- About Us
-
-
- About UsWe are the regional leaders in cybersecurity. We are masters in our tradecraft. We are dynamic, talented, customer-centric, laser-focused and our mission is to defend and protect our customers from cyber adversaries through advisory, consulting, engineering, and operational services.
-
-
- Solutions
-
-
- SolutionsThe cybersecurity industry is fragmented. We have carefully curated an interoperable suite of cybersecurity products and solutions that focus on improving your security compliance and risk maturity that add real business value, effectiveness, and ROI. Combined with our professional services and security engineering expertise we design, architect, implement and operate complex environments and protect your digital space.
-
- Industry
-
-
- IndustryCyber adversaries and threat actors have no boundaries. No industry is immune to cyber-attacks. Each industry has unique attributes and requirements. At DTS we have served all industry verticals since inception and have built specialization in each segment; to ensure our customers can operate with a high degree of confidence and assurance giving them a competitive advantage.
-
- Services
-
-
- ServicesOur cybersecurity services are unmatched in the region. With our unique customer-centric approach and methodology of SSORR we provide end-to-end strategic and tactical services in cybersecurity. We on-ramp, develop, nurture, build, enhance, operationalize, inject confidence, and empower our customers.
-
-
- Vendors
- Products
- Resources
- Press Center
- Tweets
- Support
- Contact
-
Firewall Compliance Management
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.
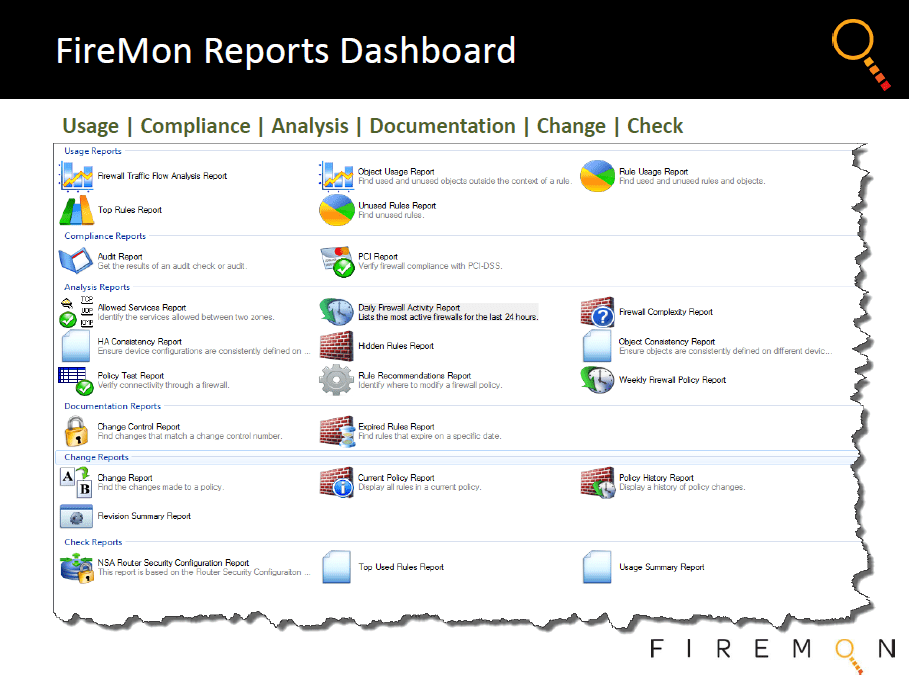
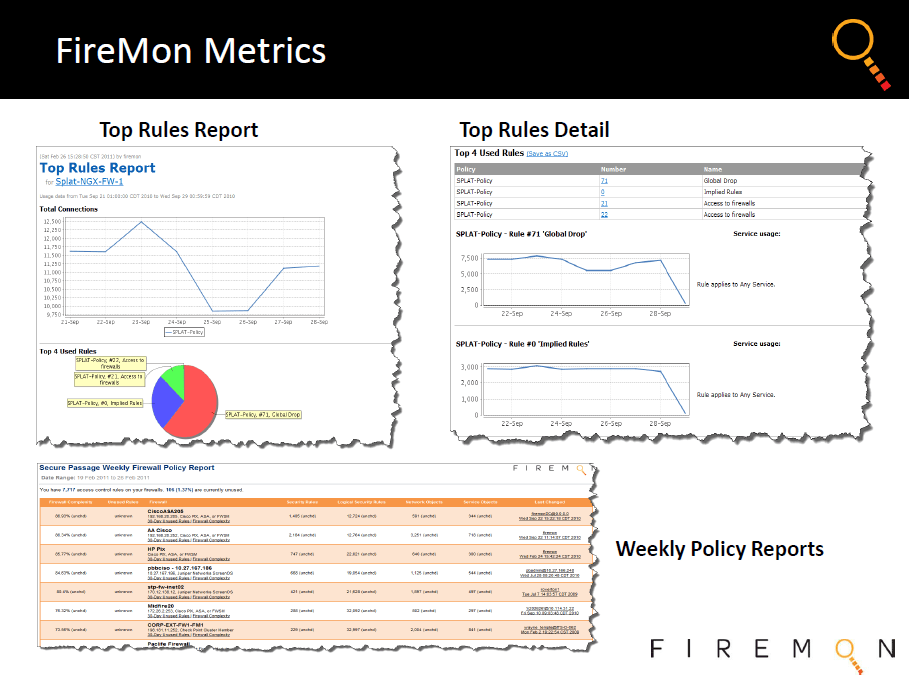
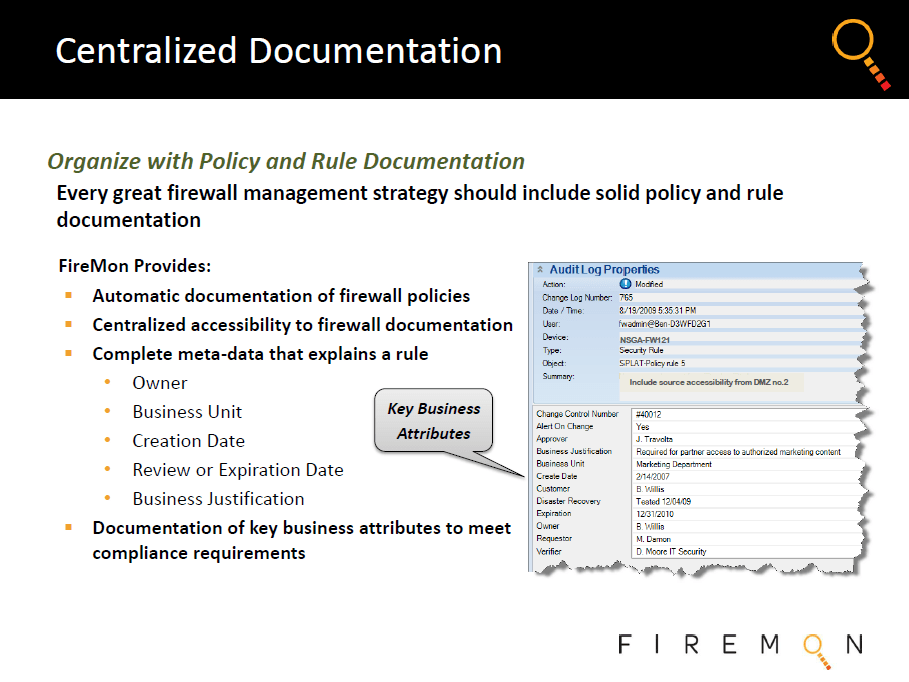
With FireMon, network and security teams can maintain a single, definitive view into the configurations of devices made by all major firewall vendors and present data in a centralized, real-time, customizable dashboard that provides reports to inform numerous management processes.
- Analyze, manage and control firewall configurations centrally and more accurately
- Cleanup and improve policies to reduce complexity and limit access, even as demands change
- Cleanup device rules across the entire network to ensure that policies result in end-to-end protection
- Migrate firewalls and legacy devices faster, validating that defenses remain in place
- Analyze and report on compliance to comply with regulations and document mandated assessment
- Identify underlying instances of IT risk left exposed to access and inform necessary remediation efforts
- Retain real-time visibility into the effectiveness of all security device infrastructure to continually adjust defenses as requirements change
- Analyze, manage and control firewall configurations centrally and more accurately
- Cleanup and improve policies to reduce complexity and limit access, even as demands change
- Cleanup device rules across the entire network to ensure that policies result in end-to-end protection
- Migrate firewalls and legacy devices faster, validating that defenses remain in place
- Analyze and report on compliance to comply with regulations and document mandated assessment
- Identify underlying instances of IT risk left exposed to access and inform necessary remediation efforts
- Retain real-time visibility into the effectiveness of all security device infrastructure to continually adjust defenses as requirements change
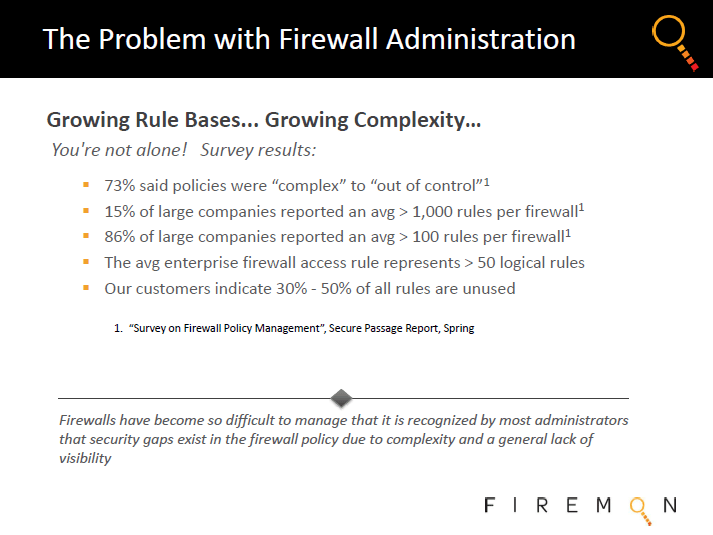
The Firewall Management Challenge......
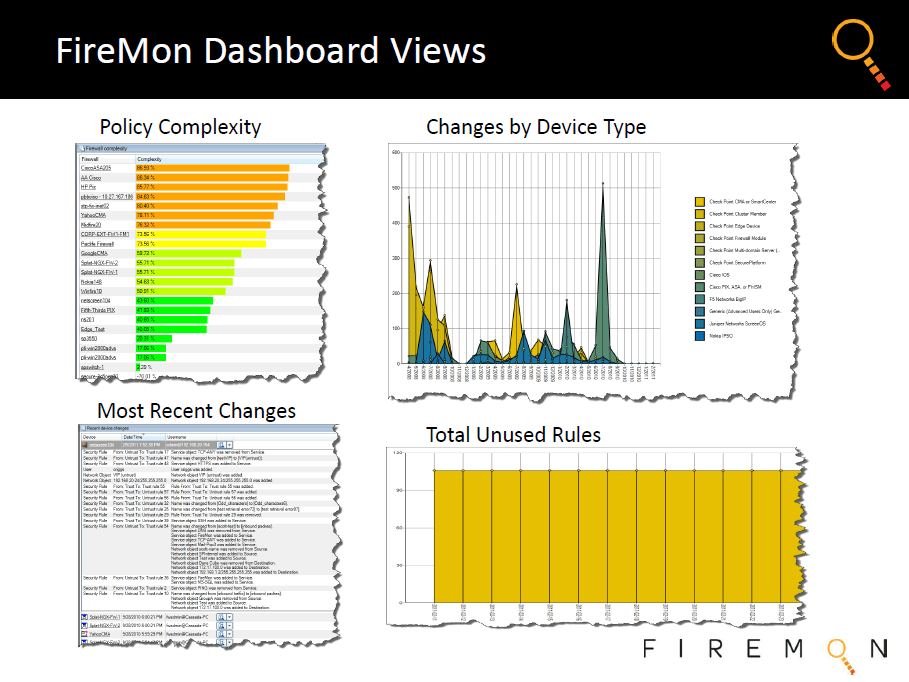
Firewall Visibility and Monitoring....
With FireMon, network and security teams can maintain a single, definitive view into the configurations of devices made by all major firewall vendors and present data in a centralized, real-time, customizable dashboard that provides reports to inform numerous management processes.
Firewall Visibility and Monitoring....
With FireMon, network and security teams can maintain a single, definitive view into the configurations of devices made by all major firewall vendors and present data in a centralized, real-time, customizable dashboard that provides reports to inform numerous management processes.
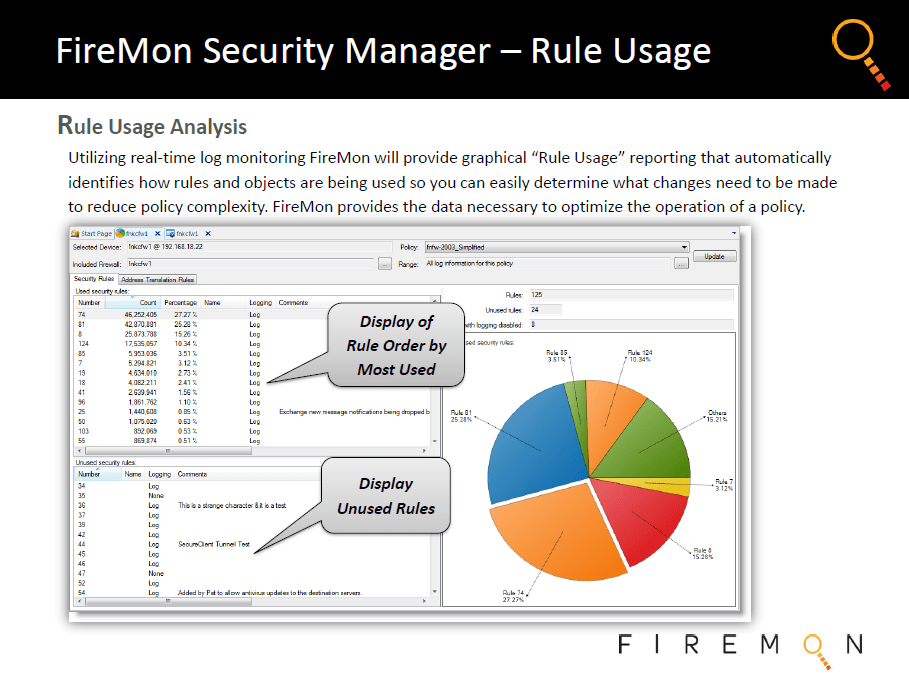
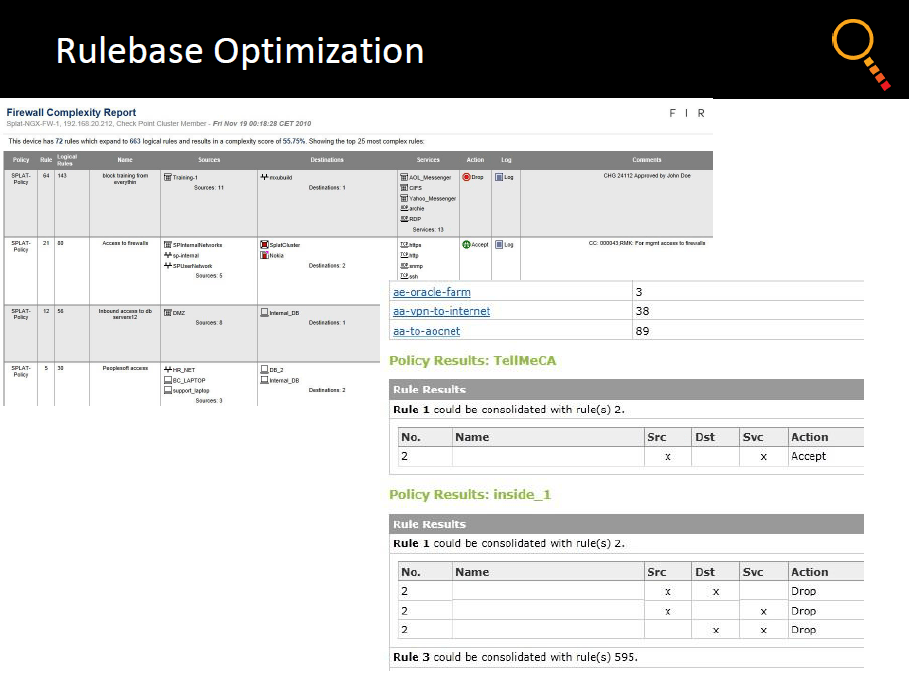
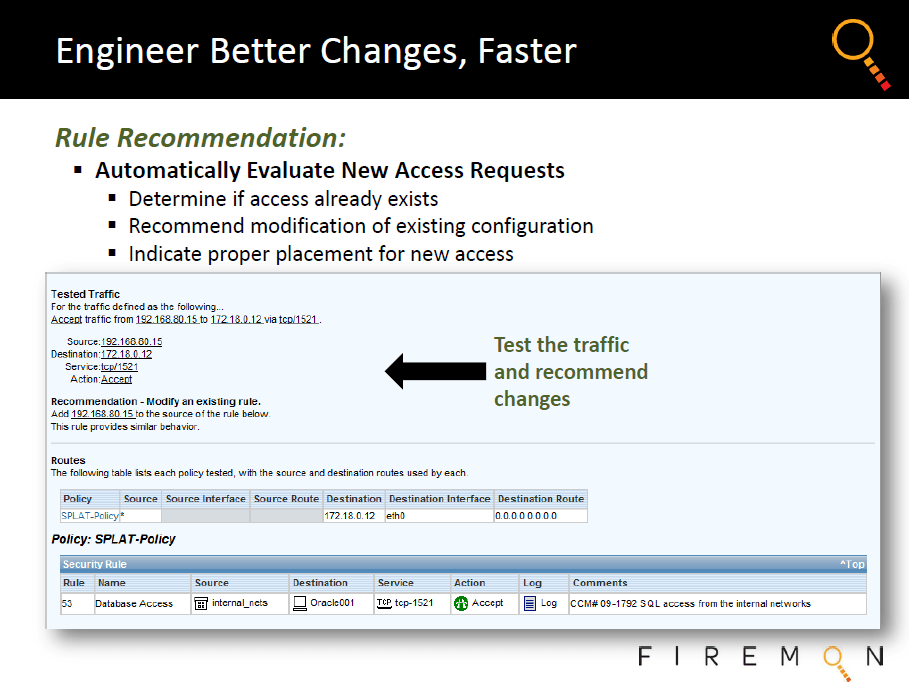
Firewall Policy Optimization....
By taking a more comprehensive, hands-on approach to security device infrastructure management, yet doing so via adoption of automated assessment and remediation intelligence, organizations can reduce IT risk and improve protection, while simplifying compliance. In addition, this keeps network performance optimized, which further enables core business efforts.
Firewall Policy Optimization....
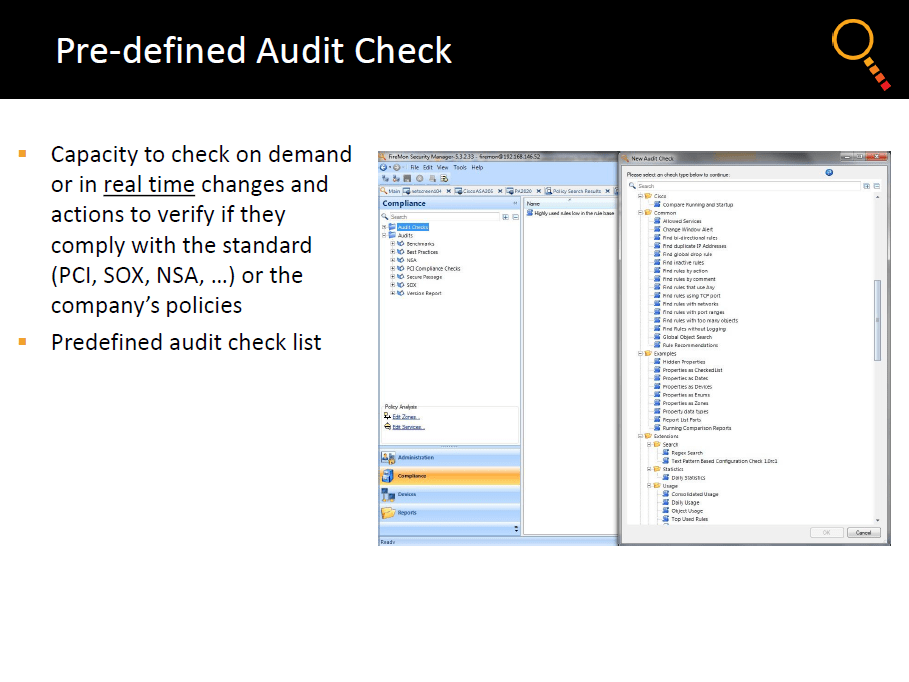
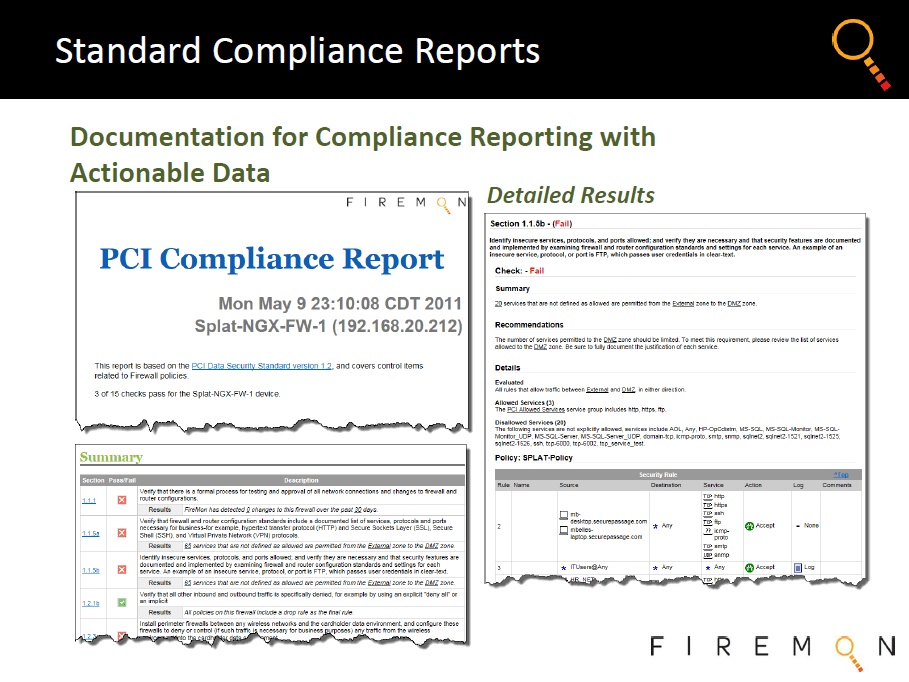
Firewall Audit and Compliance.....
With onboard capability to test for popular security requirements such as the PCI DSS standard, FireMon Security Manager represents an even more conclusive and detailed analysis of both policy compliance and the ability to meet the underlying goals of such measures in validating real world IT risk mitigation.
Firewall Audit and Compliance.....
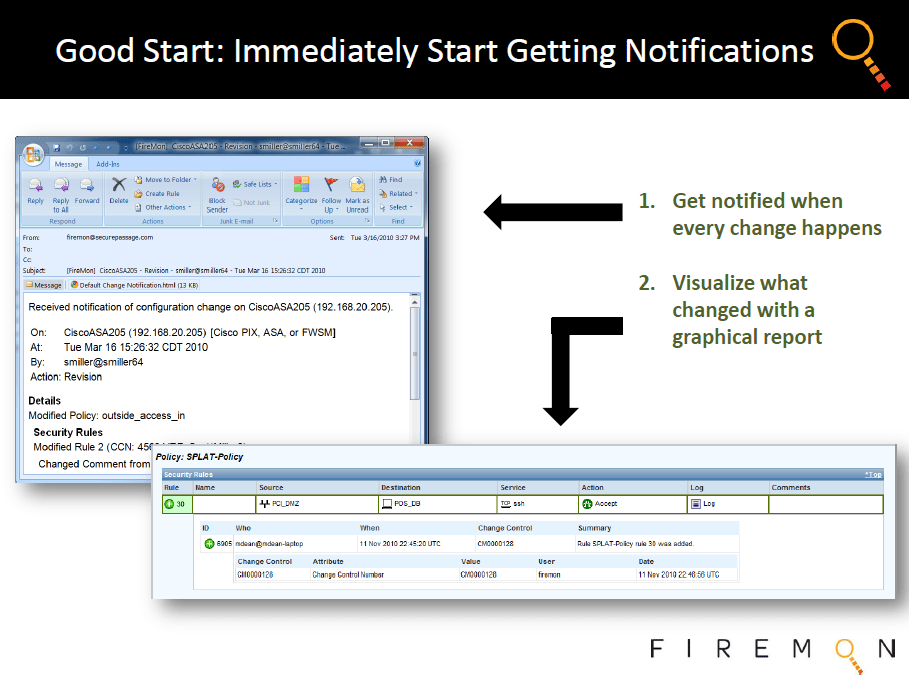
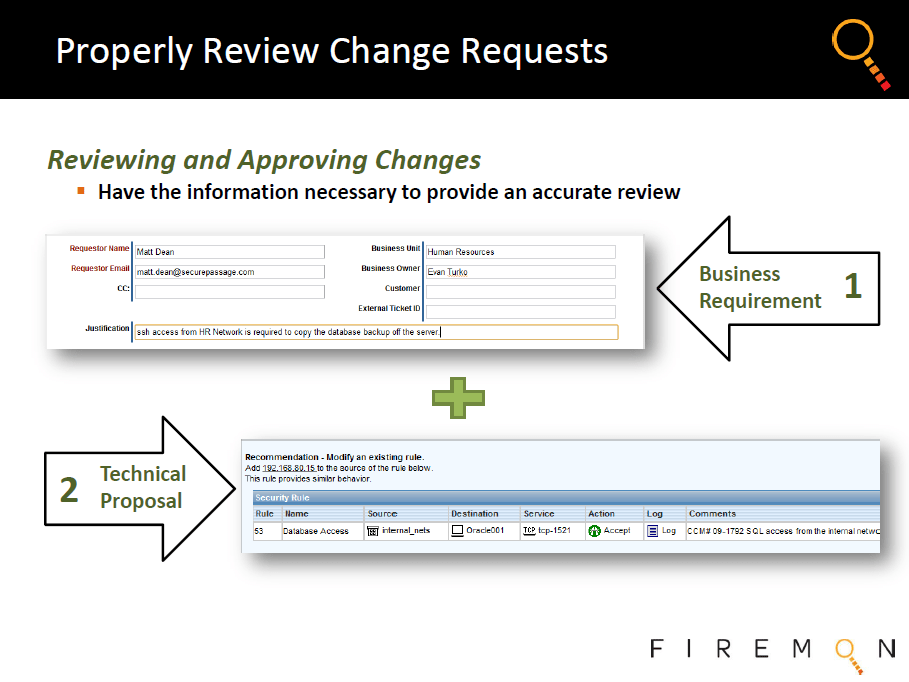
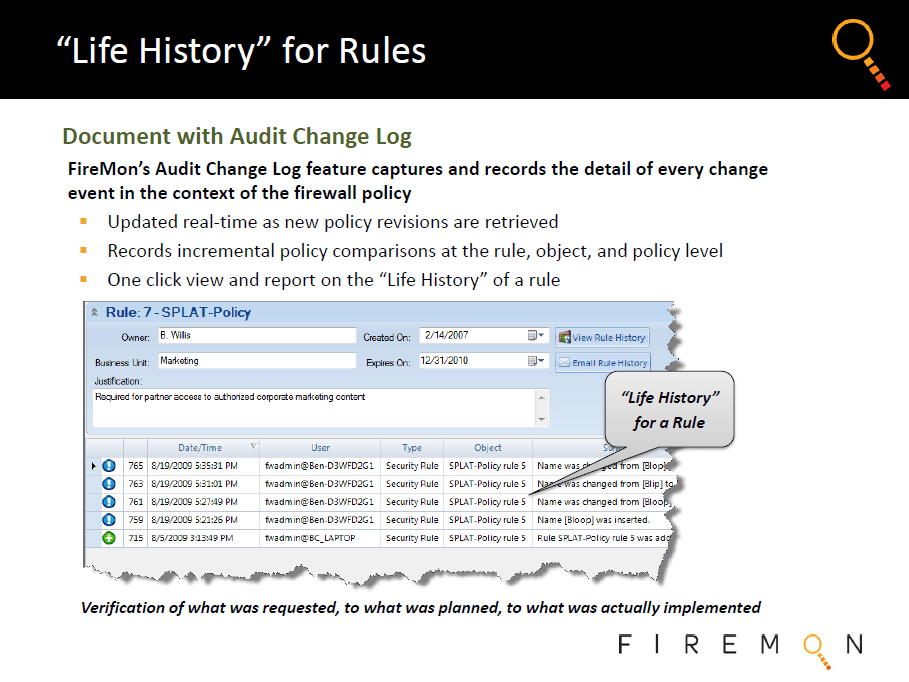
Firewall Change Management....
Further, by logging all changes to security infrastructure on a continuous basis and automatically alerting any staff responsible for affected devices, assets or policies, Security Manager creates a full end-to-end closed loop lifecycle process that drives down exposure over time and allows for constant refinement of IT risk management.
Firewall Change Management....
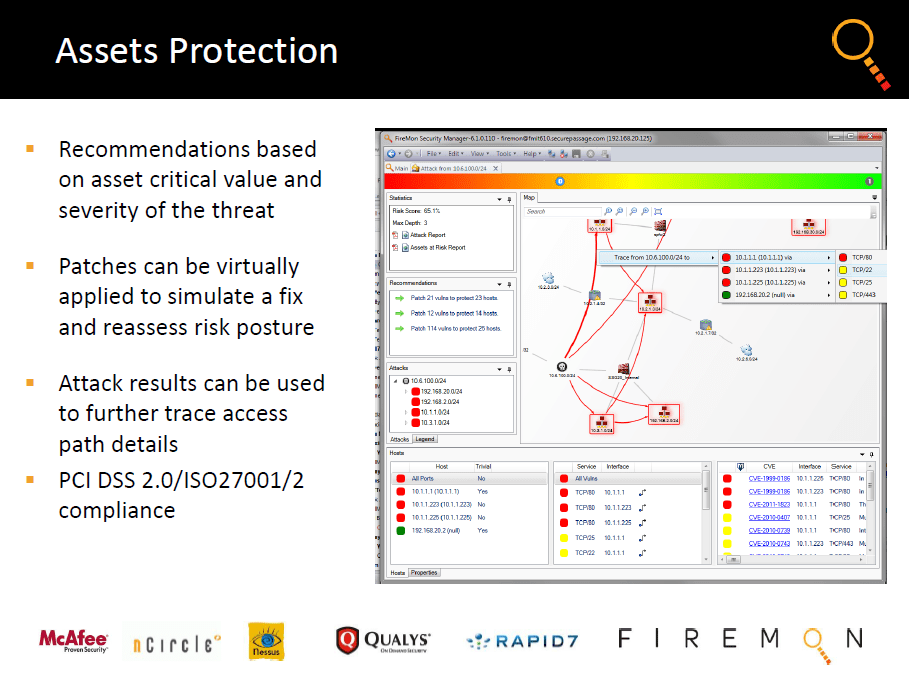
Firewall Vulnerability Management....
By integrating Security Manager directly with leading industry scanners and gaining the full context of vulnerability nature, underlying assets and exposure to potential attack, enterprises now have the ability to rapidly seek out the issues they should prioritize first and markedly reduce real-world IT risk.
Firewall Vulnerability Management....
Solutions
Network and Infrastructure Security
Zero Trust and Private Access
Endpoint and Server Protection
Vulnerability and Patch Management
Data Protection
Application Security
Secure Software and DevSecOps
Cloud Security
Identity Access Governance
Governance, Risk and Compliance
Security Intelligence Operations
Incident Response
Accreditations


Accreditations


Dubai
Office 7, Floor 14
Makeen Tower, Al Mawkib St.
Al Zahiya Area
Abu Dhabi, UAE
Sama Tower, Floor 7
Moh. Thunayan AlGhanim Str.
Jibla, Kuwait City
Kuwait
160 Kemp House, City Road
London, EC1V 2NX
United Kingdom
Company Number: 10276574
Riyadh
Office 109, Aban Center
King Abdulaziz Road
Al Ghadir
Riyadh, Saudi Arabia
The website is our proprietary property and all source code, databases, functionality, software, website designs, audio, video, text, photographs, icons and graphics on the website (collectively, the “Content”) are owned or controlled by us or licensed to us, and are protected by copyright laws and various other intellectual property rights. The content and graphics may not be copied, in part or full, without the express permission of DTS Solution LLC (owner) who reserves all rights.
DTS Solution, DTS-Solution.com, the DTS Solution logo, HAWKEYE, FYNSEC, FRONTAL, HAWKEYE CSOC WIKI and Firewall Policy Builder are registered trademarks of DTS Solution, LLC.