Seid Yassin, our Senior VAPT and AppSec Consultant, delivered a compelling session on “Damn Vulnerable RPA – A Hacker’s Perspective” at the Black Hat MEA 2023 conference on 15th November, shedding light on the critical aspects of Robotic Process Automation (RPA) security.
A key member within DTS Solution’s Red Team, Seid Yassin offers essential assurance to clients in the MENA region, spanning both the public and private sectors, concerning the security posture of their products and infrastructure. Armed with nearly a decade of expertise in offensive and defensive information security practices, Seid is well-versed in tackling the complexities of RPA security.
Damn Vulnerable RPA – A Hacker’s Perspective
Seid’s session captivated a packed audience as he covered key topics, including an introduction to RPA, an exploration of DVRPA components and vulnerabilities, insights on attacking and securing DVRPA, emphasizing the importance of RPA security, and sharing mitigation strategies and best practices.
During the session, Seid navigated through the intricacies of RPA security, highlighting potential risks associated with RPA implementations and emphasizing the need for proactive security measures. As organizations increasingly integrate RPA into their operations, understanding and mitigating security challenges become paramount.
Seid Yassin, our Senior VAPT and AppSec Consultant, delivered a compelling session on “Damn Vulnerable RPA – A Hacker’s Perspective” at the Black Hat MEA 2023 conference on 15th November, shedding light on the critical aspects of Robotic Process Automation (RPA) security.
A key member within DTS Solution’s Red Team, Seid Yassin offers essential assurance to clients in the MENA region, spanning both the public and private sectors, concerning the security posture of their products and infrastructure. Armed with nearly a decade of expertise in offensive and defensive information security practices, Seid is well-versed in tackling the complexities of RPA security.

Damn Vulnerable RPA – A Hacker’s Perspective
Seid’s session captivated a packed audience as he covered key topics, including an introduction to RPA, an exploration of DVRPA components and vulnerabilities, insights on attacking and securing DVRPA, emphasizing the importance of RPA security, and sharing mitigation strategies and best practices.
During the session, Seid navigated through the intricacies of RPA security, highlighting potential risks associated with RPA implementations and emphasizing the need for proactive security measures. As organizations increasingly integrate RPA into their operations, understanding and mitigating security challenges become paramount.
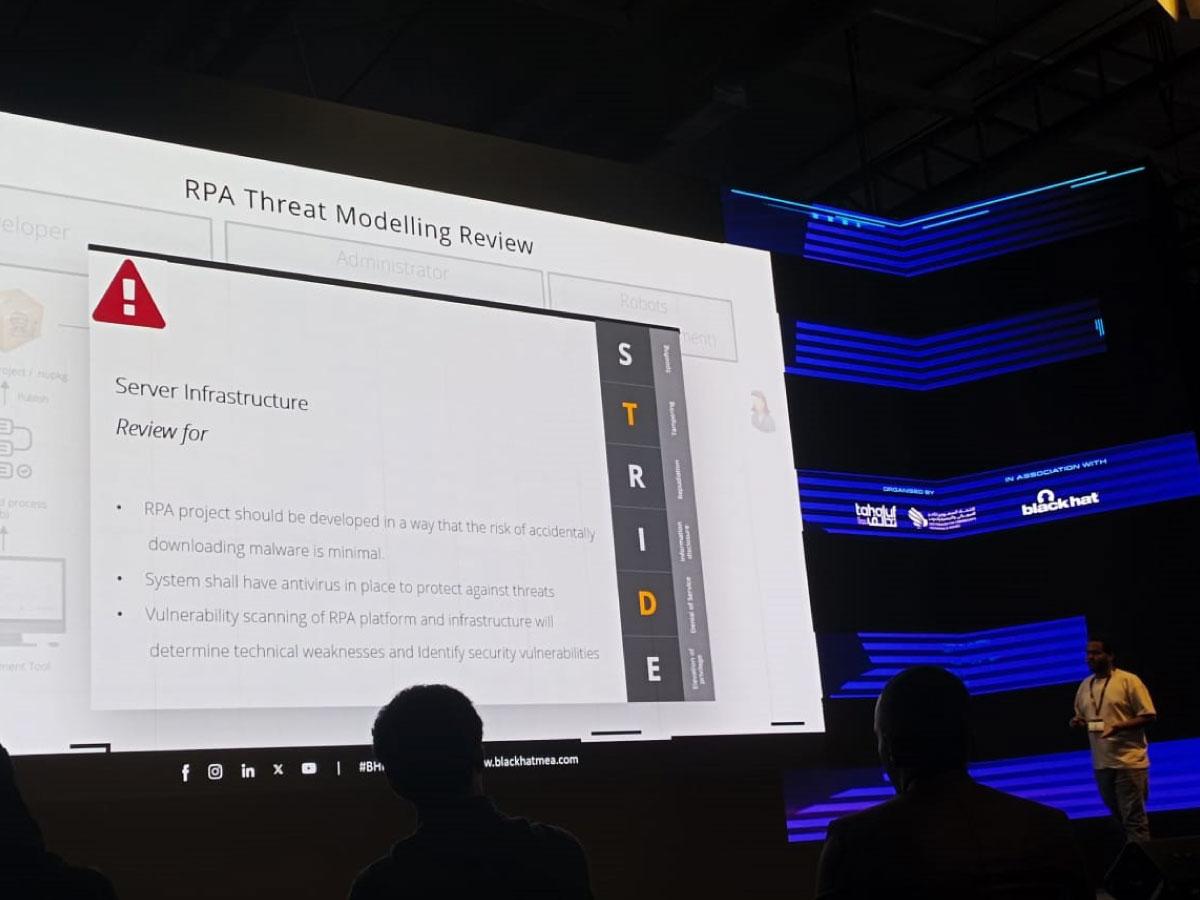
One of the session’s highlights was Seid’s in-depth exploration of security reviews for RPA implementations. Attendees gained insights into methodologies such as threat modeling and source code analysis, essential tools for evaluating and fortifying the security posture of RPA workflows.
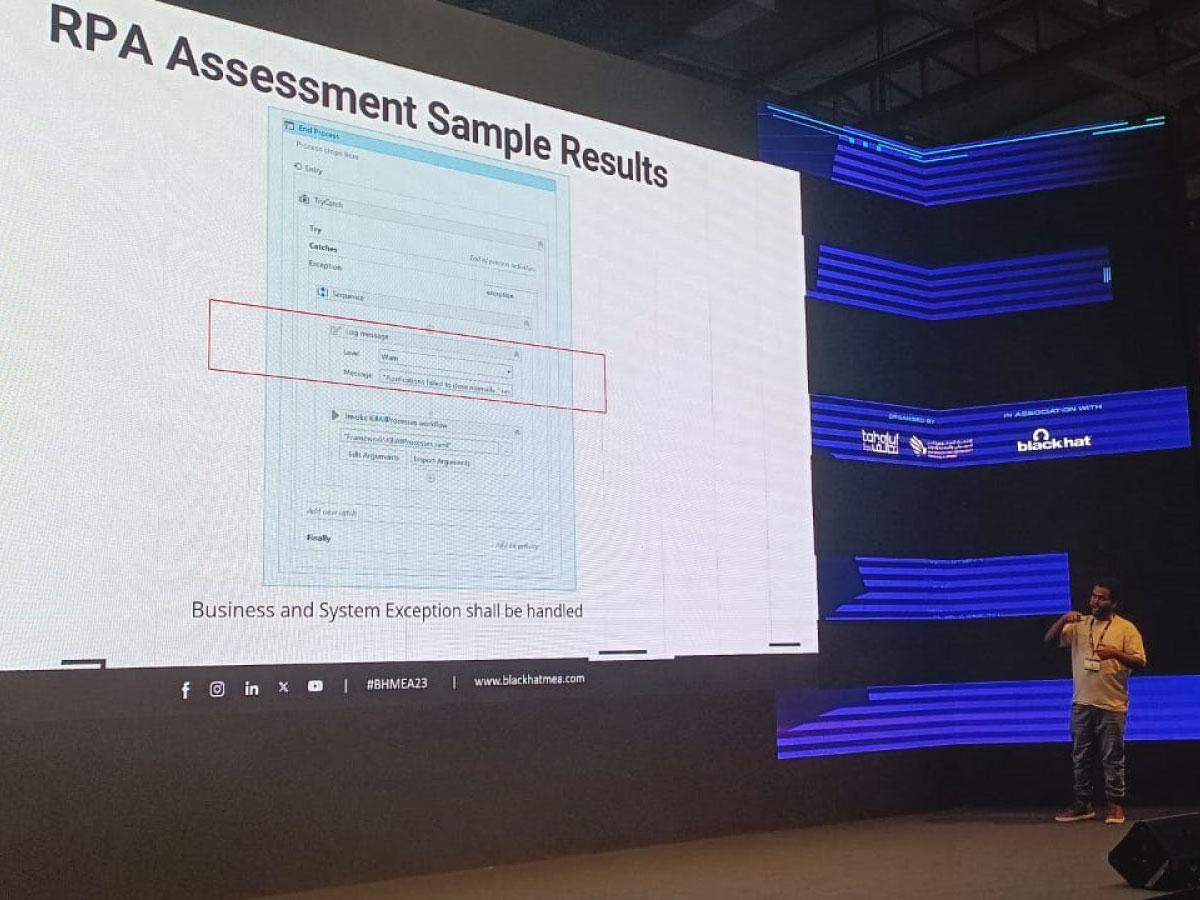
Seid also introduced a groundbreaking initiative – the creation of a Damn Vulnerable RPA process, focusing on invoice extraction. This practical exercise serves as a valuable resource for the information security community, empowering practitioners to enhance their skills in securely reviewing, assessing, and evaluating RPA processes deployed in any organization.
Following Seid’s insightful session, organizations and security practitioners are encouraged to proactively review, assess, and fortify their RPA implementations.
One of the session’s highlights was Seid’s in-depth exploration of security reviews for RPA implementations. Attendees gained insights into methodologies such as threat modeling and source code analysis, essential tools for evaluating and fortifying the security posture of RPA workflows.
Seid also introduced a groundbreaking initiative – the creation of a Damn Vulnerable RPA process, focusing on invoice extraction. This practical exercise serves as a valuable resource for the information security community, empowering practitioners to enhance their skills in securely reviewing, assessing, and evaluating RPA processes deployed in any organization.
Following Seid’s insightful session, organizations and security practitioners are encouraged to proactively review, assess, and fortify their RPA implementations.
See also: