- About Us
-
-
- About UsWe are the regional leaders in cybersecurity. We are masters in our tradecraft. We are dynamic, talented, customer-centric, laser-focused and our mission is to defend and protect our customers from cyber adversaries through advisory, consulting, engineering, and operational services.
-
-
- Solutions
-
-
- SolutionsThe cybersecurity industry is fragmented. We have carefully curated an interoperable suite of cybersecurity products and solutions that focus on improving your security compliance and risk maturity that add real business value, effectiveness, and ROI. Combined with our professional services and security engineering expertise we design, architect, implement and operate complex environments and protect your digital space.
-
- Industry
-
-
- IndustryCyber adversaries and threat actors have no boundaries. No industry is immune to cyber-attacks. Each industry has unique attributes and requirements. At DTS we have served all industry verticals since inception and have built specialization in each segment; to ensure our customers can operate with a high degree of confidence and assurance giving them a competitive advantage.
-
- Services
-
-
- ServicesOur cybersecurity services are unmatched in the region. With our unique customer-centric approach and methodology of SSORR we provide end-to-end strategic and tactical services in cybersecurity. We on-ramp, develop, nurture, build, enhance, operationalize, inject confidence, and empower our customers.
-
-
- Vendors
- Products
- Resources
- Press Center
- Tweets
- Support
- Contact
-
APT Zero Day Malware
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.
The Middle East saw a significant rise in APT targeted attacked towards large enterprises to cause significant impact – Saudi Aramco, RASGAS, RAKBANK, NTA UAE, UAE Central Bank and Abu Dhabi Exchange to name a few. DTS is at the forefront of providing advanced APT security solutions and has been working with some of these clients post-incident to develop security operations centers and build a security monitoring framework.
The Middle East saw a significant rise in APT targeted attacked towards large enterprises to cause significant impact – Saudi Aramco, RASGAS, RAKBANK, NTA UAE, UAE Central Bank and Abu Dhabi Exchange to name a few. DTS is at the forefront of providing advanced APT security solutions and has been working with some of these clients post-incident to develop security operations centers and build a security monitoring framework.
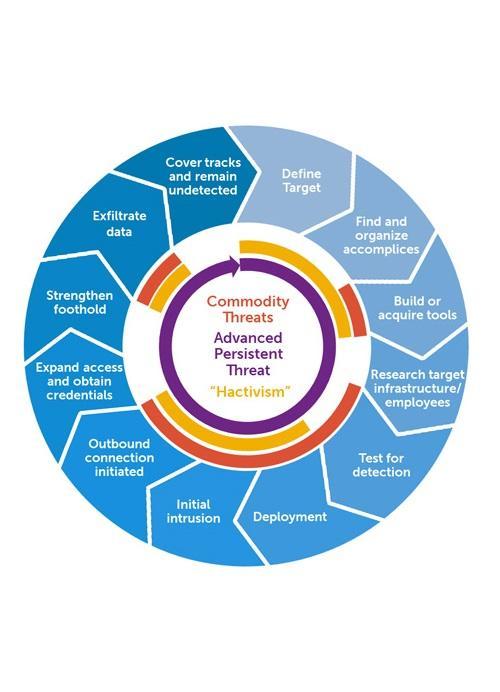
Advance Persistent Threat Life Cycle
- Target specific organizations for a singular objective
- Attempt to gain a foothold in the environment, common tactics include spear phishing emails.
- Use the compromised systems as access into the target network
- Deploy additional tools that help fulfill the attack objective
- Cover tracks to maintain access for future initiatives
Research into the APT life cycle illustrate some attacks using APT methodology that infected endpoints and were resident within the enterprise over 8 years;
- Initial compromise — performed by use of social engineering and spear phishing, over email, using zero-day viruses. Another popular infection method was planting malware on a website that the victim employees will be likely to visit.
- Establish Foothold — plant remote administration software in victim's network, create network backdoors and tunnels allowing stealth access to its infrastructure.
- Escalate Privileges — use exploits and password cracking to acquire administrator privileges over victim's computer and possibly expand it to Windows domain administrator accounts.
- Internal Reconnaissance — collect information on surrounding infrastructure, trust relationships, Windows domain structure.
- Move Laterally — expand control to other workstations, servers and infrastructure elements and perform data harvesting on them.
- Maintain Presence — ensure continued control over access channels and credentials acquired in previous steps.
- Complete Mission — exfiltrate stolen data from victim's network.
Advance Persistent Threat Life Cycle
- Target specific organizations for a singular objective
- Attempt to gain a foothold in the environment, common tactics include spear phishing emails.
- Use the compromised systems as access into the target network
- Deploy additional tools that help fulfill the attack objective
- Cover tracks to maintain access for future initiatives
- Initial compromise — performed by use of social engineering and spear phishing, over email, using zero-day viruses. Another popular infection method was planting malware on a website that the victim employees will be likely to visit.
- Establish Foothold — plant remote administration software in victim's network, create network backdoors and tunnels allowing stealth access to its infrastructure.
- Escalate Privileges — use exploits and password cracking to acquire administrator privileges over victim's computer and possibly expand it to Windows domain administrator accounts.
- Internal Reconnaissance — collect information on surrounding infrastructure, trust relationships, Windows domain structure.
- Move Laterally — expand control to other workstations, servers and infrastructure elements and perform data harvesting on them.
- Maintain Presence — ensure continued control over access channels and credentials acquired in previous steps.
- Complete Mission — exfiltrate stolen data from victim's network.
A universal detection method for advanced malware across various applications.
A universal detection method for advanced malware across various applications.

High-Resolution Security Analysis
DTS Solution works with Lastline to provide the most comprehensive Zero Day Malware detection systems. Lastline’s full-system emulation functionality dissects not only APTs, but malware crafted to evade detection by traditional sandboxes used by first-generation APT security vendors.

High-Resolution Security Analysis
DTS Solution works with Lastline to provide the most comprehensive Zero Day Malware detection systems. Lastline’s full-system emulation functionality dissects not only APTs, but malware crafted to evade detection by traditional sandboxes used by first-generation APT security vendors.
Global Threat Intelligence
DTS Solution preferred vendor of choice for Zero Day Malware detection Lastline has the ability to crawl the web utilizing emulated browsers, machine learning, information on objects analyzed and big data analytics to build a knowledge base of malicious objects, bad IP addresses and active command-and-control systems.

Global Threat Intelligence
DTS Solution preferred vendor of choice for Zero Day Malware detection Lastline has the ability to crawl the web utilizing emulated browsers, machine learning, information on objects analyzed and big data analytics to build a knowledge base of malicious objects, bad IP addresses and active command-and-control systems.
Increase your coverage without increasing your costs
Distributed Architecture That Scales
Flexible architecture allows for easy scalability as your architectural, operational and business needs change. We offer organizations the ability to deploy on commodity hardware or in virtual environments on a per-user basis, so go ahead, deploy as much as you’d like. Expensive proprietary hardware is a thing of the past.
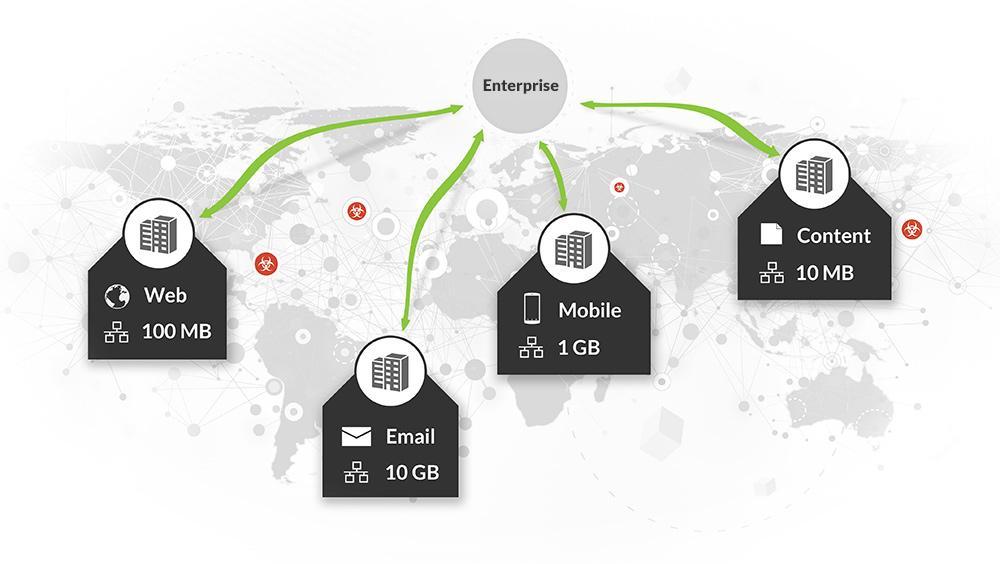
Increase your coverage without increasing your costs

Distributed Architecture That Scales
Flexible architecture allows for easy scalability as your architectural, operational and business needs change. We offer organizations the ability to deploy on commodity hardware or in virtual environments on a per-user basis, so go ahead, deploy as much as you’d like. Expensive proprietary hardware is a thing of the past.
Stop filtering through alerts. Start blocking threats
Actionable Threat Intelligence
When a threat is serious, you will know. Lastline makes it easy for you to identify critical APTs targeting your network. Network activity is correlated with information resulting from the execution of software artifacts, providing an incident-centric view of infections. The ability to link together the various steps involved in the compromise of an internal endpoint supports root-cause analysis and more effective remediation.
Stop filtering through alerts. Start blocking threats

Actionable Threat Intelligence
When a threat is serious, you will know. Lastline makes it easy for you to identify critical APTs targeting your network. Network activity is correlated with information resulting from the execution of software artifacts, providing an incident-centric view of infections. The ability to link together the various steps involved in the compromise of an internal endpoint supports root-cause analysis and more effective remediation.
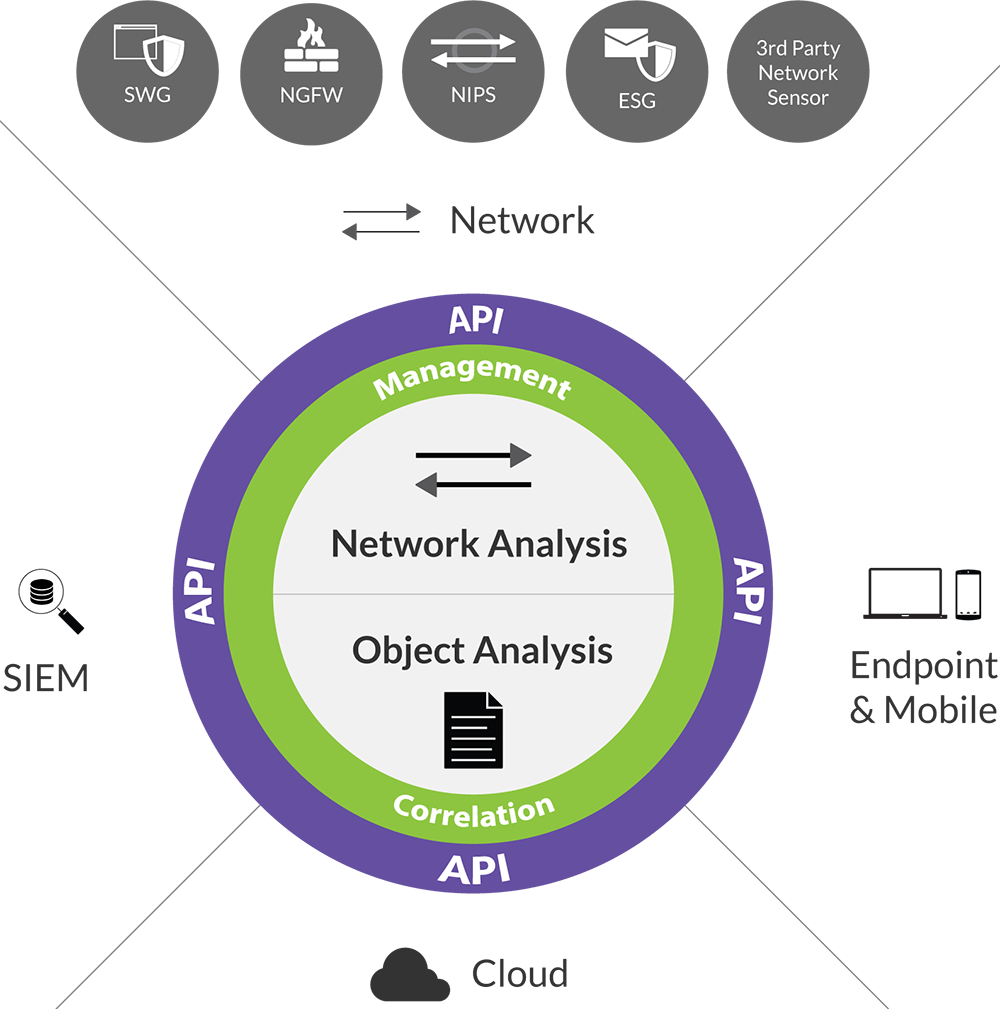
Ensure end-to-end interoperability
Integrate With Traditional Security Systems
Lastline’s unrivaled API capabilities allow you to easily integrate our software solution with existing security infrastructures to add malware analysis and better protect against advanced cyber threats. Use your own sensors or existing technologies — SWGs (Secure Web Gateways), IPSs (Intrusion Protection System), NGFWs (Next-Generation Firewalls) and SIEM (Security Information Event Management) installations can all interoperate seamlessly with Lastline Enterprise.
Ensure end-to-end interoperability
Integrate With Traditional Security Systems
Lastline’s unrivaled API capabilities allow you to easily integrate our software solution with existing security infrastructures to add malware analysis and better protect against advanced cyber threats. Use your own sensors or existing technologies — SWGs (Secure Web Gateways), IPSs (Intrusion Protection System), NGFWs (Next-Generation Firewalls) and SIEM (Security Information Event Management) installations can all interoperate seamlessly with Lastline Enterprise.
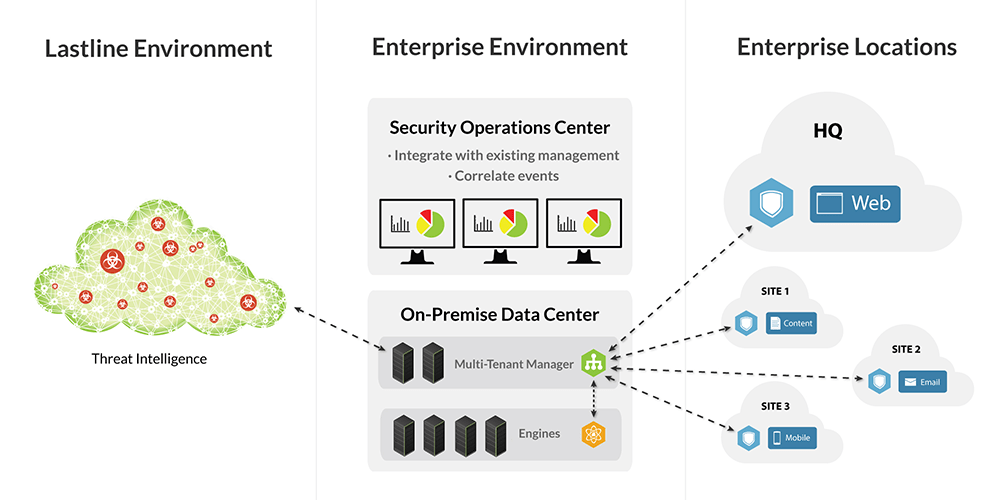
On-Premise Deployment
Deploy in your private cloud or ours...
Lastline Enterprise was designed with flexibility in mind. If your Enterprise is restricted by strict privacy laws and policies, deploy on-premise, and install components in your data center. Network behavior models associated with malware will be regularly downloaded from Lastline. Or choose the hosted deployment model and Lastline will manage the backend infrastructure for you.
On-Premise Deployment
Deploy in your private cloud or ours...
Lastline Enterprise was designed with flexibility in mind. If your Enterprise is restricted by strict privacy laws and policies, deploy on-premise, and install components in your data center. Network behavior models associated with malware will be regularly downloaded from Lastline. Or choose the hosted deployment model and Lastline will manage the backend infrastructure for you.
Solutions
Network and Infrastructure Security
Zero Trust and Private Access
Endpoint and Server Protection
Vulnerability and Patch Management
Data Protection
Application Security
Secure Software and DevSecOps
Cloud Security
Identity Access Governance
Governance, Risk and Compliance
Security Intelligence Operations
Incident Response
Accreditations


Accreditations


Dubai
Office 7, Floor 14
Makeen Tower, Al Mawkib St.
Al Zahiya Area
Abu Dhabi, UAE
Mezzanine Floor, Tower 3
Mohammad Thunayyan Al-Ghanem Street, Jibla
Kuwait City, Kuwait
+971 4 3383365
[email protected]
160 Kemp House, City Road
London, EC1V 2NX
United Kingdom
Company Number: 10276574
The website is our proprietary property and all source code, databases, functionality, software, website designs, audio, video, text, photographs, icons and graphics on the website (collectively, the “Content”) are owned or controlled by us or licensed to us, and are protected by copyright laws and various other intellectual property rights. The content and graphics may not be copied, in part or full, without the express permission of DTS Solution LLC (owner) who reserves all rights.
DTS Solution, DTS-Solution.com, the DTS Solution logo, HAWKEYE, FYNSEC, FRONTAL, HAWKEYE CSOC WIKI and Firewall Policy Builder are registered trademarks of DTS Solution, LLC.