a limited time. This way, JIT reduces the number of privileged accounts and credentials and minimizes the exposure of sensitive data and resources.
JEA is a security technology that enables users to perform administrative tasks without having full administrative rights. Instead of granting users broad and permanent privileges, JEA assigns them specific roles and capabilities that allow them to perform only the tasks they are authorized to do. This way, JEA reduces the attack surface and limits the damage that malicious or compromised users can do.
The typical workflow of JIT and JEA can be summarized as follows:
- A user needs to perform a task that requires privileged access, such as updating a server, installing a software, or accessing a database.
- The user requests the necessary privileges from a central authority, such as a PAM system, a manager, or a workflow automation tool.
- The authority verifies the user’s identity, role, and authorization and grants the user the appropriate privileges for a predefined duration.
- The user performs the task using the granted privileges, which are monitored and audited by the authority.
- The user returns or revokes the privileges, or the privileges expire automatically after the duration ends.
What is JIT and JEA?
Just-in-time (JIT) and just-enough-administration (JEA) are two approaches to privileged access management (PAM) that aim to reduce the risk and complexity of granting and managing privileges. They are based on the principle of least privilege, which states that users should have the minimum level of access required to perform their tasks.
JIT is a borrowed concept from business, representing an inventory management method that focuses on keeping as little inventory on hand as possible. Instead of stockpiling products and raw materials, JIT orders small shipments to replace inventory as it forecasts and fulfills orders. Similarly, JIT for PAM means that users request and receive privileges only when they need them and only for a limited time. This way, JIT reduces the number of privileged accounts and credentials and minimizes the exposure of sensitive data and resources.
JEA is a security technology that enables users to perform administrative tasks without having full administrative rights. Instead of granting users broad and permanent privileges, JEA assigns them specific roles and capabilities that allow them to perform only the tasks they are authorized to do. This way, JEA reduces the attack surface and limits the damage that malicious or compromised users can do.
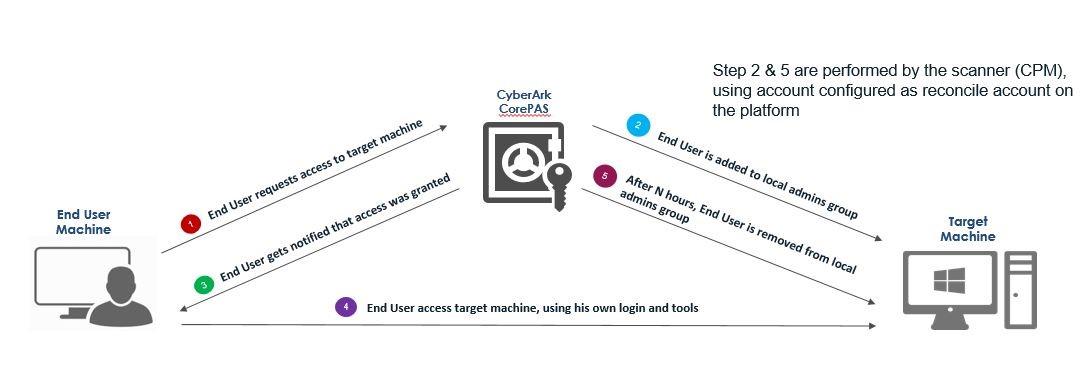
The typical workflow of JIT and JEA can be summarized as follows:
- A user needs to perform a task that requires privileged access, such as updating a server, installing a software, or accessing a database.
- The user requests the necessary privileges from a central authority, such as a PAM system, a manager, or a workflow automation tool.
- The authority verifies the user’s identity, role, and authorization and grants the user the appropriate privileges for a predefined duration.
- The user performs the task using the granted privileges, which are monitored and audited by the authority.
- The user returns or revokes the privileges, or the privileges expire automatically after the duration ends.
How JIT/JEA Transform Privileged Access Workflows
Consider a scenario where a cloud administrator needs to manage many virtual machines and services in a cloud environment. Instead of having a single and powerful privileged account, the administrator uses JIT and JEA to access only the resources that are needed for each task. The JIT and JEA tools use policies and attributes to determine the appropriate level and duration of access for each resource based on the administrator’s identity, role, context, and risk level. The JIT and JEA tools also provide visibility and control over the administrator’s activities for governance and remediation purposes.
Similarly, suppose a remote worker needs to access a server in the cloud to perform a maintenance task. Instead of having a permanent privileged account, the worker requests JIT access from a PAM system, which verifies the worker’s identity, role, and authorization. The PAM system grants the worker a temporary and time-limited credential, which is automatically revoked after the task is completed. The worker’s actions are also recorded and logged by the PAM system for auditing and compliance purposes.
These are just some of the scenarios where JIT and JEA can transform privileged access workflows. These two concepts can also provide several benefits, such as:
- Reducing the attack surface and the risk of data breaches by minimizing the number and exposure of privileged accounts and credentials
- Improving productivity and efficiency by enabling users to access only what they need when they need it, without compromising security or compliance
- Enforcing the principle of least privilege and aligning access policies with business needs and objectives
- Enhancing visibility and accountability by monitoring and auditing privileged access and activities
- Simplifying management and administration by automating and streamlining privileged access workflows
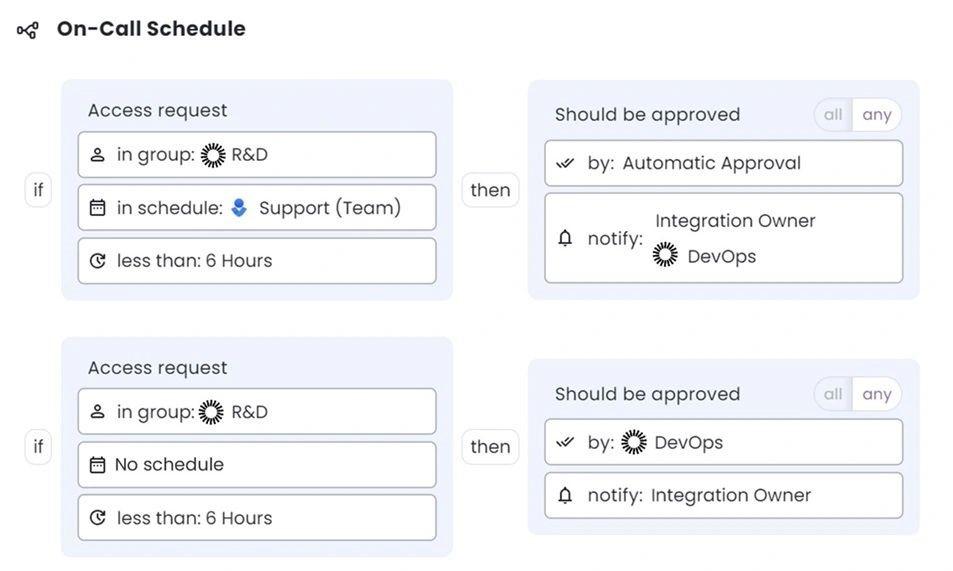
How JIT/JEA Transform Privileged Access Workflows
JIT and JEA are more than just theoretical concepts but practical solutions that can be applied in various scenarios and domains.
Consider a scenario where a cloud administrator needs to manage many virtual machines and services in a cloud environment. Instead of having a single and powerful privileged account, the administrator uses JIT and JEA to access only the resources that are needed for each task. The JIT and JEA tools use policies and attributes to determine the appropriate level and duration of access for each resource based on the administrator’s identity, role, context, and risk level. The JIT and JEA tools also provide visibility and control over the administrator’s activities for governance and remediation purposes.

Similarly, suppose a remote worker needs to access a server in the cloud to perform a maintenance task. Instead of having a permanent privileged account, the worker requests JIT access from a PAM system, which verifies the worker’s identity, role, and authorization. The PAM system grants the worker a temporary and time-limited credential, which is automatically revoked after the task is completed. The worker’s actions are also recorded and logged by the PAM system for auditing and compliance purposes.
These are just some of the scenarios where JIT and JEA can transform privileged access workflows. These two concepts can also provide several benefits, such as:
- Reducing the attack surface and the risk of data breaches by minimizing the number and exposure of privileged accounts and credentials
- Improving productivity and efficiency by enabling users to access only what they need when they need it, without compromising security or compliance
- Enforcing the principle of least privilege and aligning access policies with business needs and objectives
- Enhancing visibility and accountability by monitoring and auditing privileged access and activities
- Simplifying management and administration by automating and streamlining privileged access workflows
How to Augment JIT and JEA With Other Security Practices

- Implementing PAM with JIT rather than creating new JIT accounts: PAM tools can help manage the lifecycle of privileged accounts and credentials and integrate with JIT solutions to grant temporary and dynamic access. This way, organizations can avoid creating new accounts that might be forgotten or misused and leverage existing identity and access management (IAM) policies and workflows.
- Recording and logging the JIT privileged access in a central location: Logging and auditing are essential for monitoring and reviewing the activities of privileged users and detecting any anomalies or incidents. Organizations should record and log the JIT access requests, approvals, denials, and revocations, as well as the actions performed by the users during the privileged sessions. These logs should be stored in a secure and centralized location and analyzed by security tools or experts.
- Ensuring more granular policies for elevated access: JIT and JEA can help limit the scope and duration of privileges, but they still depend on the definition and enforcement of access policies. Organizations should ensure these policies are as granular and specific as possible, based on the user’s identity, role, context, and risk level. For example, a user might need different access levels depending on the time of day, the location, the device, the network, the resource, or the task.
- Combining role-based access control (RBAC) and attribute-based access control (ABAC): RBAC and ABAC are two models for defining and assigning user access rights. RBAC is based on the user’s role or function in the organization, while ABAC is based on the user’s attributes or characteristics, such as department, project, seniority, etc. By combining RBAC and ABAC, organizations can achieve more flexibility and granularity in their access policies, and align them with the business needs and objectives.
- Inventorizing assets and marking existing high-risk vulnerabilities: JIT and JEA can help reduce the exposure of privileged assets, but they cannot prevent or mitigate the vulnerabilities that might exist in those assets. Organizations should inventorize their assets and identify the ones that have high-risk vulnerabilities, such as outdated software, misconfigurations, or weak passwords. These assets should be prioritized for remediation or protection and marked with tags or labels that can trigger stricter access policies or alerts.
How to Augment JIT and JEA With Other Security Practices

- Implementing PAM with JIT rather than creating new JIT accounts: PAM tools can help manage the lifecycle of privileged accounts and credentials and integrate with JIT solutions to grant temporary and dynamic access. This way, organizations can avoid creating new accounts that might be forgotten or misused and leverage existing identity and access management (IAM) policies and workflows.
- Recording and logging the JIT privileged access in a central location: Logging and auditing are essential for monitoring and reviewing the activities of privileged users and detecting any anomalies or incidents. Organizations should record and log the JIT access requests, approvals, denials, and revocations, as well as the actions performed by the users during the privileged sessions. These logs should be stored in a secure and centralized location and analyzed by security tools or experts.
- Ensuring more granular policies for elevated access: JIT and JEA can help limit the scope and duration of privileges, but they still depend on the definition and enforcement of access policies. Organizations should ensure these policies are as granular and specific as possible, based on the user’s identity, role, context, and risk level. For example, a user might need different access levels depending on the time of day, the location, the device, the network, the resource, or the task.
- Combining role-based access control (RBAC) and attribute-based access control (ABAC): RBAC and ABAC are two models for defining and assigning user access rights. RBAC is based on the user’s role or function in the organization, while ABAC is based on the user’s attributes or characteristics, such as department, project, seniority, etc. By combining RBAC and ABAC, organizations can achieve more flexibility and granularity in their access policies, and align them with the business needs and objectives.
- Inventorizing assets and marking existing high-risk vulnerabilities: JIT and JEA can help reduce the exposure of privileged assets, but they cannot prevent or mitigate the vulnerabilities that might exist in those assets. Organizations should inventorize their assets and identify the ones that have high-risk vulnerabilities, such as outdated software, misconfigurations, or weak passwords. These assets should be prioritized for remediation or protection and marked with tags or labels that can trigger stricter access policies or alerts.
Conclusion
Conclusion
See also:

