- OpenSSL 1.0.1 through 1.0.1f (inclusive) are vulnerable
- OpenSSL 1.0.1g is NOT vulnerable
- OpenSSL 1.0.0 branch is NOT vulnerable
- OpenSSL 0.9.8 branch is NOT vulnerable
- Junos OS 13.3R1 (Fixed code is listed in the "Solution" section)
- SSL VPN (IVEOS) 7.4r1 and later, and SSL VPN (IVEOS) 8.0r1 and later (Fixed code is listed in the "Solution" section)
- UAC 4.4r1 and later, and UAC 5.0r1 and later (Fixed code is listed in the "Solution" section)
- Junos Pulse (Desktop) 5.0r1 and later, and Junos Pulse (Desktop) 4.0r5 and later (Fixed code is listed in the "Solution" section)
- Network Connect (windows only) version 7.4R5 to 7.4R9.1 & 8.0R1 to 8.0R3.1. (This client is only impacted when used in FIPS mode.) (Fixed code is listed in the "Solution" section)
- Junos Pulse (Mobile) on Android version 4.2R1 and higher. (Fixed code is listed in the "Solution" section)
- Junos Pulse (Mobile) on iOS version 4.2R1 and higher. (This client is only impacted when used in FIPS mode.) (Fixed code is listed in the "Solution" section)
- WebApp Secure (Fixed code is listed in the "Solution" section)
- Odyssey client 5.6r5 and later
| Impacted Product Line | Resolution | Related Knowledgebase Item |
| Junos: | Juniper Networks has released Junos OS 13.3R1.8 to resolve this issue. Customers are encouraged to upgrade to 13.3R1.8 from earlier versions of 13.3R1 to resolve this issue. | N/A |
| SSL VPN (IVEOS): | Juniper Networks has released IVEOS 8.0R3.2 and 7.4R9.3. | http://kb.juniper.net/KB29004 |
| UAC: | Juniper Networks has released UAC 5.0r3.2. | http://kb.juniper.net/KB29007 |
| Junos Pulse (Desktop): | Juniper Networks has released Pulse Desktop 5.0R3.1 and Pulse Desktop 4.0R9.2. | http://kb.juniper.net/KB29004 |
| Junos Pulse (Mobile): | Juniper Networks has released Junos Pulse for Android version 5.0R3 (44997) which is now available for download on the Google Play Store. Juniper Networks has released Junos Pulse for Apple iOS version 5.0.3.44999 which is available for download from Apple App Store. | |
| WebApp Secure: | Juniper has pushed a software update (5.1.3-30) to systems that will resolve this issue. Please initiate the upgrade to resolve this issue | https://www.juniper.net/techpubs/en_US/webapp5.1.3/information-products/topic-collections/webapp-secure-5.1.3-30-release-notes.pdf |
Junos:
- Since SSL is used for remote network configuration and management applications such as J-Web and SSL Service for JUNOScript (XNM-SSL), viable workarounds for this issue in Junos may include:
- Disabling J-Web
- Disable SSL service for JUNOScript and only use Netconf, which makes use of SSH, to make configuration changes Limit access to J-Web and XNM-SSL from only trusted networks
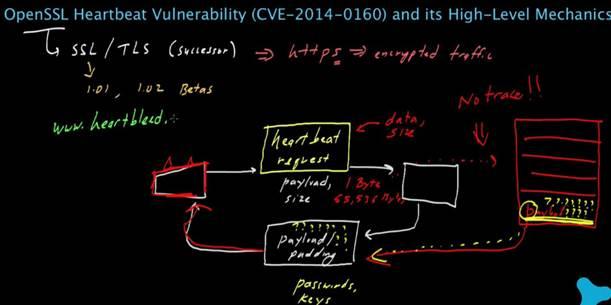
NEW BUG UNCOVERED – a vulnerability which exists in OpenSSL has recently been uncovered. The vulnerability is an information disclosure bug which is due to an error when handling TLS/DTLS heartbeat packets. An attacker can leverage this vulnerability to disclose memory contents of a connected client or server.
Details:
- OpenSSL 1.0.1 through 1.0.1f (inclusive) are vulnerable
- OpenSSL 1.0.1g is NOT vulnerable
- OpenSSL 1.0.0 branch is NOT vulnerable
- OpenSSL 0.9.8 branch is NOT vulnerable
- Junos OS 13.3R1 (Fixed code is listed in the "Solution" section)
- SSL VPN (IVEOS) 7.4r1 and later, and SSL VPN (IVEOS) 8.0r1 and later (Fixed code is listed in the "Solution" section)
- UAC 4.4r1 and later, and UAC 5.0r1 and later (Fixed code is listed in the "Solution" section)
- Junos Pulse (Desktop) 5.0r1 and later, and Junos Pulse (Desktop) 4.0r5 and later (Fixed code is listed in the "Solution" section)
- Network Connect (windows only) version 7.4R5 to 7.4R9.1 & 8.0R1 to 8.0R3.1. (This client is only impacted when used in FIPS mode.) (Fixed code is listed in the "Solution" section)
- Junos Pulse (Mobile) on Android version 4.2R1 and higher. (Fixed code is listed in the "Solution" section)
- Junos Pulse (Mobile) on iOS version 4.2R1 and higher. (This client is only impacted when used in FIPS mode.) (Fixed code is listed in the "Solution" section)
- WebApp Secure (Fixed code is listed in the "Solution" section)
- Odyssey client 5.6r5 and later
| Impacted Product Line | Resolution | Related Knowledgebase Item |
| Junos: | Juniper Networks has released Junos OS 13.3R1.8 to resolve this issue. Customers are encouraged to upgrade to 13.3R1.8 from earlier versions of 13.3R1 to resolve this issue. | N/A |
| SSL VPN (IVEOS): | Juniper Networks has released IVEOS 8.0R3.2 and 7.4R9.3. | http://kb.juniper.net/KB29004 |
| UAC: | Juniper Networks has released UAC 5.0r3.2. | http://kb.juniper.net/KB29007 |
| Junos Pulse (Desktop): | Juniper Networks has released Pulse Desktop 5.0R3.1 and Pulse Desktop 4.0R9.2. | http://kb.juniper.net/KB29004 |
| Junos Pulse (Mobile): | Juniper Networks has released Junos Pulse for Android version 5.0R3 (44997) which is now available for download on the Google Play Store. Juniper Networks has released Junos Pulse for Apple iOS version 5.0.3.44999 which is available for download from Apple App Store. | |
| WebApp Secure: | Juniper has pushed a software update (5.1.3-30) to systems that will resolve this issue. Please initiate the upgrade to resolve this issue | https://www.juniper.net/techpubs/en_US/webapp5.1.3/information-products/topic-collections/webapp-secure-5.1.3-30-release-notes.pdf |
IDP/IPS Signature released to detect Heartbleed vulnerability.
Sigpack 2362 released : https://signatures.juniper.net/restricted/sigupdates/nsm-updates/updates.xml https://signatures.juniper.net/restricted/sigupdates/nsm-updates/2362.html
Junos:
- Since SSL is used for remote network configuration and management applications such as J-Web and SSL Service for JUNOScript (XNM-SSL), viable workarounds for this issue in Junos may include:
- Disabling J-Web
- Disable SSL service for JUNOScript and only use Netconf, which makes use of SSH, to make configuration changes Limit access to J-Web and XNM-SSL from only trusted networks
NEW BUG UNCOVERED – a vulnerability which exists in OpenSSL has recently been uncovered. The vulnerability is an information disclosure bug which is due to an error when handling TLS/DTLS heartbeat packets. An attacker can leverage this vulnerability to disclose memory contents of a connected client or server.
See also: