- Security tests
- Security assessment and review
- Security audit
Following security best practices, a complete IT security assessment should be performed during a risk assessment at enterprise level and after any significant changes in the IT infrastructure and information systems.
- Security tests
- Security assessment and review
- Security audit
Following security best practices, a complete IT security assessment should be performed during a risk assessment at enterprise level and after any significant changes in the IT infrastructure and information systems.
Security Tests
- Availability of security testing resources
- Criticality of the systems and applications protected by the tested controls
- Sensitivity of information contained on tested systems and applications
- Likelihood of a technical failure of the mechanism implementing the control
- Likelihood of a misconfiguration of the control that would jeopardize security
- Risk that the system will come under attack
- Rate of change of the control configuration
- Other changes in the technical environment that may affect the control performance
- Difficulty and time required to perform a control test
- Impact of the test on normal business operations
After assessing each of these factors, security teams design and validate a comprehensive assessment and testing strategy. This strategy may include frequent automated tests (vulnerability scans) supplemented by infrequent manual tests (penetration tests).
Security Tests
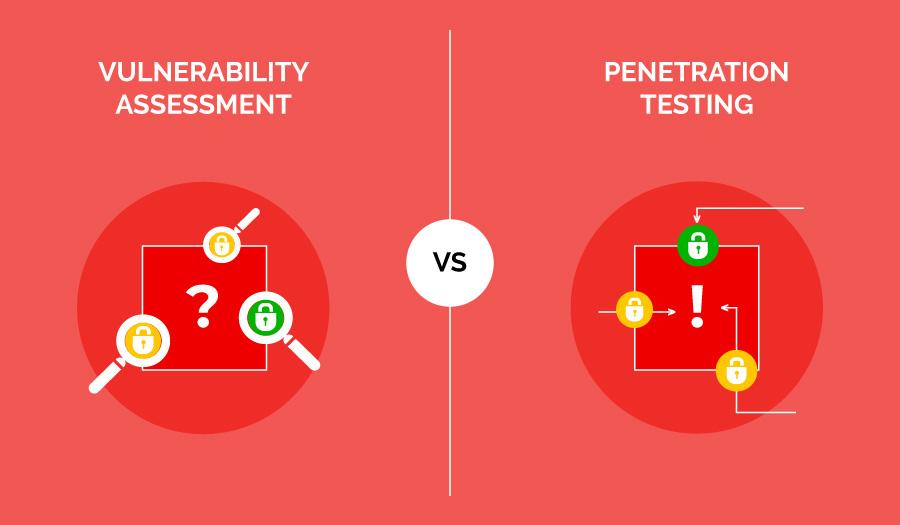
- Vulnerability assessment:
- Endpoint IP Discovery and Network Leakage Detection
- Rogue and Unknown Network Detection
- Penetration testing:
- Network and system configuration reviews
- Environment vulnerability assessments
- Physical Security Review
- Availability of security testing resources
- Criticality of the systems and applications protected by the tested controls
- Sensitivity of information contained on tested systems and applications
- Likelihood of a technical failure of the mechanism implementing the control
- Likelihood of a misconfiguration of the control that would jeopardize security
- Risk that the system will come under attack
- Rate of change of the control configuration
- Other changes in the technical environment that may affect the control performance
- Difficulty and time required to perform a control test
- Impact of the test on normal business operations
After assessing each of these factors, security teams design and validate a comprehensive assessment and testing strategy. This strategy may include frequent automated tests (vulnerability scans) supplemented by infrequent manual tests (penetration tests).
Vulnerability Assessment
Please visit the Red Team page for methodologies of the various technical assessments performed by DTS Solution.
Vulnerability Assessment
Please visit the Red Team page for methodologies of the various technical assessments performed by DTS Solution.
Penetration Testing
- Network – aims at identifying systems on the network with open ports and discovering known security flaws on those systems
- Mobile applications – aims at searching for known vulnerabilities in mobile applications (OWASP Top 10 Mobile Risks)
- Wireless - aims at searching for known vulnerabilities in WiFi systems, Bluetooth, ZigBee, Z-Wave, DECT, RFID, NFC, contactless smart cards, and proprietary wireless systems
- Consultant background check and certifications validation:
- For lead penetration tester:
- Minimum 5 years of experience
- One or more of the following certifications: CISSP, CISM, CISA, GIAC GSLC
- Either GIAC GPEN or offensive security OSCP/equivalent certification
- For penetration tester:
- Minimum 3 years of experience
- One of the following certifications: CISSP, GCIH, GIAC GPEN, or offensive security OSCP/equivalent certification
- Define very clearly the scope of testing:
- The scope will detail the objective, scale, depth and methodology to be used. If CII entity, the methodology to be used is NESA UAE Security Penetration Testing Mandatory Guideline. If non-CII entity, please visit the Red Team page for methodologies of the various technical assessments on the offensive domain.
- The scope shall determine how much information is given to the penetration testing team:
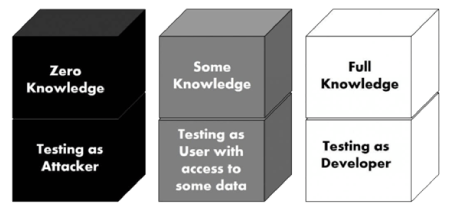
- Black Box: Very limited information: a zero-knowledge team knows nothing about the target site except for publicly available information, such as domain name and company address. It’s as if they are looking at the target as a black box and have no idea what is within the box until they start probing. An attack by a zero-knowledge team closely resembles a real external attack because all information about the environment must be obtained from scratch.
- Gray Box: Limited information: also known as partial knowledge tests, these are sometimes chosen to balance the advantages and disadvantages of white and black box penetration tests (mostly costs and time constraints). The team may be given information on the network design and configuration details so that they can focus on attacks and vulnerabilities for specific targets.
- White Box: All information: a full-knowledge team has full access to all aspects of the target environment. They know what patches and upgrades are installed, and the exact configuration of all relevant devices. If the target is an application, they would have access to the source code. It provides the attackers with detailed information about the systems they target.
- Notify NESA UAE if CII entity:
- The company name of the third party that will perform penetration testing, the scope of the testing, and the team members involved
- Wait for approval (beware that NESA may reject some requests)
- Obtain security clearance for the team members involved
- Be aware of and approve the scanning tools to be used by the third party
Penetration Testing
- Network – aims at identifying systems on the network with open ports and discovering known security flaws on those systems
- Mobile applications – aims at searching for known vulnerabilities in mobile applications (OWASP Top 10 Mobile Risks)
- Wireless - aims at searching for known vulnerabilities in WiFi systems, Bluetooth, ZigBee, Z-Wave, DECT, RFID, NFC, contactless smart cards, and proprietary wireless systems
- Consultant background check and certifications validation:
- For lead penetration tester:
- Minimum 5 years of experience
- One or more of the following certifications: CISSP, CISM, CISA, GIAC GSLC
- Either GIAC GPEN or offensive security OSCP/equivalent certification
- For penetration tester:
- Minimum 3 years of experience
- One of the following certifications: CISSP, GCIH, GIAC GPEN, or offensive security OSCP/equivalent certification
- Define very clearly the scope of testing:
- The scope will detail the objective, scale, depth and methodology to be used. If CII entity, the methodology to be used is NESA UAE Security Penetration Testing Mandatory Guideline. If non-CII entity, please visit the Red Team page for methodologies of the various technical assessments on the offensive domain.
- The scope shall determine how much information is given to the penetration testing team:
- Black Box: Very limited information: a zero-knowledge team knows nothing about the target site except for publicly available information, such as domain name and company address. It’s as if they are looking at the target as a black box and have no idea what is within the box until they start probing. An attack by a zero-knowledge team closely resembles a real external attack because all information about the environment must be obtained from scratch.
- Gray Box: Limited information: also known as partial knowledge tests, these are sometimes chosen to balance the advantages and disadvantages of white and black box penetration tests (mostly costs and time constraints). The team may be given information on the network design and configuration details so that they can focus on attacks and vulnerabilities for specific targets.
- White Box: All information: a full-knowledge team has full access to all aspects of the target environment. They know what patches and upgrades are installed, and the exact configuration of all relevant devices. If the target is an application, they would have access to the source code. It provides the attackers with detailed information about the systems they target.
- Notify NESA UAE if CII entity:
- The company name of the third party that will perform penetration testing, the scope of the testing, and the team members involved
- Wait for approval (beware that NESA may reject some requests)
- Obtain security clearance for the team members involved
- Be aware of and approve the scanning tools to be used by the third party
Security Assessments
- Security architecture, design and solutions review
- Security review of web-based systems:
- Applications security
- Database security
- Availability Assessment
- Distributed Denial of Service (DDoS) Protection
- Web Portal Availability
Security Assessments
- Security architecture, design and solutions review
- Security review of web-based systems:
- Applications security
- Database security
- Availability Assessment
- Distributed Denial of Service (DDoS) Protection
- Web Portal Availability
Security Architecture Review
- Review of network topology, network segmentation, and of security controls and devices deployed across the OSI networking framework
- Client-based infrastructure (e.g., applets, local caches)
- Server-based infrastructure (e.g., data flow control)
- Database security (e.g., inference, aggregation, data mining, data analytics, warehousing)
- Large-scale parallel data systems
- Distributed systems (e.g., cloud computing, grid computing, peer to peer)
- Cryptographic systems
- Industrial control systems (e.g., SCADA)
Security Architecture Review
- Review of network topology, network segmentation, and of security controls and devices deployed across the OSI networking framework
- Client-based infrastructure (e.g., applets, local caches)
- Server-based infrastructure (e.g., data flow control)
- Database security (e.g., inference, aggregation, data mining, data analytics, warehousing)
- Large-scale parallel data systems
- Distributed systems (e.g., cloud computing, grid computing, peer to peer)
- Cryptographic systems
- Industrial control systems (e.g., SCADA)
Security Review of Web-Based Systems
- Source code review: pair programming and peer reviews (development phase)
- Software testing: static testing, dynamic testing, interface testing, and misuse case testing (integration and testing phase)
- Security review (production phase)
- Source code review - is the process of auditing the source code of a web application to verify that the proper security controls are present to mitigate security weaknesses and known vulnerabilities at the source code level (e.g. XML, OWASP Top 10 Application Risks), they work as intended, and that they have been invoked in all the right places.
- Web server security review – is the process of auditing the protection of information assets that can be accessed from a web server connected to the Internet.
- Back end database security review – is the process of auditing the collective measures used to protect and secure a database from illegitimate use and malicious threats and attacks. It is a broad term that includes a multitude of processes, tools and methodologies that ensure security within a database environment.
- Security code review – is the method of assuring the security of the software development environment and that software developers are following secure development techniques. A general rule of thumb is that a penetration test should not discover any additional application vulnerabilities relating to the developed code after the application has undergone a proper security code review.
Security Review of Web-Based Systems
- Source code review: pair programming and peer reviews (development phase)
- Software testing: static testing, dynamic testing, interface testing, and misuse case testing (integration and testing phase)
- Security review (production phase)
- Source code review - is the process of auditing the source code of a web application to verify that the proper security controls are present to mitigate security weaknesses and known vulnerabilities at the source code level (e.g. XML, OWASP Top 10 Application Risks), they work as intended, and that they have been invoked in all the right places.
- Web server security review – is the process of auditing the protection of information assets that can be accessed from a web server connected to the Internet.
- Back end database security review – is the process of auditing the collective measures used to protect and secure a database from illegitimate use and malicious threats and attacks. It is a broad term that includes a multitude of processes, tools and methodologies that ensure security within a database environment.
- Security code review – is the method of assuring the security of the software development environment and that software developers are following secure development techniques. A general rule of thumb is that a penetration test should not discover any additional application vulnerabilities relating to the developed code after the application has undergone a proper security code review.
Availability Assessment
- Effectiveness of malware propagation controls and scanning protection tools
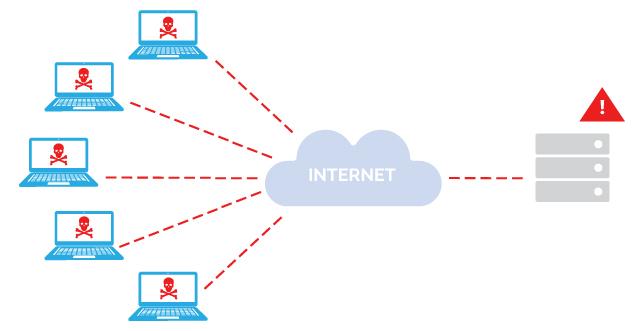
- Real-time controls to prevent DDoS and protect against volumetric attacks (Botnet / Zombie)
- Web application protections against Application Layer (L7) outages
- Controls protecting critical servers and services (e.g. behavioral, non-signature based, signature based, reputation services)
- Web Portal Availability / Domain Name Service (DNS) management and DNS server protection
Availability Assessment
- Effectiveness of malware propagation controls and scanning protection tools
- Real-time controls to prevent DDoS and protect against volumetric attacks (Botnet / Zombie)
- Web application protections against Application Layer (L7) outages
- Controls protecting critical servers and services (e.g. behavioral, non-signature based, signature based, reputation services)
- Web Portal Availability / Domain Name Service (DNS) management and DNS server protection
Security Audits
- Active Directory (AD) audit – provide an evaluation of the AD implementation, and security design effectiveness to support the servers and workstations deployed in a Windows environment
- Windows server and workstation audit – provide an evaluation of the servers’ functions (web. email, file/print, etc.) and of the operating system and function (desktop, laptop, special applications, etc.)
- Compliance audit - provide an evaluation of the compliance with existing policies, procedures and applicable standards, and of the operating effectiveness of the security controls
- AD management
- Secure AD boundaries
- Secure domain controllers
- Physical security of the domain controllers
- Secure domain and domain controller configuration settings
- Secure administrative practices
The compliance audit with policies, procedures and applicable standards is a review of the effectiveness of the security program, with a focus on security processes such as asset inventory and classification, user access and identity management, log reviews, backup verification data, key performance and risk indicators, etc.
Security Audits
- Active Directory (AD) audit – provide an evaluation of the AD implementation, and security design effectiveness to support the servers and workstations deployed in a Windows environment
- Windows server and workstation audit – provide an evaluation of the servers’ functions (web. email, file/print, etc.) and of the operating system and function (desktop, laptop, special applications, etc.)
- Compliance audit - provide an evaluation of the compliance with existing policies, procedures and applicable standards, and of the operating effectiveness of the security controls
- AD management
- Secure AD boundaries
- Secure domain controllers
- Physical security of the domain controllers
- Secure domain and domain controller configuration settings
- Secure administrative practices
The compliance audit with policies, procedures and applicable standards is a review of the effectiveness of the security program, with a focus on security processes such as asset inventory and classification, user access and identity management, log reviews, backup verification data, key performance and risk indicators, etc.
See also: