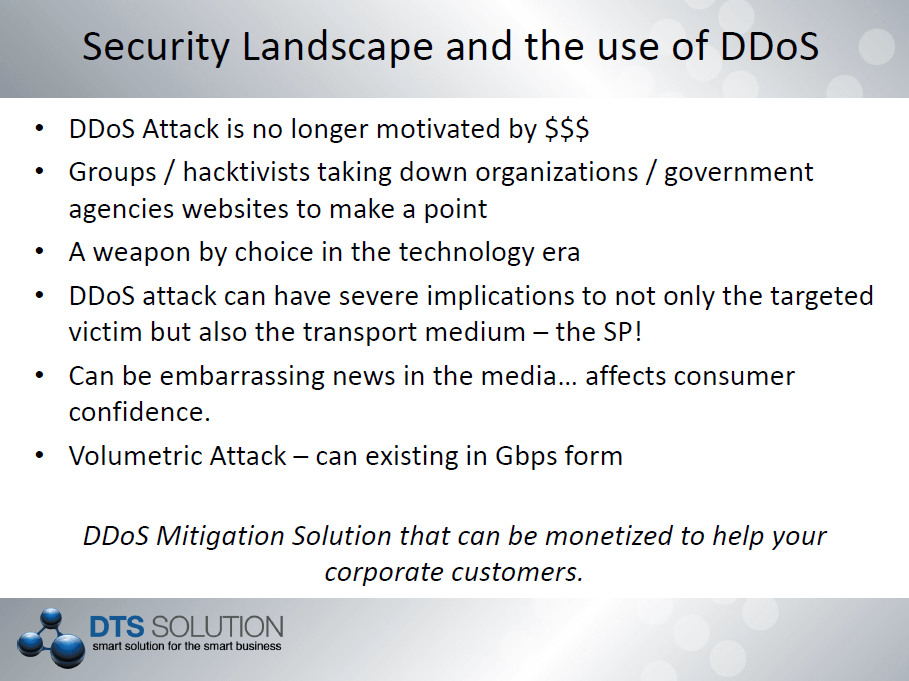
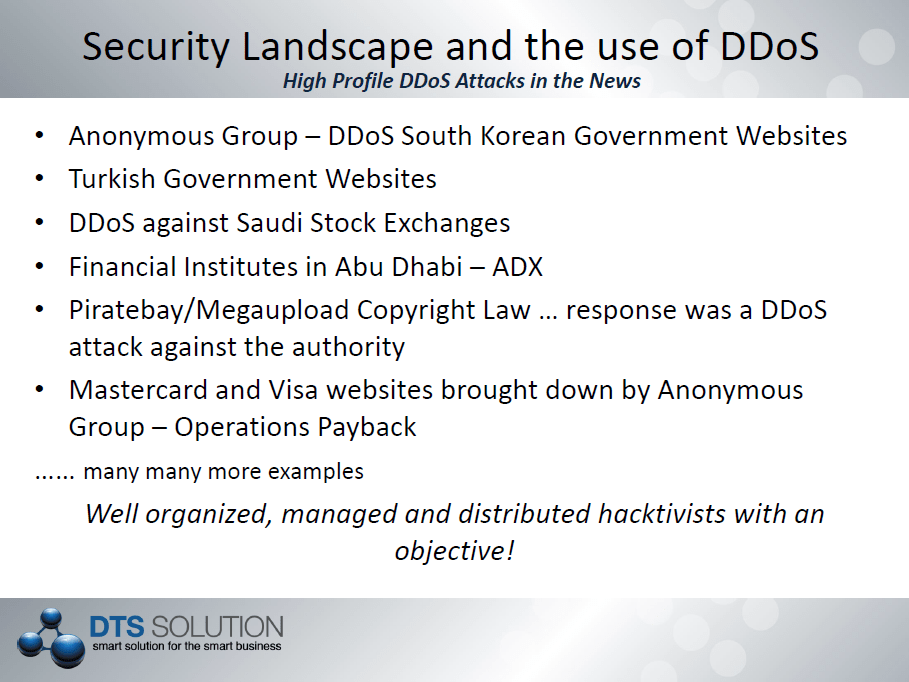
DTS Solution – leading security consulting firm; has been selected by one of the largest Internet Service Provider (ISP) in the UAE, to provide consulting and professional services for national Distributed Denial of Service (DDoS) protection using Arbor Networks technology and the PeakFlow SP solution. The region has seen a period of highly targeted attacks against governmental and financial institutes and DDoS attributed to many of these attacks causing significant business impact through service unavailability. As a leading security solutions integrator DTS understands the growing concerns of DDoS and the severe crippling impact it can bring to business operations and working with the leaders in DDoS protection – Arbor Networks, will allow the ISP to not only protect itself to such attacks but also its corporate customers for which it provides hosting and IP transport services.
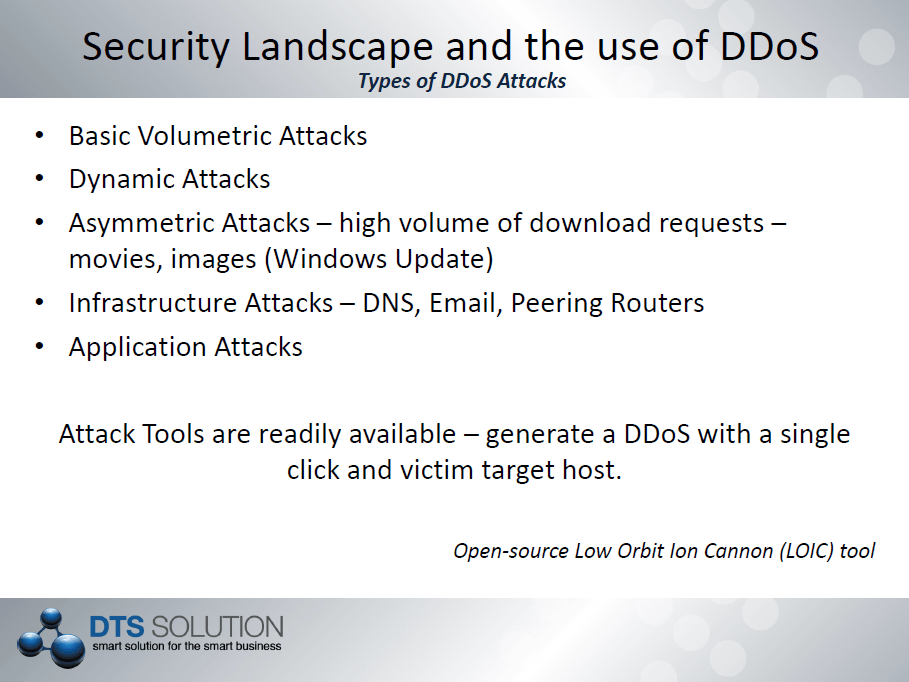
DDoS attacks can range in many different forms;
- Volumetric Attack – flood the network pipe (TCP SYN Flood as an example).
- Dynamic Attack – using DoS as a tool to generate additional DoS attacks – high volume of HTTP requests translates to high volume of SQL queries.
- Asymmetric Attack – initiating an enormous amount of download request from a large network of botnets – i.e. download or stream a particular video stream.
- Application Level Attack – HTTP get requests for particular object files or URL retrieval.
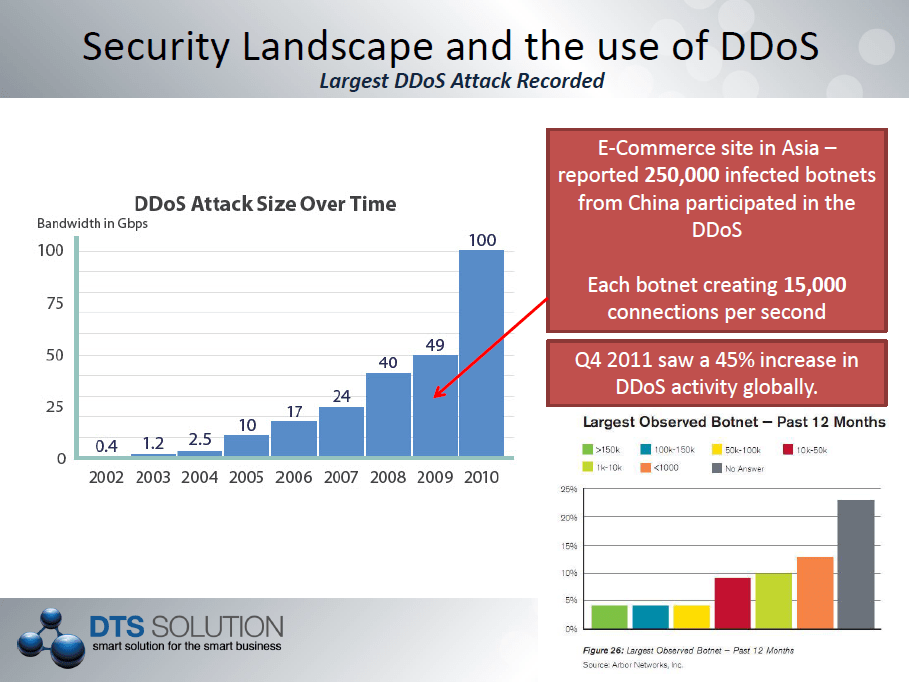
DDoS attacks on the rise;
DDoS attacks on organizations have exponentially grown over the last few years as illustrated below; not only increasing in the number of attacks but also in the scale of the attack and now ranging to multi-Gbps of DDoS volumetric attacks.
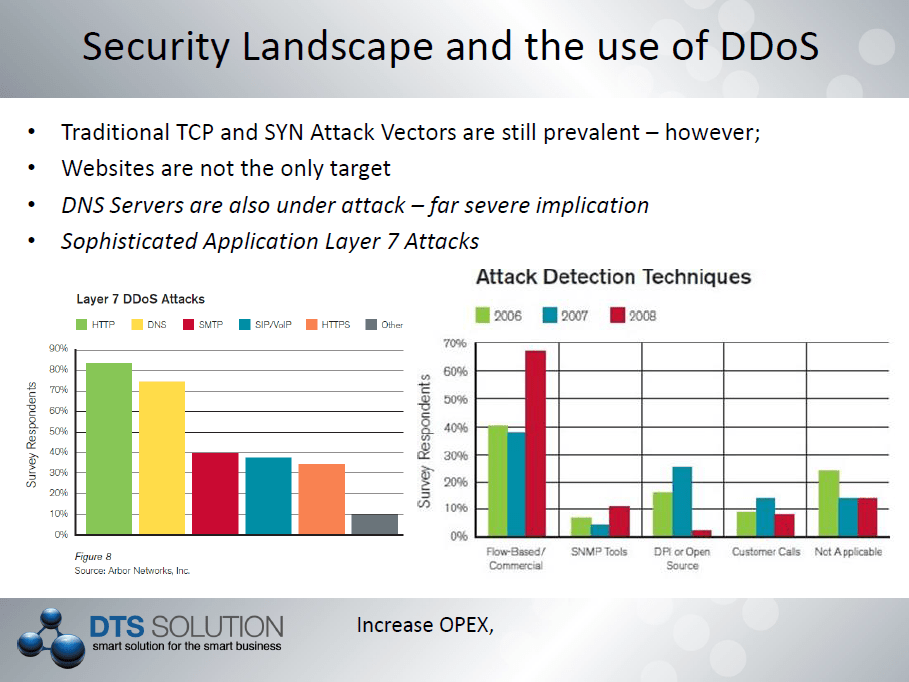
Traditional exploits on L3/L4 DDoS are still more prevalent however there is an increase on DDoS against the application level, the so called L7 of the OSI stack requiring application level of intelligence. HTTP and DNS DDoS are very common these days and understanding the use of these protocols within a DDoS attack is an important mechanism to provide preventative and blocking techniques to DDoS attacks.
The components of a DDoS …
DDoS attacks are created through the use of thousands of infected machines known as ‘botnets’ that are remotely controlled by command and control (C&C) servers. A botnet is a collection of internet-connected computers whose security defenses have been breached and control ceded to a malicious party. Each such compromised device, known as a “bot”, is created when a computer is penetrated by software from a malware distribution; otherwise known as malicious software. The controller of a botnet is able to direct the activities of these compromised computers through communication channels formed by standards-based network protocols such as IRC (Internet Relay Chat) and HTTP (Hypertext Transfer Protocol). Once the botnet is controlled by the C&C is can be used as a platform to launch DDOS attacks – of course the higher the volume of bots you have in the botnet the more severe you can make the DDoS attack.
DDoS Protection using Arbor Network
Arbor Networks specializes in DDoS protection through the use of dynamic DDoS analysis techniques. The prevention of DDoS attack takes place in three phases – Detection, Diversion/Injection and finally Mitigation.
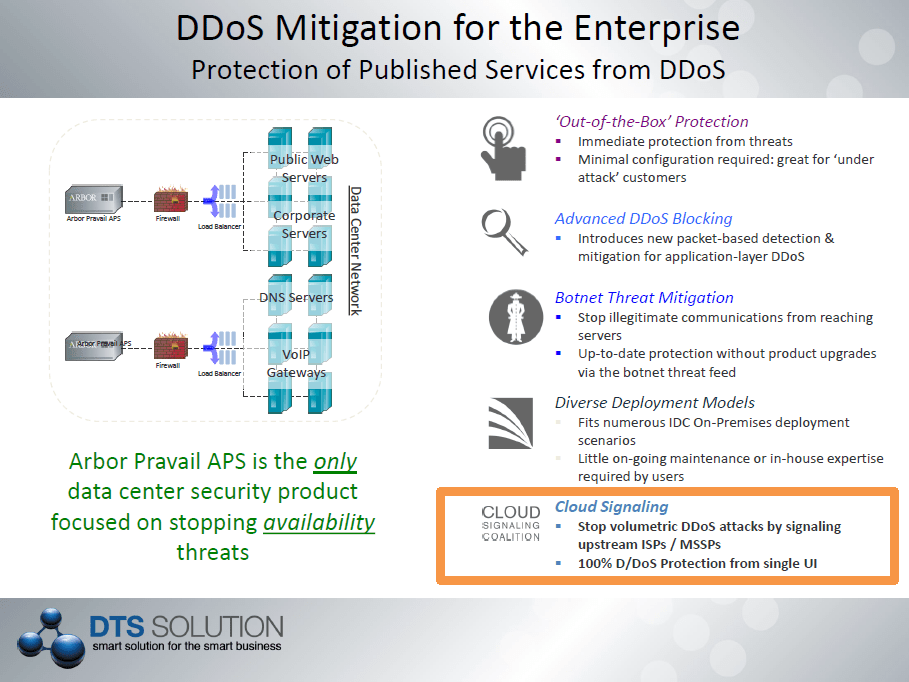
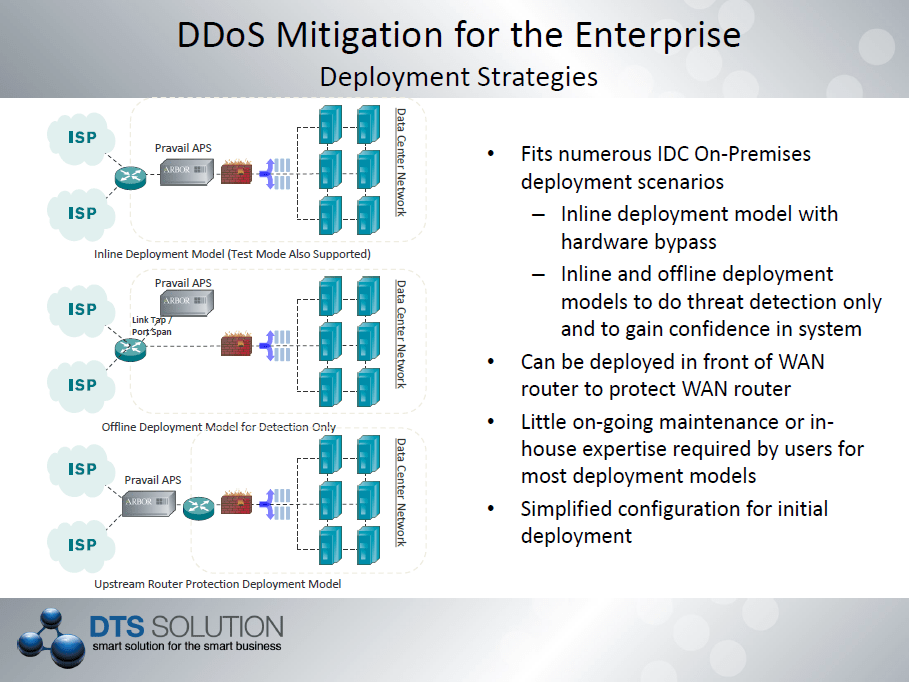
With the dynamic nature of Arbor Network PeakFlow SP solution that is implemented within the ISP network – DDoS attacks can be prevent upstream before there is impact to organizations. With this in mind, the ISP can offer Managed DDoS protection for organizations that subscribe to the service. Localized DDoS prevention technology where the DDoS protection device is deployed inline and at data center or internet gateway perimeters are ineffective since the pipe is already flooded before it hits the perimeter / edge of the network. It is for this reason DDoS protection can only be enabled upstream and this is at the ISP level.
Using the PeakFlow engine, Arbor Networks can accurately identify and classify a DDoS attack through the use of Flow (NetFlow, J-Flow, S-Flow, IPIX) information from Internet Gateway connected (IGW) routers. Once a DDoS attack is identified a dynamic BGP route can be advertised to the IGW router to redirect traffic to the scrubbing center for the organization under attack. With the DDoS traffic to the organization redirected to the scrubbing center, Arbor Network TMS (Threat Mitigation System) takes care of the rest. Blocking the source IP that initiated DDoS traffic (botnet detection) whilst allowing legitimate traffic to the same organization thus preventing service unavailability during DDoS attacks.
To learn more about DDOS – preventative technology, solutions and consulting services please contact our sales team.
DTS Solution – leading security consulting firm; has been selected by one of the largest Internet Service Provider (ISP) in the UAE, to provide consulting and professional services for national Distributed Denial of Service (DDoS) protection using Arbor Networks technology and the PeakFlow SP solution. The region has seen a period of highly targeted attacks against governmental and financial institutes and DDoS attributed to many of these attacks causing significant business impact through service unavailability. As a leading security solutions integrator DTS understands the growing concerns of DDoS and the severe crippling impact it can bring to business operations and working with the leaders in DDoS protection – Arbor Networks, will allow the ISP to not only protect itself to such attacks but also its corporate customers for which it provides hosting and IP transport services.
DDoS attacks can range in many different forms;
- Volumetric Attack – flood the network pipe (TCP SYN Flood as an example).
- Dynamic Attack – using DoS as a tool to generate additional DoS attacks – high volume of HTTP requests translates to high volume of SQL queries.
- Asymmetric Attack – initiating an enormous amount of download request from a large network of botnets – i.e. download or stream a particular video stream.
- Application Level Attack – HTTP get requests for particular object files or URL retrieval.
DDoS attacks on the rise;
DDoS attacks on organizations have exponentially grown over the last few years as illustrated below; not only increasing in the number of attacks but also in the scale of the attack and now ranging to multi-Gbps of DDoS volumetric attacks.
Traditional exploits on L3/L4 DDoS are still more prevalent however there is an increase on DDoS against the application level, the so called L7 of the OSI stack requiring application level of intelligence. HTTP and DNS DDoS are very common these days and understanding the use of these protocols within a DDoS attack is an important mechanism to provide preventative and blocking techniques to DDoS attacks.
The components of a DDoS …
DDoS attacks are created through the use of thousands of infected machines known as ‘botnets’ that are remotely controlled by command and control (C&C) servers. A botnet is a collection of internet-connected computers whose security defenses have been breached and control ceded to a malicious party. Each such compromised device, known as a “bot”, is created when a computer is penetrated by software from a malware distribution; otherwise known as malicious software. The controller of a botnet is able to direct the activities of these compromised computers through communication channels formed by standards-based network protocols such as IRC (Internet Relay Chat) and HTTP (Hypertext Transfer Protocol). Once the botnet is controlled by the C&C is can be used as a platform to launch DDOS attacks – of course the higher the volume of bots you have in the botnet the more severe you can make the DDoS attack.
DDoS Protection using Arbor Network
Arbor Networks specializes in DDoS protection through the use of dynamic DDoS analysis techniques. The prevention of DDoS attack takes place in three phases – Detection, Diversion/Injection and finally Mitigation.
With the dynamic nature of Arbor Network PeakFlow SP solution that is implemented within the ISP network – DDoS attacks can be prevent upstream before there is impact to organizations. With this in mind, the ISP can offer Managed DDoS protection for organizations that subscribe to the service. Localized DDoS prevention technology where the DDoS protection device is deployed inline and at data center or internet gateway perimeters are ineffective since the pipe is already flooded before it hits the perimeter / edge of the network. It is for this reason DDoS protection can only be enabled upstream and this is at the ISP level.
Using the PeakFlow engine, Arbor Networks can accurately identify and classify a DDoS attack through the use of Flow (NetFlow, J-Flow, S-Flow, IPIX) information from Internet Gateway connected (IGW) routers. Once a DDoS attack is identified a dynamic BGP route can be advertised to the IGW router to redirect traffic to the scrubbing center for the organization under attack. With the DDoS traffic to the organization redirected to the scrubbing center, Arbor Network TMS (Threat Mitigation System) takes care of the rest. Blocking the source IP that initiated DDoS traffic (botnet detection) whilst allowing legitimate traffic to the same organization thus preventing service unavailability during DDoS attacks.
To learn more about DDOS – preventative technology, solutions and consulting services please contact our sales team.
See also: