An audit universe is a fundamental component of audit planning, providing a structured framework to identify and assess all auditable entities within an organization including business processes, IT and security systems etc. It helps internal auditors prioritize audit engagements, ensuring that high-risk areas receive adequate scrutiny within a fiscal year or a predetermined audit period.
A security audit universe, therefore, is a structured framework that helps organizations identify, assess, and audit their cybersecurity and IT risk areas. It ensures that all critical security domains, including cybersecurity, IT security, business continuity, cyber resilience among others, are systematically reviewed. It helps internal auditors, risk managers, and compliance teams systematically assess security controls, identify vulnerabilities, and ensure adherence to cybersecurity frameworks.
In essence, the existence of a security audit universe:
- Reduces the likelihood of security breaches, minimizes attack surfaces, and strengthens defences against cyber threats.
- Helps organizations avoid hefty fines, legal consequences, and reputational damage due to non-compliance.
- Ensures operational continuity, reduces financial losses, and maintains trust in the organization’s ability to withstand cyber disruptions.
- Helps leaders make informed decisions about cybersecurity investments, policy enforcement, and risk mitigation strategies.
- Reduces risks from third-party data breaches, insecure APIs, and vendor security weaknesses.
- Creates an organization-wide security culture, reducing human errors and insider threats.
As an audit executive or simply a audit planner, the following considerations can be made in creating a security universe:
An audit universe is a fundamental component of audit planning, providing a structured framework to identify and assess all auditable entities within an organization including business processes, IT and security systems etc. It helps internal auditors prioritize audit engagements, ensuring that high-risk areas receive adequate scrutiny within a fiscal year or a predetermined audit period.
A security audit universe, therefore, is a structured framework that helps organizations identify, assess, and audit their cybersecurity and IT risk areas. It ensures that all critical security domains, including cybersecurity, IT security, business continuity, cyber resilience among others, are systematically reviewed. It helps internal auditors, risk managers, and compliance teams systematically assess security controls, identify vulnerabilities, and ensure adherence to cybersecurity frameworks.
In essence, the existence of a security audit universe:
- Reduces the likelihood of security breaches, minimizes attack surfaces, and strengthens defences against cyber threats.
- Helps organizations avoid hefty fines, legal consequences, and reputational damage due to non-compliance.
- Ensures operational continuity, reduces financial losses, and maintains trust in the organization’s ability to withstand cyber disruptions.
- Helps leaders make informed decisions about cybersecurity investments, policy enforcement, and risk mitigation strategies.
- Reduces risks from third-party data breaches, insecure APIs, and vendor security weaknesses.
- Creates an organization-wide security culture, reducing human errors and insider threats.
As an audit executive or simply a audit planner, the following considerations can be made in creating a security universe:
Organize the Security Audit Universe Properly
- Group security areas in a logical way (e.g., Cybersecurity, IT, Business Continuity etc)
- If the company has offices in different regions or operates internationally, they may be considerations made for location-based security risks.
- Make sure everything fits within the company’s risk management plan and meets applicable cybersecurity regulations.
Find the Right Level of Detail (or Altitude)
- If categories are too broad, audits may miss important risks (e.g., just saying “Cybersecurity” instead of breaking it into specific areas like “ISMS” or “TPRM”).
- If categories are too detailed, audits may become too complex and difficult to manage (e.g., listing every small security control separately).
- The best approach is a balance; making sure security risks are properly grouped but still detailed enough to catch vulnerabilities.
Identify and Fix Missing Areas
- Compare the security audit universe to the company’s risk assessments. This will help to spot missing security areas that in fact, require audits.
- Check if it matches applicable cybersecurity laws and global security standards relevant to the organization like ISO 27001 or NIST.
- Use an audit matrix or a checklist to ensure all key security risks are included and nothing important is left out.
Organize the Security Audit Universe Properly
- Group security areas in a logical way (e.g., Cybersecurity, IT, Business Continuity etc)
- If the company has offices in different regions or operates internationally, they may be considerations made for location-based security risks.
- Make sure everything fits within the company’s risk management plan and meets applicable cybersecurity regulations.
Find the Right Level of Detail (or Altitude)
- If categories are too broad, audits may miss important risks (e.g., just saying “Cybersecurity” instead of breaking it into specific areas like “ISMS” or “TPRM”).
- If categories are too detailed, audits may become too complex and difficult to manage (e.g., listing every small security control separately).
- The best approach is a balance; making sure security risks are properly grouped but still detailed enough to catch vulnerabilities.
Identify and Fix Missing Areas
- Compare the security audit universe to the company’s risk assessments. This will help to spot missing security areas that in fact, require audits.
- Check if it matches applicable cybersecurity laws and global security standards relevant to the organization like ISO 27001 or NIST.
- Use an audit matrix or a checklist to ensure all key security risks are included and nothing important is left out.
To further understand how to structure the components of a security audit universe, determining the right altitude to strike a balance between broad coverage and detailed risk assessment must be thoroughly understood. Consider the following steps to picking an ideal altitude:
🔹 Match the Audit Universe to the Organization’s IT and Security Structure
- If the organization operates in a hybrid cloud environment, security audits should cover both on-premises and cloud risks separately.
- If security operations are centralized, broader categories like Network Security, Cloud Security, and Endpoint Protection may suffice.
🔹 Find the Right Level of Detail e.g.,
Level | Example | Outcome |
Too Broad | IT Security | Too vague—does not specify areas like data loss prevention, endpoint security, or network security. Key risks may go unnoticed. |
Too Detailed | IT Security → Network Security → Firewall Rules → Rule Configuration for Each Office Location | Overcomplicates the audit process, making it difficult to manage and execute audits efficiently. |
Balanced | IT Security → Network Security → Firewall & IDS/IPS | Provides enough detail to cover risks like unauthorized access and malware while keeping the audit scope manageable. |
Level | Example | Outcome |
Too Broad | Cybersecurity | Too generic—does not clarify whether the audit covers compliance, third-party risks, or security policies. |
Too Detailed | Cybersecurity → ISO 27001 → Clause 9.3 → ISMS Internal Review for Each Business Unit | Overly specific—auditing individual sub-clauses for each business unit makes it difficult to manage at an enterprise scale. |
Balanced | Cybersecurity → ISMS Governance → Risk & Compliance Framework Effectiveness” | Ensures a structured review of ISO 27001 and compliance policies without overwhelming the audit scope. |
🔹 Align with Stakeholder Needs
- Regulators & Compliance Teams require specific breakdowns for cybersecurity audits.
- Executives & Audit Committees prefer high-level insights into security risks.
- Security Teams & Internal Auditors need detailed breakdowns to track vulnerabilities.
🔹 Use Risk-Based Prioritization
- High-risk areas (e.g., Network Security, Cloud Security, Privileged Access Management, and Incident Response) should have detailed audits.
- Lower-risk areas (e.g., Security Awareness Training, Physical Access Controls) can be grouped into broader categories.
🔹 Continuously Review and Update
- The security audit universe should be updated annually or after significant security changes (e.g., new compliance regulations, cyber incidents, digital transformation projects).
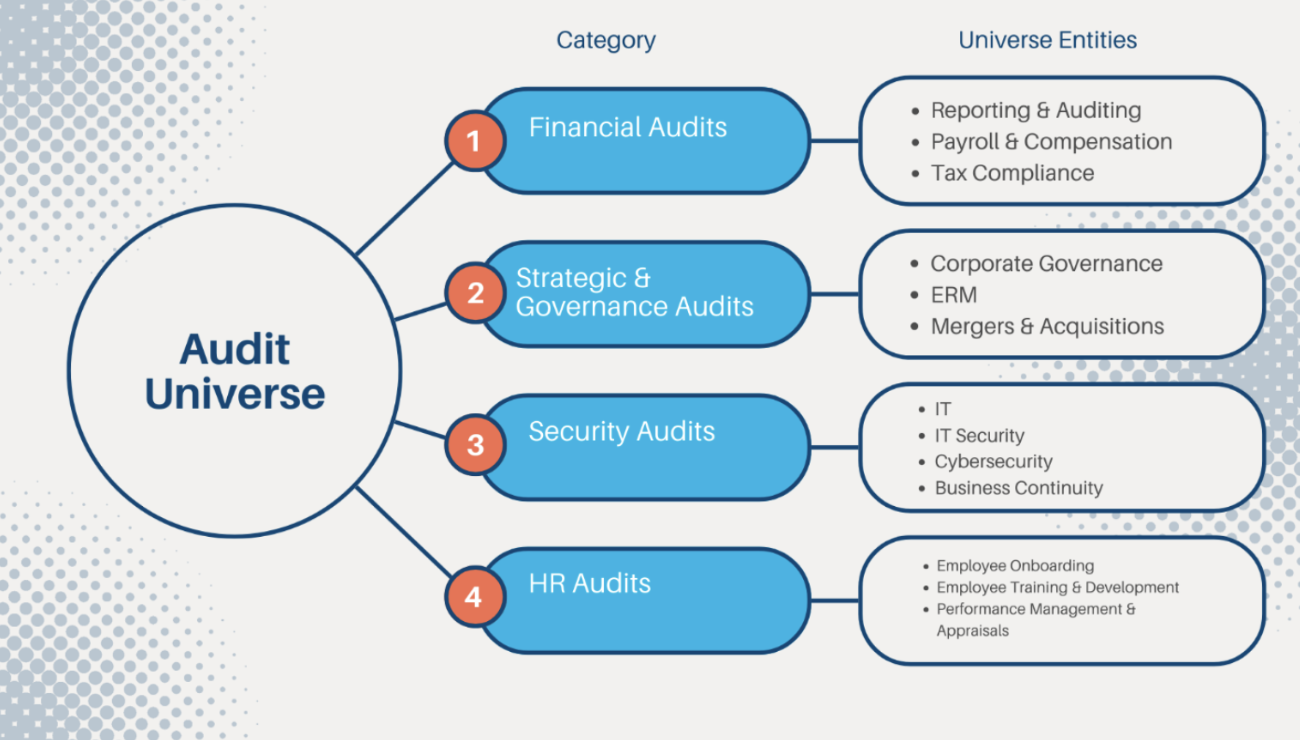
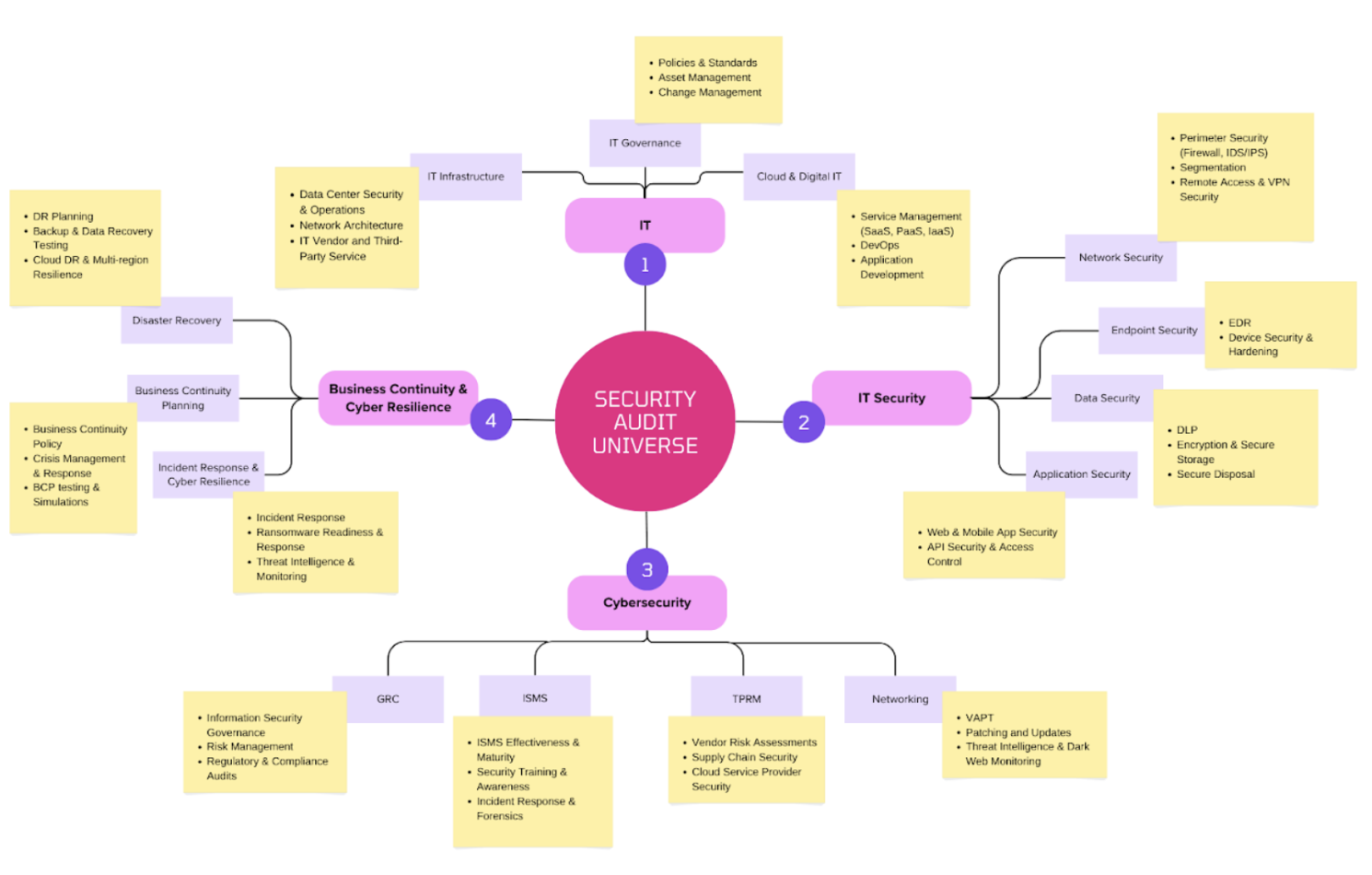
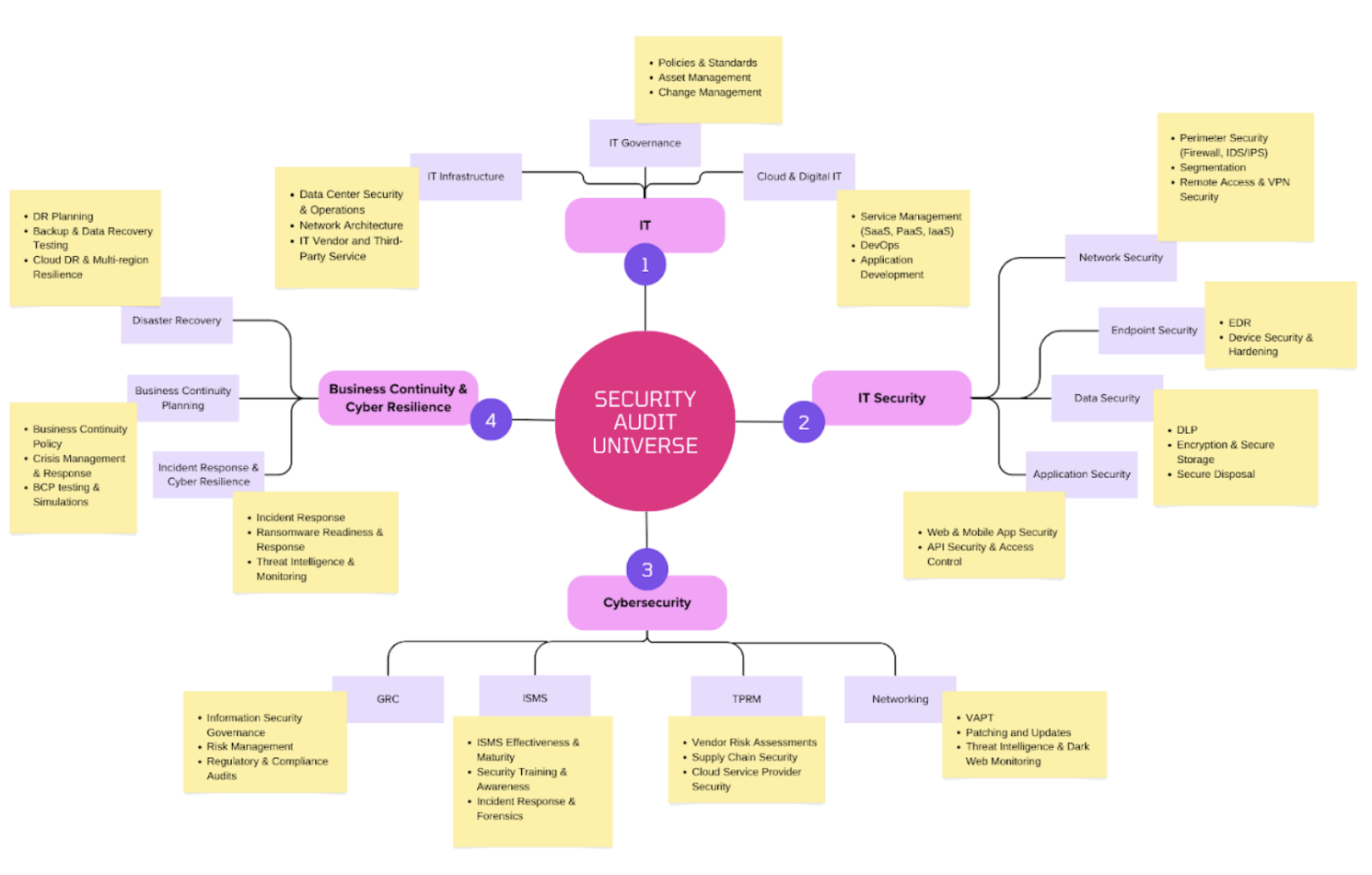
Below is an example of an enterprise-wide audit universe and an expanded security audit universe tailored for a fictional institution focusing on four areas each:
🔹 Match the Audit Universe to the Organization’s IT and Security Structure
- If the organization operates in a hybrid cloud environment, security audits should cover both on-premises and cloud risks separately.
- If security operations are centralized, broader categories like Network Security, Cloud Security, and Endpoint Protection may suffice.
🔹 Find the Right Level of Detail e.g.,
Level | Example | Outcome |
Too Broad | IT Security | Too vague—does not specify areas like data loss prevention, endpoint security, or network security. Key risks may go unnoticed. |
Too Detailed | IT Security → Network Security → Firewall Rules → Rule Configuration for Each Office Location | Overcomplicates the audit process, making it difficult to manage and execute audits efficiently. |
Balanced | IT Security → Network Security → Firewall & IDS/IPS | Provides enough detail to cover risks like unauthorized access and malware while keeping the audit scope manageable. |
Level | Example | Outcome |
Too Broad | Cybersecurity | Too generic—does not clarify whether the audit covers compliance, third-party risks, or security policies. |
Too Detailed | Cybersecurity → ISO 27001 → Clause 9.3 → ISMS Internal Review for Each Business Unit | Overly specific—auditing individual sub-clauses for each business unit makes it difficult to manage at an enterprise scale. |
Balanced | Cybersecurity → ISMS Governance → Risk & Compliance Framework Effectiveness” | Ensures a structured review of ISO 27001 and compliance policies without overwhelming the audit scope. |
🔹 Align with Stakeholder Needs
- Regulators & Compliance Teams require specific breakdowns for cybersecurity audits.
- Executives & Audit Committees prefer high-level insights into security risks.
- Security Teams & Internal Auditors need detailed breakdowns to track vulnerabilities.
🔹 Use Risk-Based Prioritization
- High-risk areas (e.g., Network Security, Cloud Security, Privileged Access Management, and Incident Response) should have detailed audits.
- Lower-risk areas (e.g., Security Awareness Training, Physical Access Controls) can be grouped into broader categories.
🔹 Continuously Review and Update
- The security audit universe should be updated annually or after significant security changes (e.g., new compliance regulations, cyber incidents, digital transformation projects).
Below is an example of an enterprise-wide audit universe and an expanded security audit universe tailored for a fictional institution focusing on four areas each:

Conclusion
A security audit universe is a critical tool for organizations to systematically audit their cybersecurity risks and compliance requirements. By structuring it logically, determining the right altitude, and aligning it with regulatory frameworks, institutions can strengthen their security posture, mitigate risks, and ensure regulatory compliance.
This structured approach ensures that all key security areas are covered, audits remain manageable, and security risks are effectively prioritized.
Conclusion
A security audit universe is a critical tool for organizations to systematically audit their cybersecurity risks and compliance requirements. By structuring it logically, determining the right altitude, and aligning it with regulatory frameworks, institutions can strengthen their security posture, mitigate risks, and ensure regulatory compliance.
This structured approach ensures that all key security areas are covered, audits remain manageable, and security risks are effectively prioritized.
See also:

