- About Us
-
-
- About UsWe are the regional leaders in cybersecurity. We are masters in our tradecraft. We are dynamic, talented, customer-centric, laser-focused and our mission is to defend and protect our customers from cyber adversaries through advisory, consulting, engineering, and operational services.
-
-
- Solutions
-
-
- SolutionsThe cybersecurity industry is fragmented. We have carefully curated an interoperable suite of cybersecurity products and solutions that focus on improving your security compliance and risk maturity that add real business value, effectiveness, and ROI. Combined with our professional services and security engineering expertise we design, architect, implement and operate complex environments and protect your digital space.
-
- Industry
-
-
- IndustryCyber adversaries and threat actors have no boundaries. No industry is immune to cyber-attacks. Each industry has unique attributes and requirements. At DTS we have served all industry verticals since inception and have built specialization in each segment; to ensure our customers can operate with a high degree of confidence and assurance giving them a competitive advantage.
-
- Services
-
-
- ServicesOur cybersecurity services are unmatched in the region. With our unique customer-centric approach and methodology of SSORR we provide end-to-end strategic and tactical services in cybersecurity. We on-ramp, develop, nurture, build, enhance, operationalize, inject confidence, and empower our customers.
-
-
- Vendors
- Products
- Resources
- Press Center
- Tweets
- Support
- Contact
-
Smart Contract Auditing
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.
Although security controls within Blockchain is inherited – the attack surface on the Bitcoin, Ethereum crypto-currency network has expanded significantly targeting the blockchain security architecture.
Cyber Security for Blockchain Technology
- Confidentiality
- Integrity
- Availability
- Consensus (Vote of Confidence)
- Provenance
- Immutability
- Finality
- Different use cases of Blockchain introduces different cyber security threat vectors
Cyber Security for Blockchain Technology
- Confidentiality
- Integrity
- Availability

- Consensus (Vote of Confidence)
- Provenance
- Immutability
- Finality
- Different use cases of Blockchain introduces different cyber security threat vectors
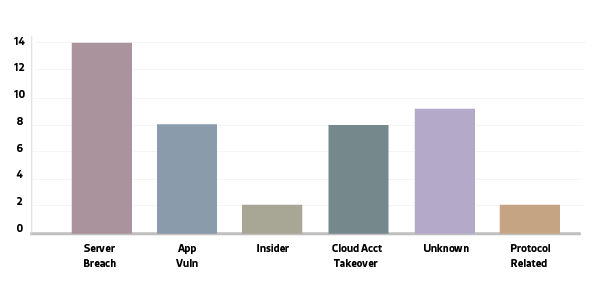
- The DAO hack wiped $50m of crypto-currency value of the crowd-funding venture
- Bitfinex – Hong Kong based crypto-currency exchange cyber theft of $68s
- Mt. Gox filed for bankruptcy post security breach where 850K Bitcoins were stolen ($450m)
- List of all publicly known blockchain breaches and root cause;
- BITFINEX
- DAO
- GATECOIN
- COINKITE
- MT GOX
- COINWALLET
- COINTRADER
- BITQUICK
- SHAPESHIFT
- CRYPTSY
- BITPAY
- BITSTAMP
- ALLCRYPT
- CRYPTOINE
- EXCOIN
- THE LIST GOES ON….


- The DAO hack wiped $50m of crypto-currency value of the crowd-funding venture
- Bitfinex – Hong Kong based crypto-currency exchange cyber theft of $68s
- Mt. Gox filed for bankruptcy post security breach where 850K Bitcoins were stolen ($450m)
- List of all publicly known blockchain breaches and root cause;
- BITFINEX
- DAO
- GATECOIN
- COINKITE
- MT GOX
- COINWALLET
- COINTRADER
- BITQUICK
- SHAPESHIFT
- CRYPTSY
- BITPAY
- BITSTAMP
- ALLCRYPT
- CRYPTOINE
- EXCOIN
- THE LIST GOES ON….

Our Approach
Our Approach
TRANSACTIONAL LEVEL
Transaction Validation
Transaction Signing
Transaction Auditing
Transaction Logging
Consensus Life-cycle
Consensus Algorithm
Consensus Code Development
Source Code Review
Auto-Update Life-cycle
Non-Repudiation
Keyless Security Infrastructure (KSI)
Application Security
Key Management
Immutability Protection
Data Integrity
Finality Protection
Multi-Signature Co-Signing
Policy and Security
Approval and Workflows
Permissioned and Permission-less
Hardware (HSM) Crypto
ACCOUNT LEVEL
User Account Management
User Account Security
Authentication Profiles
Two-Factor Authentication
Self-Managed Wallet Security
Exchange Hosted Account Security
Denial of Services (DoS)
Phishing Prevention and Security
Hosted Exchanges
Wallet Provider Security Controls
My Wallet Security Controls
Logging and Auditing
Application Security
Sessions and Cookie Management
Local Storage Security
Personal and Privacy Information
Policy and Security
Role Based Access Control
Multi-Tenancy
Privacy and Identity Management
Account Verification Process
CONTRACT LEVEL
Script Source Code Review
Contract Code Audit
Programming Security
Secure Development Life-cycle
Contract Threat Correlation
Threat Simulation Smart Rules
Contract Verification Workflow
Fallback function security
Bug Identification
Variable Limiting
Program function validation
Call stack limit vulnerability
Contract Data Classification
Proof of Work
Smart Contract Cryptography
Re-entrancy Protection
Contract Vulnerability Assessment
Check Effect Interaction Pattern
Function Wrapping
Compiler Bugs
Unbound Loops
DISTRIBUTED ORGANIZATION LEVEL
Organization Level Security and Conformity Requirements
Technical Security Requirements
Token Assignment
Token Authorization
Validators Security Control
Censorship Policy
Blockchain contract approval workflow
Entity Level Security Validation
Security Readiness Verification
HSM Crypto
Key Management
Application Security
Multi-Signature Co-Signing
Distributed Authorization Process
NETWORK AND APPLICATION LEVEL
Permissioned Network
Open or Hybrid Architecture
P2P Network Security Architecture
VPN and secure communication
Next Generation Firewalls
Security Zoning
Network Segmentation
Intrusion Prevention System
Web Application Security Controls
API Security Gateway
PKI Security Infrastructure
Virtual Machine Infrastructure
Data Center Switching
Data Center Routing
Protocol Security
In-band and Out of band Management
Threat intelligence
Phishing Security
Threat Hunting
GOVERNANCE LEVEL
Security Operations
Logging and Monitoring
Governance and Compliance
Risk Management
Data Security
Data Classification
Data Labelling
Transactional Records
Smart Contract Tagging
Security Approval Workflows
Information Security Policies
Security Processes and Procedures
Asset Management
Disaster Recovery
Backup and Restoration
Security Awareness and Training
What is a Smart Contract?
- Smart contracts can be thought of as an account without a private key
- It cannot be governed by a group or individual
- Solely governed by the code within the contract
- Smart contracts are immutable
Why audit a smart contract?
- Immutability
- Unchanging over time or unable to be changed
- How to make a change in a smart contract? -> "Make a new smart contract”
Attacks on a smart contract
What is a Smart Contract?
- Smart contracts can be thought of as an account without a private key
- It cannot be governed by a group or individual
- Solely governed by the code within the contract
- Smart contracts are immutable

Why audit a smart contract?
- Immutability
- Unchanging over time or unable to be changed
- How to make a change in a smart contract? -> "Make a new smart contract”
Attacks on a smart contract
Private key theft
- An attacker having access to private keys can send all ETH from the victims account.
- Attacker usually gains access to private keys using phishing.
51% attack
- This attack occurs when an attacker or a group of attackers own 51 percent of the mining hash rate.
- It is hypothetical in public networks.
- Fairly reachable in private networks
Logic flaws in the contract code
- Logic flaws can be different in various decentralized apps or DAPPs. But the reason it is highlighted here is because once a contract is published, it cannot be edited.
Re-entrancy attacks
- Here attacker use the logical flaws in the vulnerable contract to withdraw more funds that what they are supposed to get.
Call to the unknown
- This attack is famous in ponzi scheme contracts. Here an attacker claims the leadership role via providing sufficient ether. When another person tries to claim leadership, the attackers malicious contract runs a revert state. This in short renders a permanent DoS.
Declaring a private function to store secret data
- All data in a contract is visible to the participants in the blockchain. The is the whole point of decentralization. Devs cannot store secret info thinking it will remain only known to the Dev team.
Practical examples of flaws in SMART CONTRACTS
This function gets the user’s balance and sets it to the “amountToWithdraw” variable. Then, the function sends the user the amount set in the “amountToWithdraw” variable. If the transaction is successful the “userBalances” is set to 0 because all the funds deposited in the balance are sent to the user
function withdrawBalance() {
uint amountToWithdraw = userBalances[msg.sender];
if (msg.sender.call.value(amountToWithdraw)() == false) {
throw;
}
userBalances[msg.sender] = 0;
}
function forwardFunds(address receiver, uint amount) public {
require(balances[msg.sender] >= amount);
receiver.transfer(amount);
balances[receiver] -= amount;
LogFundsForwarded(msg.sender, receiver, amount);
}
Practical examples of flaws in SMART CONTRACTS
This function gets the user’s balance and sets it to the “amountToWithdraw” variable. Then, the function sends the user the amount set in the “amountToWithdraw” variable. If the transaction is successful the “userBalances” is set to 0 because all the funds deposited in the balance are sent to the user
function withdrawBalance() {
uint amountToWithdraw = userBalances[msg.sender];
if (msg.sender.call.value(amountToWithdraw)() == false) {
throw;
}
userBalances[msg.sender] = 0;
}
function forwardFunds(address receiver, uint amount) public {
require(balances[msg.sender] >= amount);
receiver.transfer(amount);
balances[receiver] -= amount;
LogFundsForwarded(msg.sender, receiver, amount);
}
Solutions
Network and Infrastructure Security
Zero Trust and Private Access
Endpoint and Server Protection
Vulnerability and Patch Management
Data Protection
Application Security
Secure Software and DevSecOps
Cloud Security
Identity Access Governance
Governance, Risk and Compliance
Security Intelligence Operations
Incident Response
Accreditations


Accreditations


Dubai
Office 7, Floor 14
Makeen Tower, Al Mawkib St.
Al Zahiya Area
Abu Dhabi, UAE
Sama Tower, Floor 7
Moh. Thunayan AlGhanim Str.
Jibla, Kuwait City
Kuwait
160 Kemp House, City Road
London, EC1V 2NX
United Kingdom
Company Number: 10276574
Riyadh
Office 109, Aban Center
King Abdulaziz Road
Al Ghadir
Riyadh, Saudi Arabia
The website is our proprietary property and all source code, databases, functionality, software, website designs, audio, video, text, photographs, icons and graphics on the website (collectively, the “Content”) are owned or controlled by us or licensed to us, and are protected by copyright laws and various other intellectual property rights. The content and graphics may not be copied, in part or full, without the express permission of DTS Solution LLC (owner) who reserves all rights.
DTS Solution, DTS-Solution.com, the DTS Solution logo, HAWKEYE, FYNSEC, FRONTAL, HAWKEYE CSOC WIKI and Firewall Policy Builder are registered trademarks of DTS Solution, LLC.