- Audit– is used for assessing the compliance of information security function against a given a standard or guideline.
- Gap assessment– is used for assessing the compliance of information security function against a given a standard or guideline.
- Risk assessment– is used for assessing the compliance of information security function against a given a standard or guideline.
If you have ever had a hard time deciding which one to pick I advise you to read further.
- Audit– is used for assessing the compliance of information security function against a given a standard or guideline.
- Gap assessment– is used for assessing the compliance of information security function against a given a standard or guideline.
- Risk assessment– is used for assessing the compliance of information security function against a given a standard or guideline.
If you have ever had a hard time deciding which one to pick I advise you to read further.
Information Security / Cyber Security Audit
Cybersecurity is concerned with protecting digital assets, meaning everything from networks to hardware and information that is processes, stored or transported by internetworked information systems.
Information Security / Cyber Security Audit
Cybersecurity is concerned with protecting digital assets, meaning everything from networks to hardware and information that is processes, stored or transported by internetworked information systems.
Information Security / Cyber Security Gap Assessment
Hopefully there are no more doubts now, and you know when to ask for an audit and when to ask for a gap assessment. The difference between them will save you money and prevent you from reading an audit report saying there are missing policies, procedures and processes and you have to implement them so they can be audited, which by the way is a true statement.
Hopefully there are no more doubts now, and you know when to ask for an audit and when to ask for a gap assessment. The difference between them will save you money and prevent you from reading an audit report saying there are missing policies, procedures and processes and you have to implement them so they can be audited, which by the way is a true statement.
Information Security / Cyber Security Risk Assessment
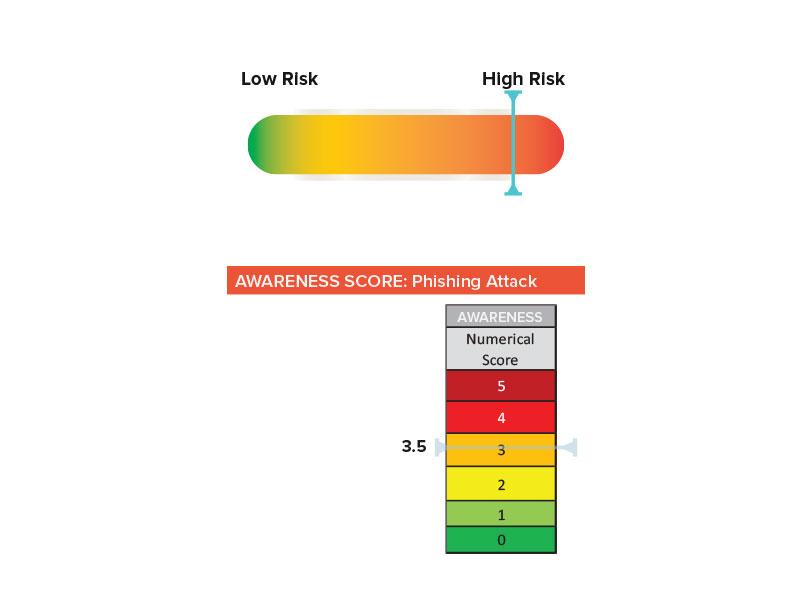
A risk assessment should provide a clear image of current threats, vulnerabilities and their exploitability (these three equal risk), assess the effectiveness of controls in place, estimate the impact and likelihood of the risk and calculate the residual risk.
Information Security / Cyber Security Risk Assessment
Now let’s bring it all together on the topic of risk:
- Risk Management Policy encompassing scope, requirements, responsibilities and criteria for accepting risks
- Risk Assessment and Treatment Methodology: process and procedure describing step by step the entire process
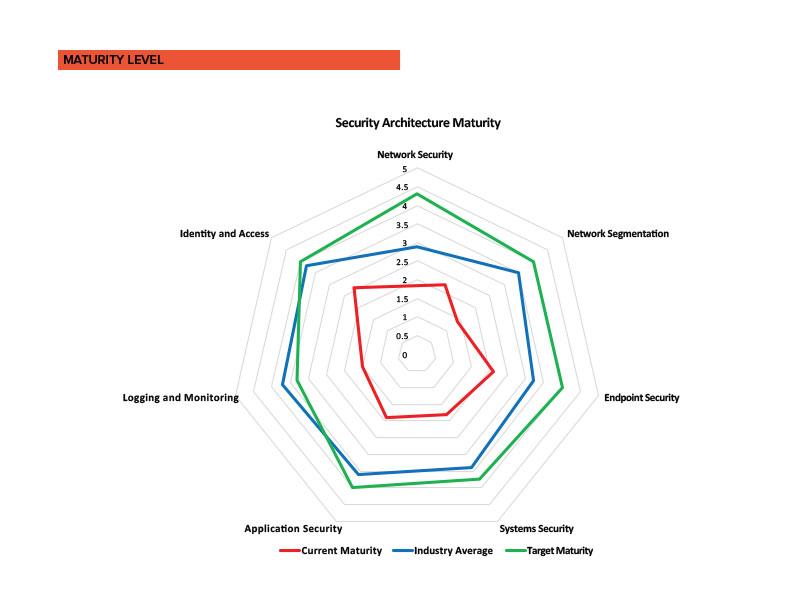
A gap assessment should assess the maturity of risk management processes and provide the level of maturity for each process step.
Now let’s bring it all together on the topic of risk:
- Risk Management Policy encompassing scope, requirements, responsibilities and criteria for accepting risks
- Risk Assessment and Treatment Methodology: process and procedure describing step by step the entire process
A gap assessment should assess the maturity of risk management processes and provide the level of maturity for each process step.
See also: