DTS Solution provides full control and visibility across the application lifecycle, with active threat protection and incident response capabilities.
Cloud-native applications pose several new security challenges due to the traditional security approach of not being able to provide adequate visibility and tighter controls, thereby making the container environment vulnerable. Containers need to be secured at build, deployment and runtime.
DTS Solution provides full control and visibility across the application lifecycle, with active threat protection and incident response capabilities.
DTS Solution provides full control and visibility across the application lifecycle, with active threat protection and incident response capabilities.
Cloud-native applications pose several new security challenges due to the traditional security approach of not being able to provide adequate visibility and tighter controls, thereby making the container environment vulnerable. Containers need to be secured at build, deployment and runtime.
DTS Solution provides full control and visibility across the application lifecycle, with active threat protection and incident response capabilities.
Key Features:
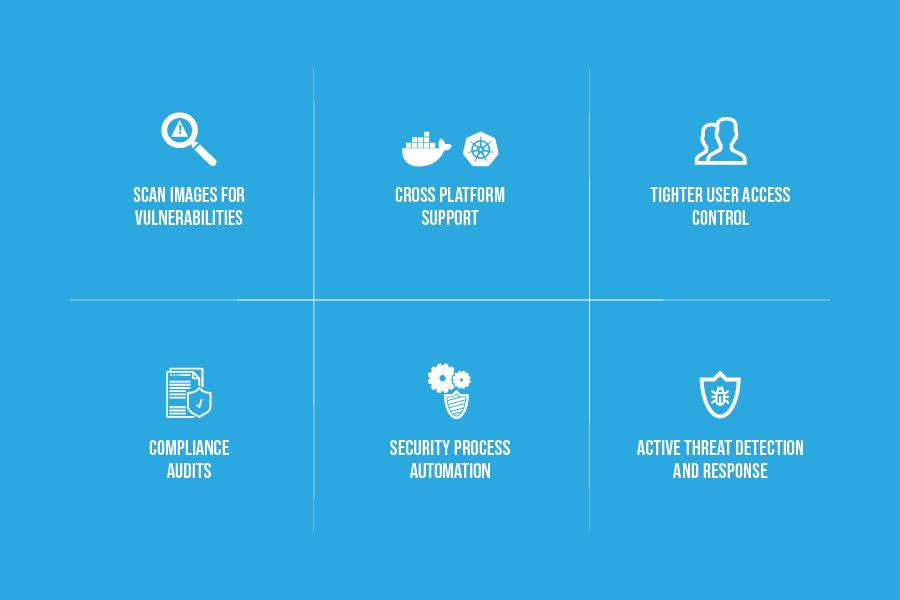
- Cross Platform Support: Supports both Dockers and Kubernetes container platforms, Linux and Windows environments, on-premise and/or public cloud
- Vulnerability Assessment: Check known vulnerabilities by continuous image scanning and remediation to ensure integrity of the application lifecyle
- Tighter User Controls: With a centralized approach, define appropriate and consistent privileges for different user categories for each container, host, image, cluster and storage volume
- Incident Detection and Response: Ensure security of containers through a layered approach with effective controls and visibility for anomaly detection, runtime protection, segmentation and container profiling
- Security Process Automation: Define operational workflows to reduce the need for continuous security efforts with the help of security orchestration tools
- Compliance Audits: Establish proper guidelines and appropriate controls and practices to meet security standards and compliance audits
For more information, please email [email protected]
Key Features:
- Cross Platform Support: Supports both Dockers and Kubernetes container platforms, Linux and Windows environments, on-premise and/or public cloud
- Vulnerability Assessment: Check known vulnerabilities by continuous image scanning and remediation to ensure integrity of the application lifecyle
- Tighter User Controls: With a centralized approach, define appropriate and consistent privileges for different user categories for each container, host, image, cluster and storage volume
- Incident Detection and Response: Ensure security of containers through a layered approach with effective controls and visibility for anomaly detection, runtime protection, segmentation and container profiling
- Security Process Automation: Define operational workflows to reduce the need for continuous security efforts with the help of security orchestration tools
- Compliance Audits: Establish proper guidelines and appropriate controls and practices to meet security standards and compliance audits
For more information, please email [email protected]
See also: