What is Kubernetes?
The most common cloud providers offering fully managed services for Kubernetes are
- EKS – Amazon Elastic Kubernetes Services
- AKS – Microsoft Azure Kubernetes Service
- GKE – Google Kubernetes Engine
What is Kubernetes?
Container-based microservices architectures have profoundly changed the way development and operations teams test and deploy modern software. Large and small software companies alike are now deploying thousands of container instances daily, and that’s a complexity of scale they have to manage.
- EKS – Amazon Elastic Kubernetes Services
- AKS – Microsoft Azure Kubernetes Service
- GKE – Google Kubernetes Engine
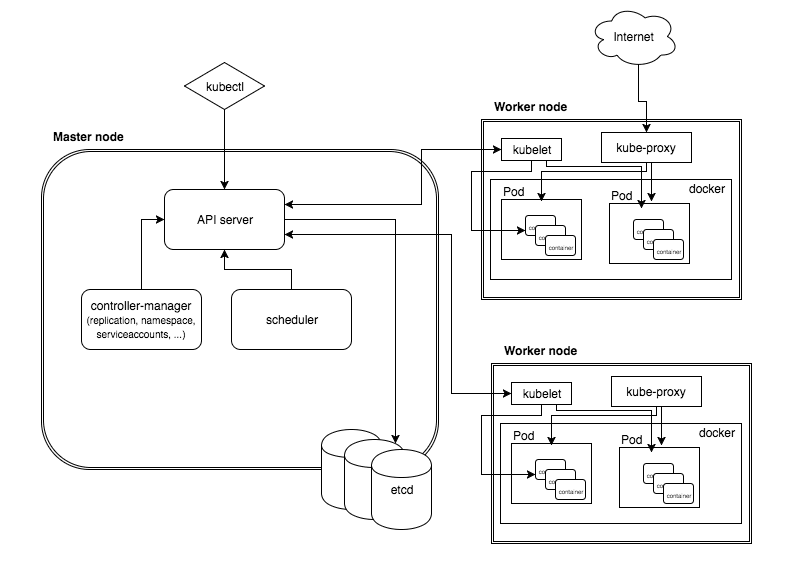
Kubernetes Components and Architecture
Master node is responsible for managing whole cluster. It monitors the health check of all nodes in the cluster.
Four basic components of the master node (control plane):
- API server : centralized component where all the cluster components are communicated
- Scheduler : responsible for assigning your application to worker node
- Controller manager : maintains the cluster, it handles node failures, replicating components, maintaining the correct number of pods
- Etcd : data store that stores the cluster configuration
Worker node are nothing but a virtual machine(VM’s) running in cloud or on-prem, a physical server running inside your data center
Three basic components of the Worker Node (Data plane)
- Kubelet : runs and manages the containers on node and it talks to API server
- Kube-proxy : load balances traffic between application components
- Container runtime : a software that executes containers and manages container images on a node(eg. Docker)
Pods are smallest unit of deployment in Kubernetes as container is smallest unit of deployment in Docker
Kubernetes Components and Architecture
Master node is responsible for managing whole cluster. It monitors the health check of all nodes in the cluster.
Four basic components of the master node (control plane):
- API server : centralized component where all the cluster components are communicated
- Scheduler : responsible for assigning your application to worker node
- Controller manager : maintains the cluster, it handles node failures, replicating components, maintaining the correct number of pods
- Etcd : data store that stores the cluster configuration
Worker node are nothing but a virtual machine(VM’s) running in cloud or on-prem, a physical server running inside your data center
Three basic components of the Worker Node (Data plane)
- Kubelet : runs and manages the containers on node and it talks to API server
- Kube-proxy : load balances traffic between application components
- Container runtime : a software that executes containers and manages container images on a node(eg. Docker)
Pods are smallest unit of deployment in Kubernetes as container is smallest unit of deployment in Docker
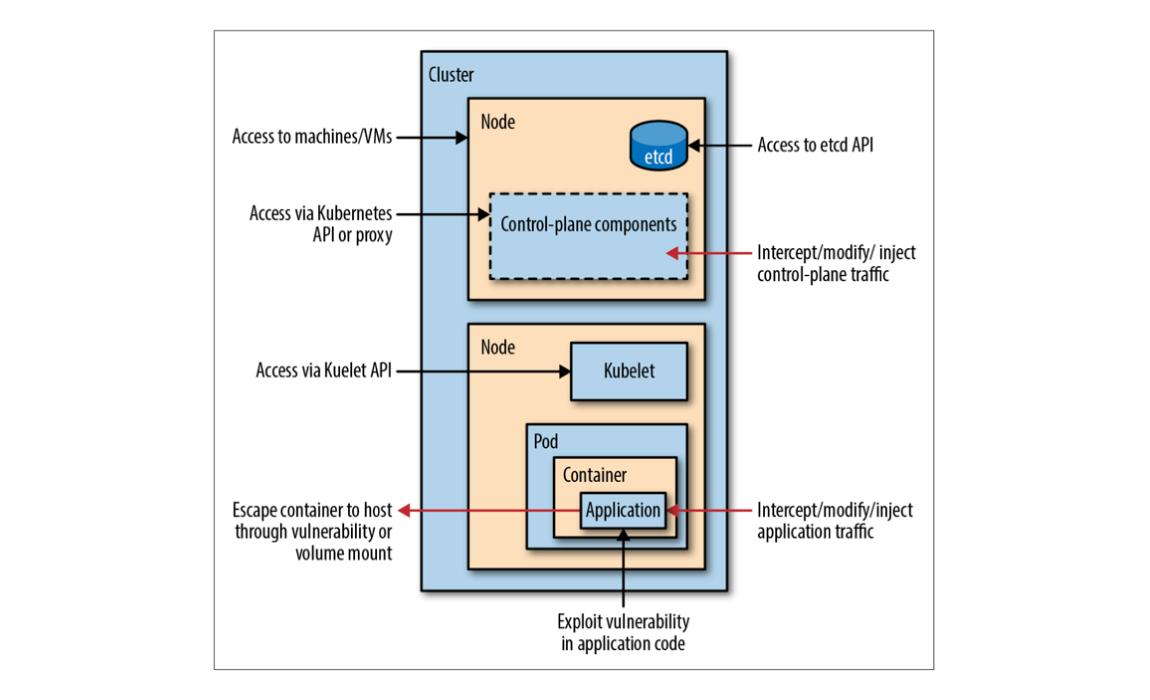
Kubernetes Security Best Practices
- Continuously scan your CI/CD pipeline and registries for vulnerabilities, hardcoded-secrets, malware and configuration issues.
- Prevent untrusted and unapproved images from running anywhere in the cluster
- Enforce fine-grained access control roles (RBAC) and policies that manage access to kubectl commands by specific Kubernetes deployments and nodes
- Regulate access to computer or network resources based on the roles of individual users within the organization
- Define permissions on namespaced resources and be granted within individual namespace(s)
- Define permissions on namespaced resources and be granted across all namespaces
- Define permissions on cluster-scoped resources
- ensure that containerized code can read only the secrets that it needs
- Use different set of secrets for different environments (like production, development, and testing).
- Secrets should be protected at rest by encrypting the traffic between the Kubernetes control-plane components using TLS
- Use tools such as Helm, helm-secrets is a great tool for managing secrets and storing them with encrypted version control.
- Check cluster and node configuration against CIS Kubernets Benchmark tests
- Implement automated container level security profiles that detect anomalies and prevent non-whitelisted operations
- Ensure Kubernetes-specific information, such as pod name, type, deployment and namespace data, in addition to user access, container start/stop and other events
- Implement network policy using network policy plugins on how Pod are allowed to communicate with each other and other network endpoints. By default, pods are non-isolated; they accept traffic from any source
- Control network traffic with container level firewall rules based on kubernets namespace, cluster and deployments using plugins such as Flannel, Calico etc.
Kubernetes Security Best Practices
- Continuously scan your CI/CD pipeline and registries for vulnerabilities, hardcoded-secrets, malware and configuration issues.
- Prevent untrusted and unapproved images from running anywhere in the cluster
- Enforce fine-grained access control roles (RBAC) and policies that manage access to kubectl commands by specific Kubernetes deployments and nodes
- Regulate access to computer or network resources based on the roles of individual users within the organization
- Define permissions on namespaced resources and be granted within individual namespace(s)
- Define permissions on namespaced resources and be granted across all namespaces
- Define permissions on cluster-scoped resources
- ensure that containerized code can read only the secrets that it needs
- Use different set of secrets for different environments (like production, development, and testing).
- Secrets should be protected at rest by encrypting the traffic between the Kubernetes control-plane components using TLS
- Use tools such as Helm, helm-secrets is a great tool for managing secrets and storing them with encrypted version control.
- Check cluster and node configuration against CIS Kubernets Benchmark tests
- Implement automated container level security profiles that detect anomalies and prevent non-whitelisted operations
- Ensure Kubernetes-specific information, such as pod name, type, deployment and namespace data, in addition to user access, container start/stop and other events
- Implement network policy using network policy plugins on how Pod are allowed to communicate with each other and other network endpoints. By default, pods are non-isolated; they accept traffic from any source
- Control network traffic with container level firewall rules based on kubernets namespace, cluster and deployments using plugins such as Flannel, Calico etc.
See also: