ICS MITRE ATT&CK Technique
ICS/OT networks continue to be targeted by cyber-attacks as the stakes are higher and the damage is greater, compared to enterprise networks. MITRE has recently published its first ICS MITRE framework which highlight the differences between ICS /OT and IT network in term of attack tactics and techniques used by adversaries. The publishing of the framework recognizes the growing concern of cyber threats on OT environment. The MITRE ATT&CK is a global knowledge base framework that could be easily accessed by organization and individuals.
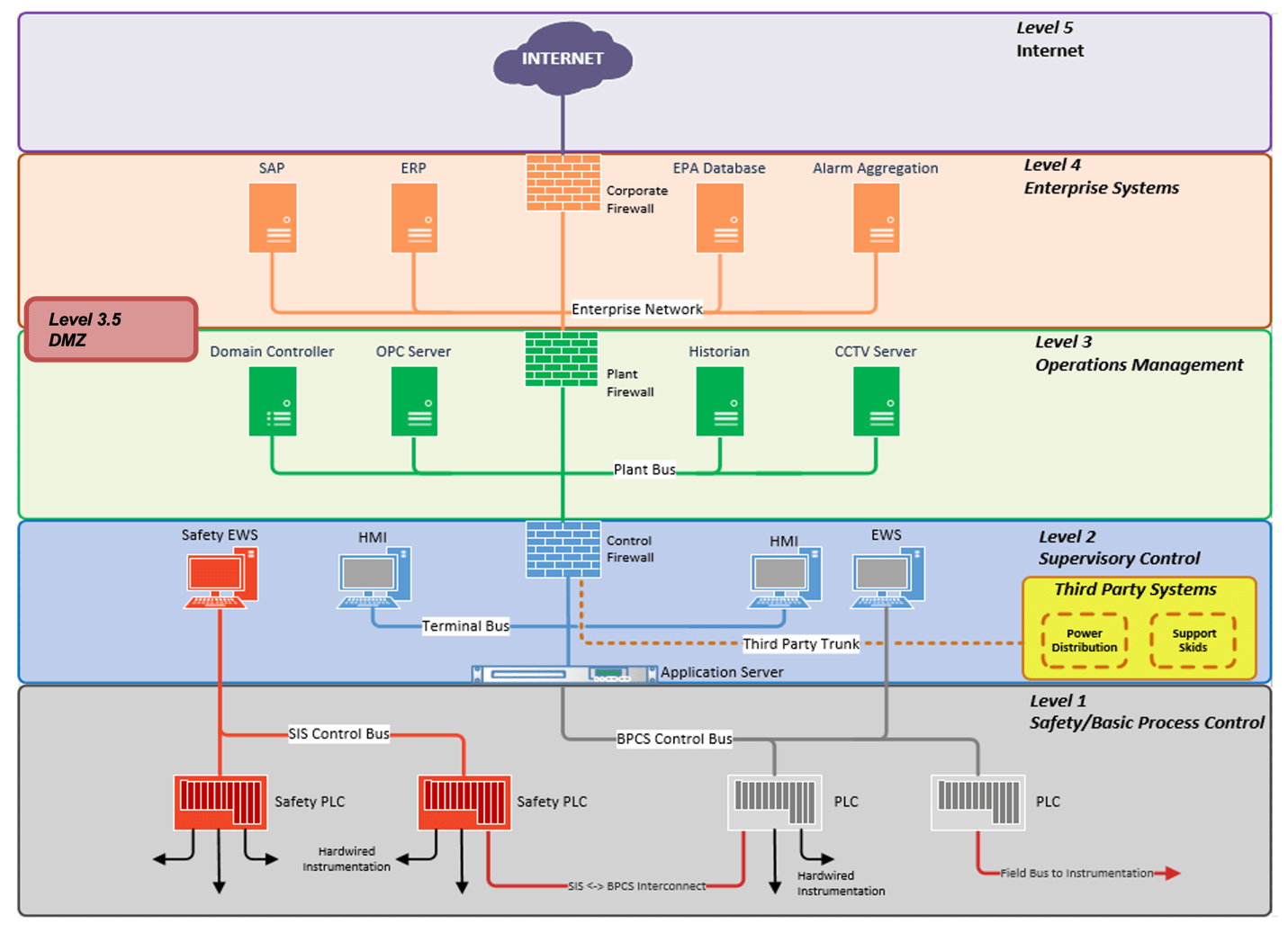
- Level 0 Basic Control such Sensors, Actuators, Pumps, Valves etc. from the field mostly hard-wired devices connected to the field
- Level 1 DCS Controllers and PLC
- Level 2 Engineering Workstation (EWS) and HMI
- Level 3 ICS Management Applications, OPC Servers, Historian
- Level 3.5 Patch Management and Windows System Updates and Anti-Virus Server
- Level 4 Business Network, Business Intelligence
-
Level 5 Internet Edge
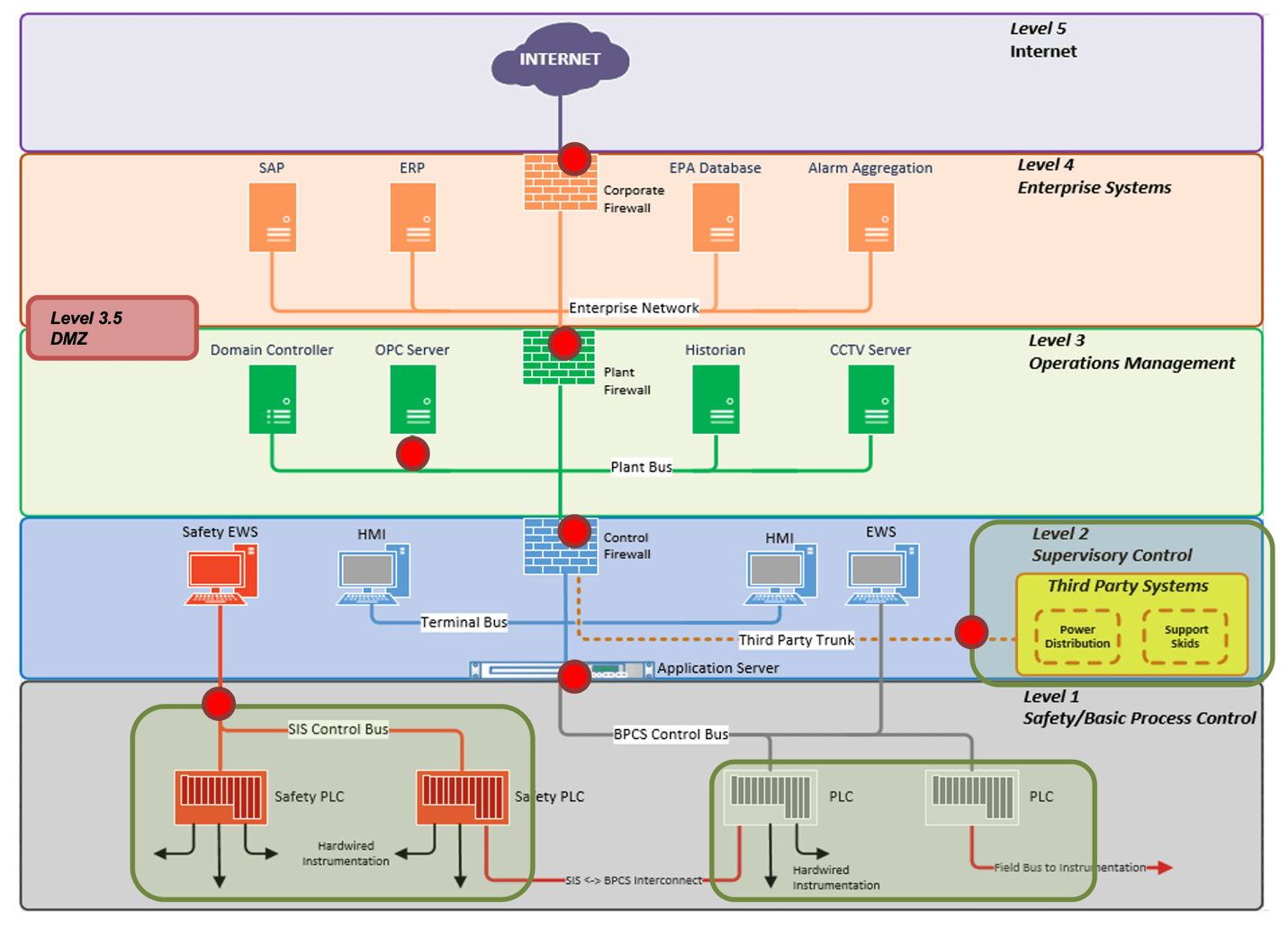
The Purdue model ensures secure network architecture by defining security zones and isolating networks or creating segments based on industrial process and its criticality in terms of safety and functionality; thereby minimizing cyber risks should an attack occur at the business network or within the plant itself.
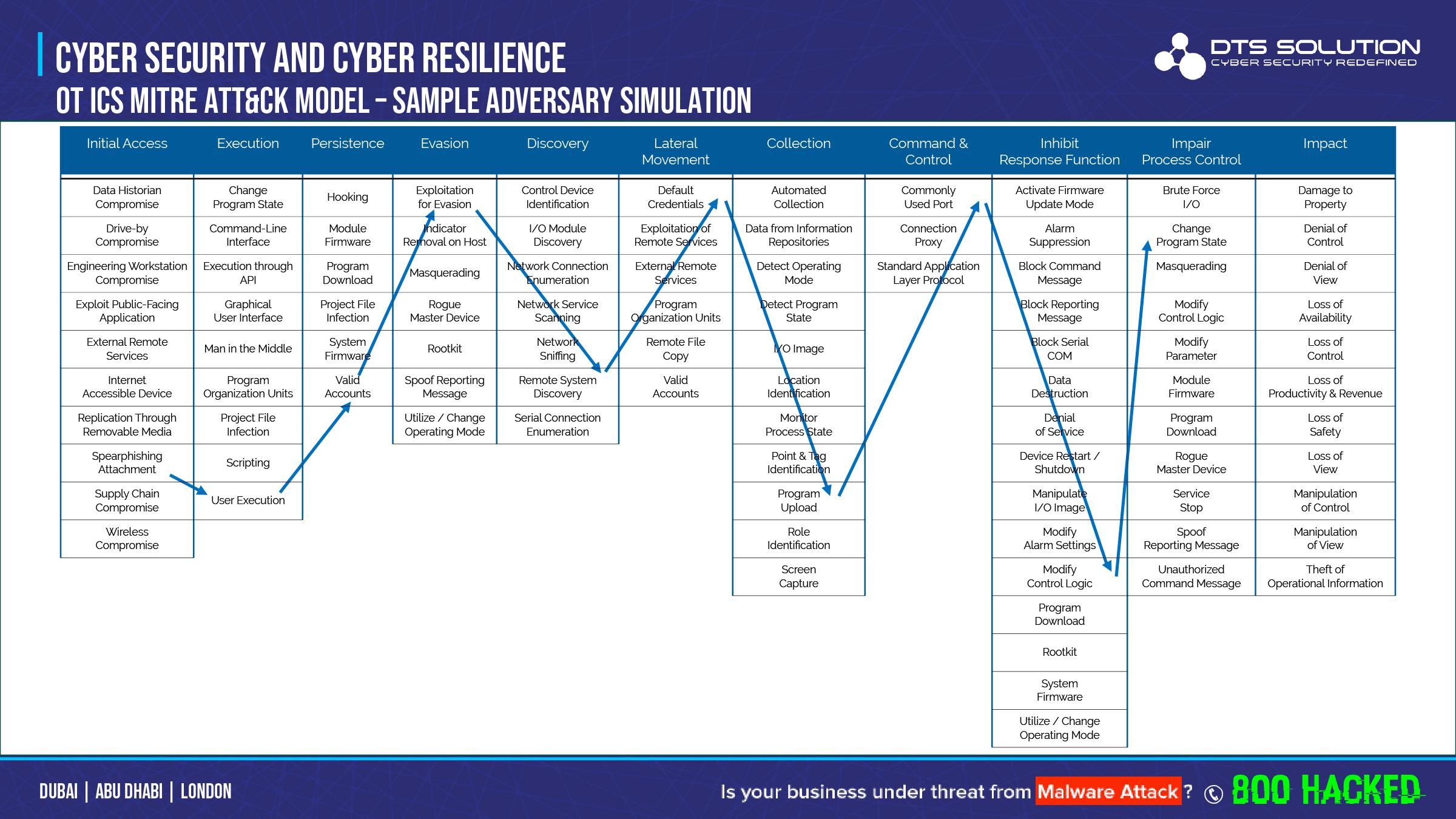
Securing the attack surface within the ICS environment using various hardening techniques will ensure defense-in-depth security. The ICS MITRE ATT&CK technique has defined eleven techniques is to how an adversary could attack OT network;
- Initial Access: The attacker needs to establish a foot hold on the ics network
- Execution: The attacker executes a code on the network
- Persistence: The attacker continues to maintain his foothold on the network
- Evasion: The attacker continues to remain hidden in the network and avoid to be detected
- Discovery: The attacker use techniques to survey the ics network
- Lateral movement: The attacker use techniques to enter and control the network
- Collection: The attacker collects information about the ICS system that will aid him in launching attack
- Command and Control: The adversary is trying to communicate with and control compromised systems, controllers, and platforms with access to your ICS environment.
- Inhibit response function: The adversary is trying to prevent your safety, protection, quality assurance, and operator intervention functions from responding to a failure, hazard, or unsafe state.
- Impair process control: The adversary is trying to manipulate, disable, or damage physical control processes.
- Impact: The adversary is trying to manipulate, interrupt, or destroy your ICS systems, data, and their surrounding environment.
- Identification of technical gaps in ICS cyber security controls and creation of defensive strategies to identify attacks during each phases of the attack-lifecycle (tactics in ICS MITRE ATT&CK)
- Development of effective ICS/OT monitoring use cases for the SOC / SIEM – ensuring that specific security events mapped to the ICS MITRE ATT&CK techniques trigger an alert.
- Develop effective ICS threat intelligence and ICS incident triage and response activities by understand how malware compromise occurs and its lifecycle
- Help train field and OT field workers and site operators in understanding of ICS threat behaviors
-
Help your red, blue and purple team to perform adversary emulation; testing of security controls and defenses in an OT testbed if you have one
It’s vital for international standard, security vendors, consulting and advisory firms that regulates ICS cyber security to adopt such a framework to improve overall cyber security posture.
ICS MITRE ATT&CK Technique
- Level 0 Basic Control such Sensors, Actuators, Pumps, Valves etc. from the field mostly hard-wired devices connected to the field
- Level 1 DCS Controllers and PLC
- Level 2 Engineering Workstation (EWS) and HMI
- Level 3 ICS Management Applications, OPC Servers, Historian
- Level 3.5 Patch Management and Windows System Updates and Anti-Virus Server
- Level 4 Business Network, Business Intelligence
- Level 5 Internet Edge
- Initial Access: The attacker needs to establish a foot hold on the ics network
- Execution: The attacker executes a code on the network
- Persistence: The attacker continues to maintain his foothold on the network
- Evasion: The attacker continues to remain hidden in the network and avoid to be detected
- Discovery: The attacker use techniques to survey the ics network
- Lateral movement: The attacker use techniques to enter and control the network
- Collection: The attacker collects information about the ICS system that will aid him in launching attack
- Command and Control: The adversary is trying to communicate with and control compromised systems, controllers, and platforms with access to your ICS environment.
- Inhibit response function: The adversary is trying to prevent your safety, protection, quality assurance, and operator intervention functions from responding to a failure, hazard, or unsafe state.
- Impair process control: The adversary is trying to manipulate, disable, or damage physical control processes.
- Impact: The adversary is trying to manipulate, interrupt, or destroy your ICS systems, data, and their surrounding environment.
- Identification of technical gaps in ICS cyber security controls and creation of defensive strategies to identify attacks during each phases of the attack-lifecycle (tactics in ICS MITRE ATT&CK)
- Development of effective ICS/OT monitoring use cases for the SOC / SIEM – ensuring that specific security events mapped to the ICS MITRE ATT&CK techniques trigger an alert.
- Develop effective ICS threat intelligence and ICS incident triage and response activities by understand how malware compromise occurs and its lifecycle
- Help train field and OT field workers and site operators in understanding of ICS threat behaviors
- Help your red, blue and purple team to perform adversary emulation; testing of security controls and defenses in an OT testbed if you have one
It’s vital for international standard, security vendors, consulting and advisory firms that regulates ICS cyber security to adopt such a framework to improve overall cyber security posture.
See also: