Mobile Application Security Assessment
Business, public organizations and government nowadays are using mobile apps in new and compelling ways, from banking applications to healthcare platforms. Managing security risk is a growing challenge on these platforms, with new vulnerabilities found every day. Is your mobile app safe from attackers?
Objective of a Mobile Application Penetration Testing?
- To strengthen the security of the mobile application, and its API/ web platform/ web-service.
- Educate developers and security professionals about mobile application behavior that puts users at risk.
What is Tested?
At DTS Solution, our security experts test each mobile app at-rest and during runtime to identify all vulnerabilities. We combine multiple assessment tools with combined in-depth manual and automated tests to get the most comprehensive security assessment of the client applications. This deep-dive methodology also targets the following.
Application Level (Mobile and server side)
- Server side penetration testing
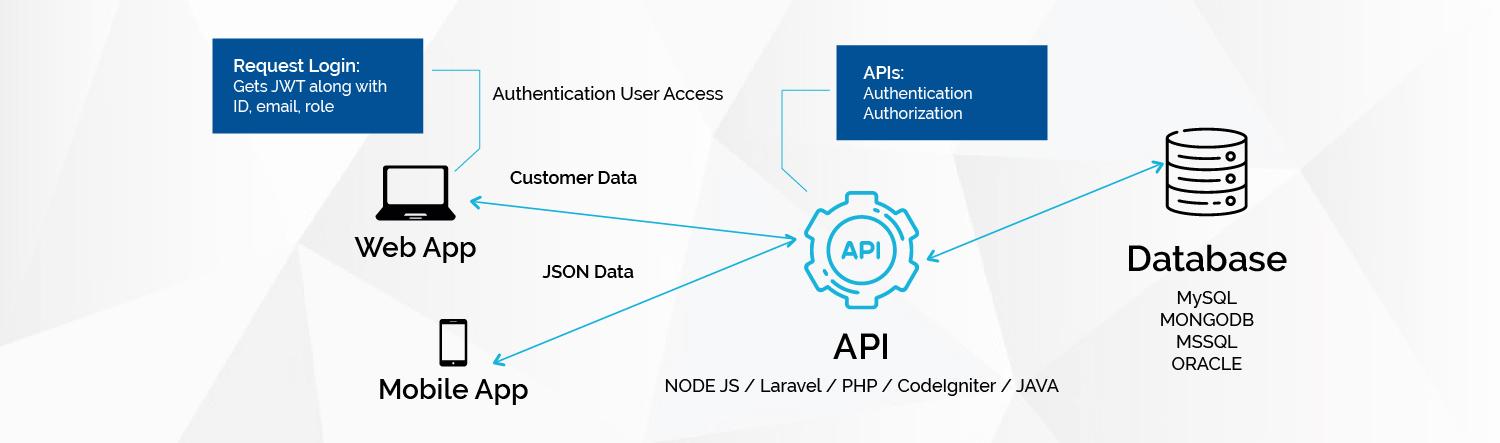
- Back end services and Application Program Interface (API) testing
- Network communication (communication with the API)
- Implementation & usages of the third-party components,
- Security configurations (signature, debug…)
- Business Logic Vulnerabilities
- Insecure Sensitive information Storage
Mobile Device Level
- Reverse engineering and code analysis
- Data storage and forensic analysis
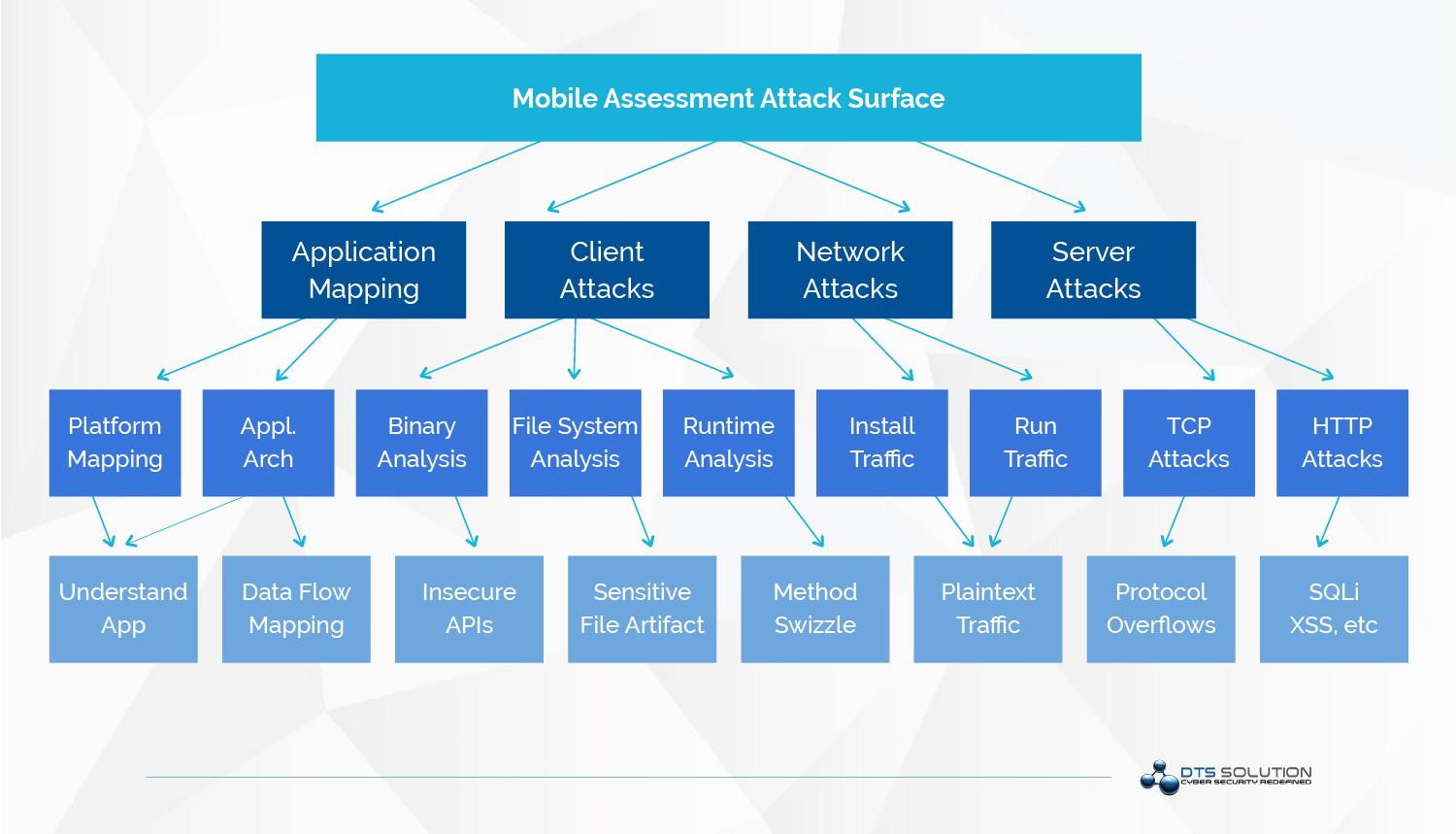
Each major attack surface contains specific areas that apply to the assessment. For each major attack, consider an appropriate technique:
- Application mapping ⇒ Information gathering
- Client attacks ⇒ Runtime, binary, and file system analysis
- Network and server attacks ⇒ Network analysis and insecure data storage
Application mapping
Observing the application at the functional level and analyzing its behavior using threat modeling techniques in the areas of
- Identity, authentication, and access control => Key chains, brute-force attacks, parameter tampering, logic flaws
- Input validation and encoding => Malicious input, fuzzing
- Encryption => SQLite database password fields, configuration file encryption
- User and session management => Session IDs, time lockouts
- Error and exception handling
- Auditing and logging => Logs, access control to logs.
Network attacks
- Authentication. In cases where the application is using HTTP basic authentication, this represents a risk. If used, it should always be done through SSL
- Authorization. Roles and access controls between them can be uncovered through parameter tampering. Securing the API key properly in an inaccessible folder can be uncovered by file analysis (native apps) or spidering the application (web-based apps).
- Session management. Session ID tokens sent through GET methods and placed in the URL are visible while proxying the application or sniffing the network.
- Weak encryption and protocols. Mobile applications are more vulnerable in these areas. Wireless vulnerabilities revolving around encryption protocols used by the device must be categorized.
The perspective of the testing (external, internal, authenticated, unauthenticated, etc.) will also be identified to ensure the validity of vulnerabilities discovered.
Mobile Application Security Assessment
Business, public organizations and government nowadays are using mobile apps in new and compelling ways, from banking applications to healthcare platforms. Managing security risk is a growing challenge on these platforms, with new vulnerabilities found every day. Is your mobile app safe from attackers?
Objective of a Mobile Application Penetration Testing?
- To strengthen the security of the mobile application, and its API/ web platform/ web-service.
- Educate developers and security professionals about mobile application behavior that puts users at risk.
What is Tested?
At DTS Solution, our security experts test each mobile app at-rest and during runtime to identify all vulnerabilities. We combine multiple assessment tools with combined in-depth manual and automated tests to get the most comprehensive security assessment of the client applications. This deep-dive methodology also targets the following.
Application Level (Mobile and server side)
- Server side penetration testing
- Back end services and Application Program Interface (API) testing
- Network communication (communication with the API)
- Implementation & usages of the third-party components,
- Security configurations (signature, debug…)
- Business Logic Vulnerabilities
- Insecure Sensitive information Storage
Mobile Device Level
- Reverse engineering and code analysis
- Data storage and forensic analysis
Each major attack surface contains specific areas that apply to the assessment. For each major attack, consider an appropriate technique:
- Application mapping ⇒ Information gathering
- Client attacks ⇒ Runtime, binary, and file system analysis
- Network and server attacks ⇒ Network analysis and insecure data storage
Application mapping
Observing the application at the functional level and analyzing its behavior using threat modeling techniques in the areas of
- Identity, authentication, and access control => Key chains, brute-force attacks, parameter tampering, logic flaws
- Input validation and encoding => Malicious input, fuzzing
- Encryption => SQLite database password fields, configuration file encryption
- User and session management => Session IDs, time lockouts
- Error and exception handling
- Auditing and logging => Logs, access control to logs.
Binary and file analysis
Discover insecure API calls and files not properly secured with adequate access controls. This can be achieved by debugging and analyzing the code using IDA Pro or the Hopper App.
Network attacks
- Authentication. In cases where the application is using HTTP basic authentication, this represents a risk. If used, it should always be done through SSL
- Authorization. Roles and access controls between them can be uncovered through parameter tampering. Securing the API key properly in an inaccessible folder can be uncovered by file analysis (native apps) or spidering the application (web-based apps).
- Session management. Session ID tokens sent through GET methods and placed in the URL are visible while proxying the application or sniffing the network.
- Weak encryption and protocols. Mobile applications are more vulnerable in these areas. Wireless vulnerabilities revolving around encryption protocols used by the device must be categorized.
The perspective of the testing (external, internal, authenticated, unauthenticated, etc.) will also be identified to ensure the validity of vulnerabilities discovered.
Mobile Application Security Testing Guide
The MSTG is a comprehensive manual for mobile app security testing and reverses engineering to be used for iOS and Android mobile security testing with the following areas in focus:
- Mobile platform internals
- Security testing in the mobile app development life-cycle
- Basic static and dynamic security testing
- Mobile app reverse engineering and tampering
- Assessing software protections
- Detailed test cases that map to the requirements in the MASVS
OWASP mobile top 10 security risks
OWASP Mobile Top 10 is a list that identifies types of security risks faced by mobile apps globally. It is an acting guide for developers to build secure applications and incorporate best coding practices.
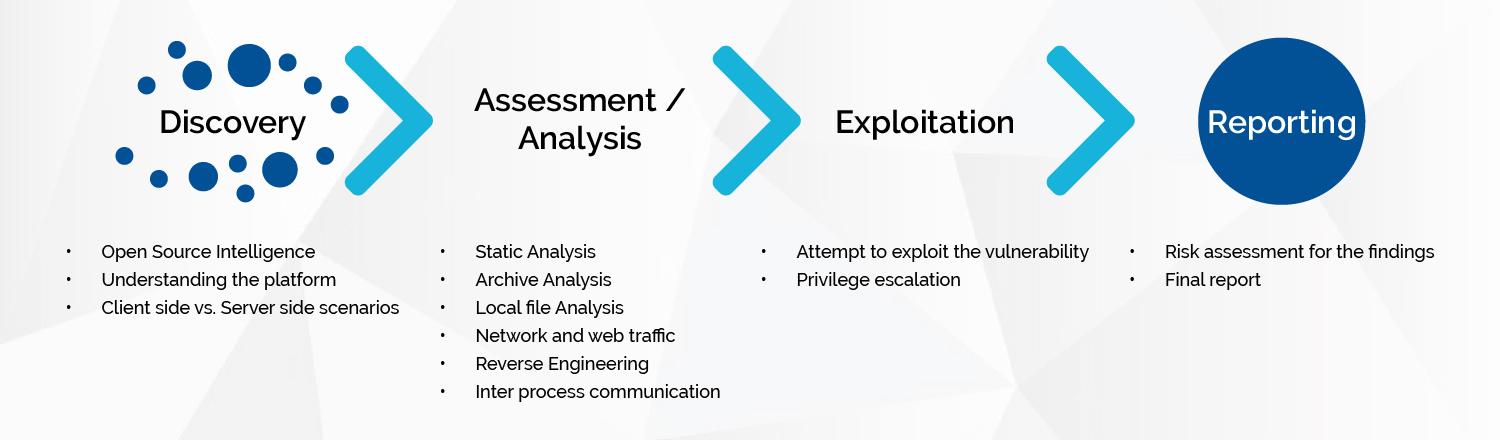
Reporting
The output provided will include an executive-level report and a technical findings report.
- The executive-level report is written for management consumption and includes a high-level overview of assessment activities, scope, most critical/thematic issues discovered.
- The technical findings report will include all vulnerabilities listed individually, with details as to how to recreate the issue, understand the risk, recommended remediation actions, and helpful reference links.
Presentation
The final activity in any assessment will be a presentation of all documentation to the client. DTS Solution will walk the client through the information provided, make any updates needed, and address questions regarding the assessment output.
Mobile Application Security Testing Guide
The MSTG is a comprehensive manual for mobile app security testing and reverses engineering to be used for iOS and Android mobile security testing with the following areas in focus:
- Mobile platform internals
- Security testing in the mobile app development life-cycle
- Basic static and dynamic security testing
- Mobile app reverse engineering and tampering
- Assessing software protections
- Detailed test cases that map to the requirements in the MASVS
OWASP mobile top 10 security risks
OWASP Mobile Top 10 is a list that identifies types of security risks faced by mobile apps globally. It is an acting guide for developers to build secure applications and incorporate best coding practices.
Reporting
The output provided will include an executive-level report and a technical findings report.
- The executive-level report is written for management consumption and includes a high-level overview of assessment activities, scope, most critical/thematic issues discovered.
- The technical findings report will include all vulnerabilities listed individually, with details as to how to recreate the issue, understand the risk, recommended remediation actions, and helpful reference links.
Presentation
The final activity in any assessment will be a presentation of all documentation to the client. DTS Solution will walk the client through the information provided, make any updates needed, and address questions regarding the assessment output.
See also: