Ransomware Incident Response Plan - Part 2
In a properly implemented crypto viral extortion attack, recovering the files without the decryption key is an intractable problem and difficult to trace digital currencies such as Ukash or Bitcoin and other cryptocurrency are used for the ransoms, making tracing and prosecuting the perpetrators difficult.
Ransomware Incident Response Plan-Part 2
The following is part two of the overall incident response plan where we are going to discuss in our opinion the most important phases of the incident response plan, which are the containment and remediation phases. Before jumping into the phases and steps we would like to give brief recap about ransomware, to explain what it is and how does it work.
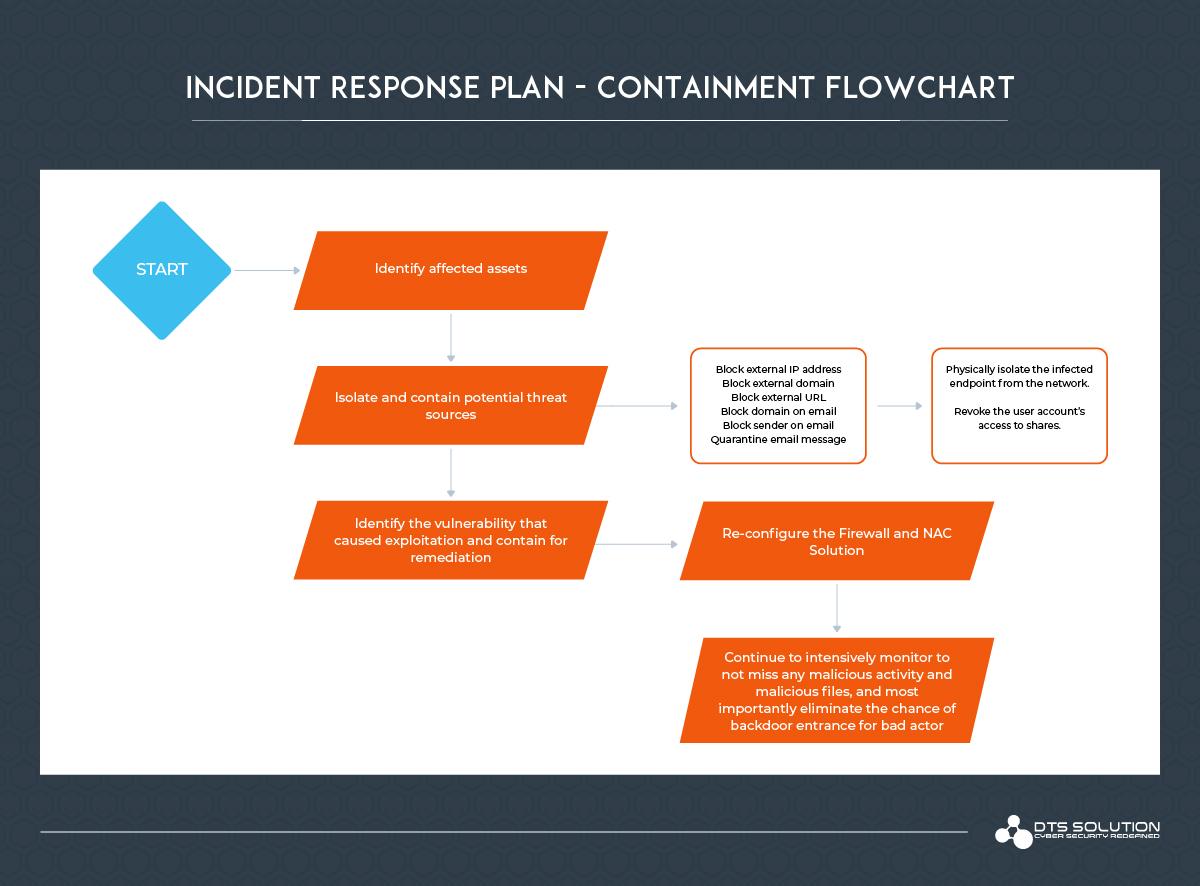
3. Containment Overview
Carefully document and report the performed activities, this will help to detect the virus/malware on other IT systems as well. Examine all endpoints that may be vulnerable or exposed to that particular attack, perform identification phase on the endpoint and in case of anomaly detection isolate the system.
3. Containment Overview
Carefully document and report the performed activities, this will help to detect the virus/malware on other IT systems as well. Examine all endpoints that may be vulnerable or exposed to that particular attack, perform identification phase on the endpoint and in case of anomaly detection isolate the system.
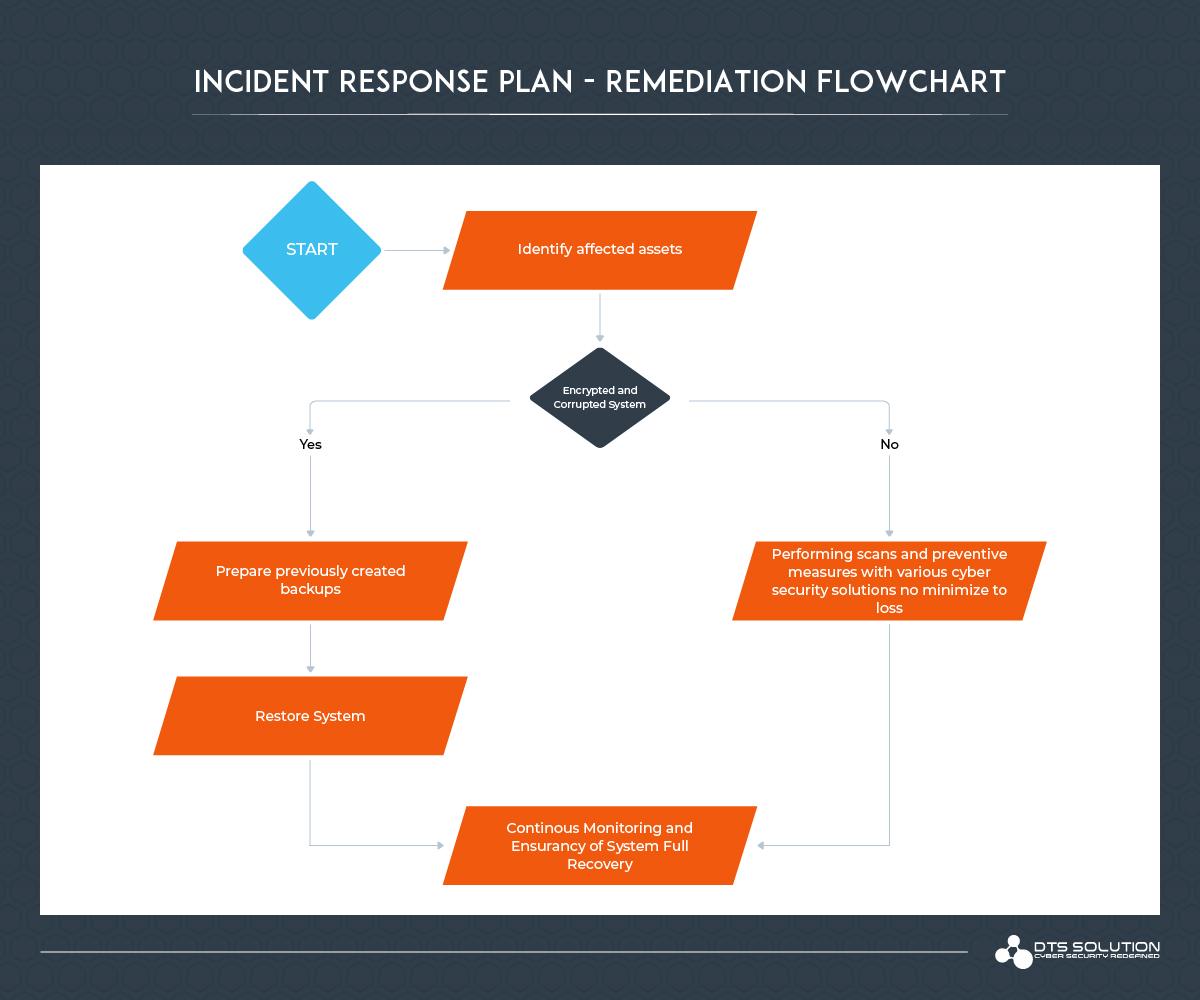
4. Remediation Overview
4. Remediation Overview
See also: