- About Us
-
-
- About UsWe are the regional leaders in cybersecurity. We are masters in our tradecraft. We are dynamic, talented, customer-centric, laser-focused and our mission is to defend and protect our customers from cyber adversaries through advisory, consulting, engineering, and operational services.
-
-
- Solutions
-
-
- SolutionsThe cybersecurity industry is fragmented. We have carefully curated an interoperable suite of cybersecurity products and solutions that focus on improving your security compliance and risk maturity that add real business value, effectiveness, and ROI. Combined with our professional services and security engineering expertise we design, architect, implement and operate complex environments and protect your digital space.
-
- Industry
-
-
- IndustryCyber adversaries and threat actors have no boundaries. No industry is immune to cyber-attacks. Each industry has unique attributes and requirements. At DTS we have served all industry verticals since inception and have built specialization in each segment; to ensure our customers can operate with a high degree of confidence and assurance giving them a competitive advantage.
-
- Services
-
-
- ServicesOur cybersecurity services are unmatched in the region. With our unique customer-centric approach and methodology of SSORR we provide end-to-end strategic and tactical services in cybersecurity. We on-ramp, develop, nurture, build, enhance, operationalize, inject confidence, and empower our customers.
-
-
- Vendors
- Products
- Resources
- Press Center
- Tweets
- Support
- Contact
-
DNS Security
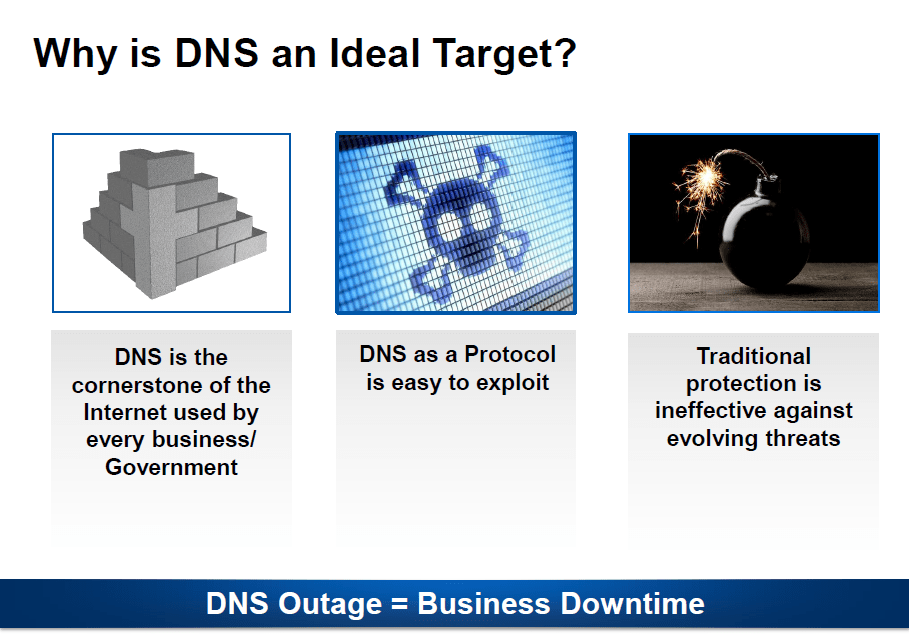
Networks are constantly being exploited using DNS for a variety of criminal purposes today. DNS is the cornerstone of the internet and attackers know that DNS is a high-value target. Without their DNS functioning properly, enterprises cannot conduct business online. DNS protocol is stateless which means attackers also cannot be traced easily.
DNS Security....
The DNS protocol can be exploited easily. It is easy to craft DNS queries that can cause the DNS server to crash or respond with a much amplified response that can congest the bandwidth. The queries can be spoofed which means attackers can direct huge amounts of traffic to its victim with the help of unsuspecting accomplices. (open resolvers on the internet). Traditional protection like firewalls leave port 53 open and don’t do much in terms of preventing DNS attacks. All these reasons make the DNS an ideal attack target.
DNS Security....
The DNS protocol can be exploited easily. It is easy to craft DNS queries that can cause the DNS server to crash or respond with a much amplified response that can congest the bandwidth. The queries can be spoofed which means attackers can direct huge amounts of traffic to its victim with the help of unsuspecting accomplices. (open resolvers on the internet). Traditional protection like firewalls leave port 53 open and don’t do much in terms of preventing DNS attacks. All these reasons make the DNS an ideal attack target.
DNS Security Challenge....
DNS security is a critical component of your infrastructure and a target for many of these attacks. Major challenges exist in securing DNS as it is an open global communication mechanism that is not well secured and often neglected in term. Enterprises can use purpose built hardware to secure their DNS infrastructure and apply best practices to ensure infrastructure is safe from modern day security threats.
DNS Security Challenge....
DNS security is a critical component of your infrastructure and a target for many of these attacks. Major challenges exist in securing DNS as it is an open global communication mechanism that is not well secured and often neglected in term. Enterprises can use purpose built hardware to secure their DNS infrastructure and apply best practices to ensure infrastructure is safe from modern day security threats.
DNS Attack Statistics....
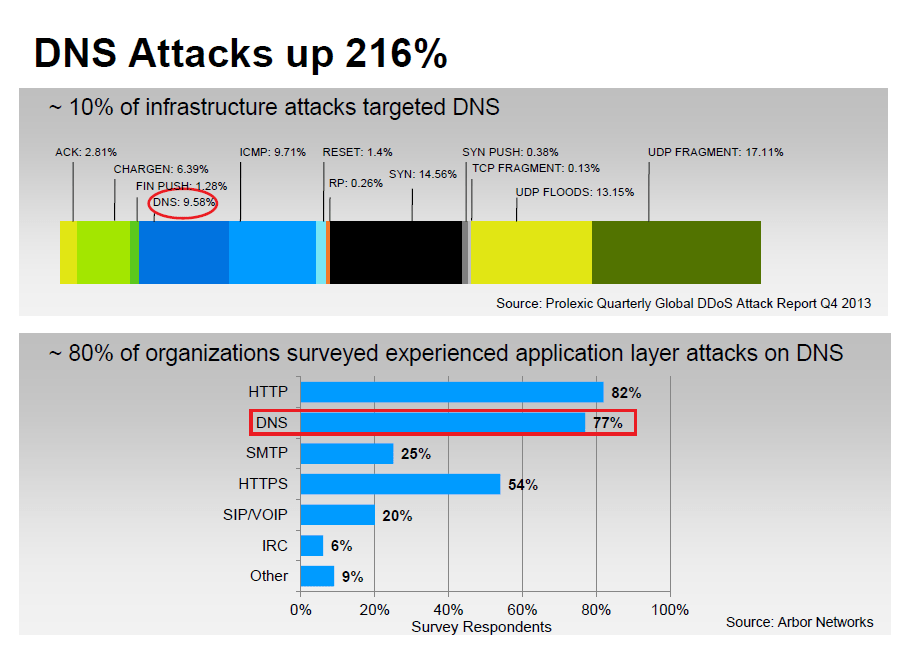
DNS infrastructure attacks have increased up 216% in 2013 alone. Approximately 10% of all layer 3 and layer 4 attacks (infrastructure layer) were targeted at DNS and this number has been growing rapidly, according to Prolexic. Arbor conducted the Infrastructure Security Survey and got about 220 responses between Nov 2012 and October 2013. Among those who responded, 80% said they experienced a DNS application layer attack. DNS is considered as the major attack vector protocol when it comes to layer 7 attacks.
DNS Attack Statistics....
DNS infrastructure attacks have increased up 216% in 2013 alone. Approximately 10% of all layer 3 and layer 4 attacks (infrastructure layer) were targeted at DNS and this number has been growing rapidly, according to Prolexic. Arbor conducted the Infrastructure Security Survey and got about 220 responses between Nov 2012 and October 2013. Among those who responded, 80% said they experienced a DNS application layer attack. DNS is considered as the major attack vector protocol when it comes to layer 7 attacks.
DNS reflection/DrDoS attacks
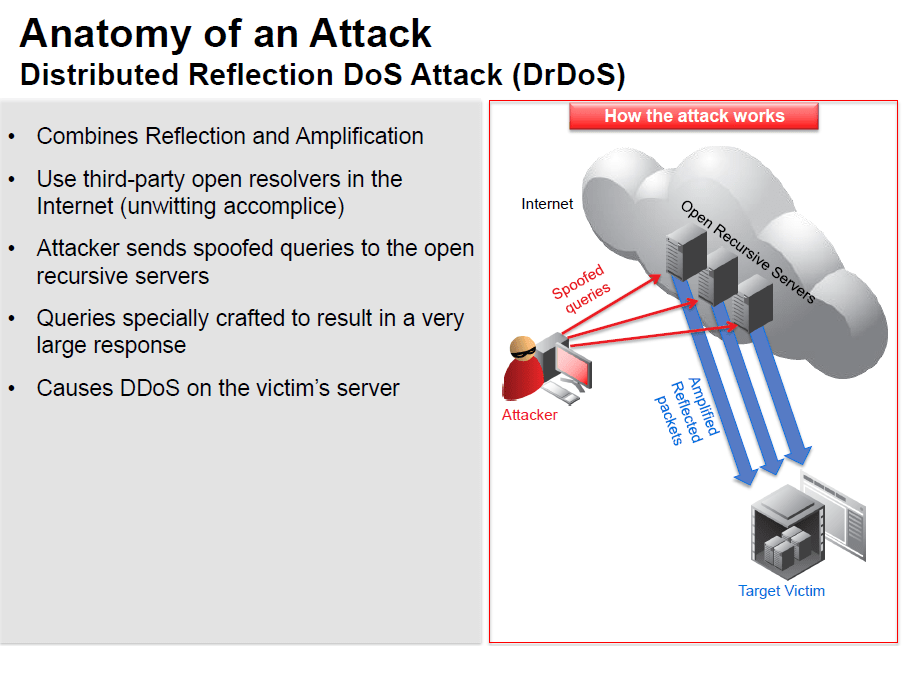
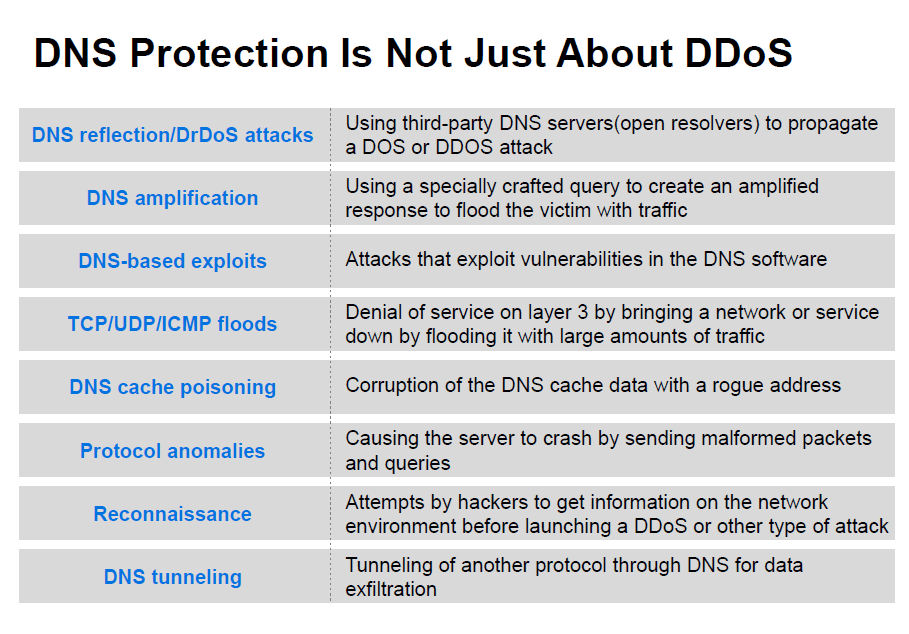
DrDoS or Distributed Reflection Denial of Service uses multiple such “host” machines or open resolvers in the internet, often thousands of servers, to launch an attack on the target victim. Amplification (described in the next row) can also be used while generating these queries to increase the impact on the victim. A high volume of such “reflected” traffic could overwhelm the victim server and bring down the victim’s site, thereby creating a Denial of Service (DoS).
DNS reflection/DrDoS attacks
Reflection attacks are attacks that use a third party DNS server, mostly an open resolver, in the internet to propagate a DDoS attack on the victim’s server. A recursive server will process queries from any IP address and return responses. An attacker spoofs the DNS queries he sends to the recursive server by including the victim’s IP address as the source IP in the queries. So when the recursive name server receives the requests, it sends all the responses to the victim’s IP address.
DrDoS or Distributed Reflection Denial of Service uses multiple such “host” machines or open resolvers in the internet, often thousands of servers, to launch an attack on the target victim. Amplification (described in the next row) can also be used while generating these queries to increase the impact on the victim. A high volume of such “reflected” traffic could overwhelm the victim server and bring down the victim’s site, thereby creating a Denial of Service (DoS).
DNS amplification
DNS amplification is an attack where a large number of specially crafted DNS queries are sent to the victim server. These specially crafted queries result in a very large response that can reach up to 70 times the size of the request. Since DNS relies on the User Datagram Protocol (UDP), the attacker can use a small volume of outbound traffic to cause the DNS server to generate a much larger volume. When the victim tries to respond to these specially crafted queries, the amplification congests the DNS server’s outbound bandwidth. This results in a Denial of Service (DoS).
DNS-based exploits
These are attacks that exploit vulnerabilities in the DNS software. This causes the DNS software to terminate abnormally, causing the server to stop responding or crash.
TCP/UDP/ICMP floods
ICMP attacks use network devices like routers to send error messages when a requested service is not available or the remote server cannot be reached. Examples of ICMP attacks include ping floods, ping-of-death and smurf attacks. This overwhelms the victim server or causes it to crash due to overflow of memory buffers.
DNS cache poisoning
Corruption of DNS cache data. It involves inserting a false address record for an Internet domain into the DNS query. If the DNS server accepts the record, subsequent requests for the address of the domain are answered with the address of a server controlled by the attacker. For as long as the false entry is cached, incoming web requests and emails will go to the attacker’s address. New cache-poisoning attacks such as the “birthday paradox” use brute force, flooding DNS responses and queries at the same time, hoping to get a match on one of the responses and poison the cache. Cache poisoning prevents access or redirects the clients to a rogue address, preventing legitimate users from accessing the company’s site. Inducing a name server to cache bogus resource records can redirect web browsers to bogus replicas of web sites, where logins, passwords and credit card numbers are captured email to hostile mail servers, where mail can be recorded or modified.
Protocol anomalies
Send malformed DNS packets, including unexpected header and payload values, to the targeted server. They make use of software bugs in protocol parsing and processing implementation. The victim server stops responding by going into an infinite loop or crashes.
Reconnaissance
This attack consists of attempts to get information on the network environment before launching a large DDoS or other type of attack. Techniques include port scanning and finding versions and authors. These attacks exhibit abnormal behavior patterns that, if identified, can provide early warning. No direct effect on the server but indicates an impending attack.
DNS tunneling
This attack involves tunneling another protocol through DNS port 53—which is allowed if the firewall is configured to carry non-DNS traffic—for the purposes of data exfiltration. A free ISC-licensed tunneling application for forwarding IPv4 traffic through DNS servers is widely used in this kind of attack.
DNS amplification
DNS-based exploits
TCP/UDP/ICMP floods
ICMP attacks use network devices like routers to send error messages when a requested service is not available or the remote server cannot be reached. Examples of ICMP attacks include ping floods, ping-of-death and smurf attacks. This overwhelms the victim server or causes it to crash due to overflow of memory buffers.
DNS cache poisoning
Protocol anomalies
Reconnaissance
DNS tunneling
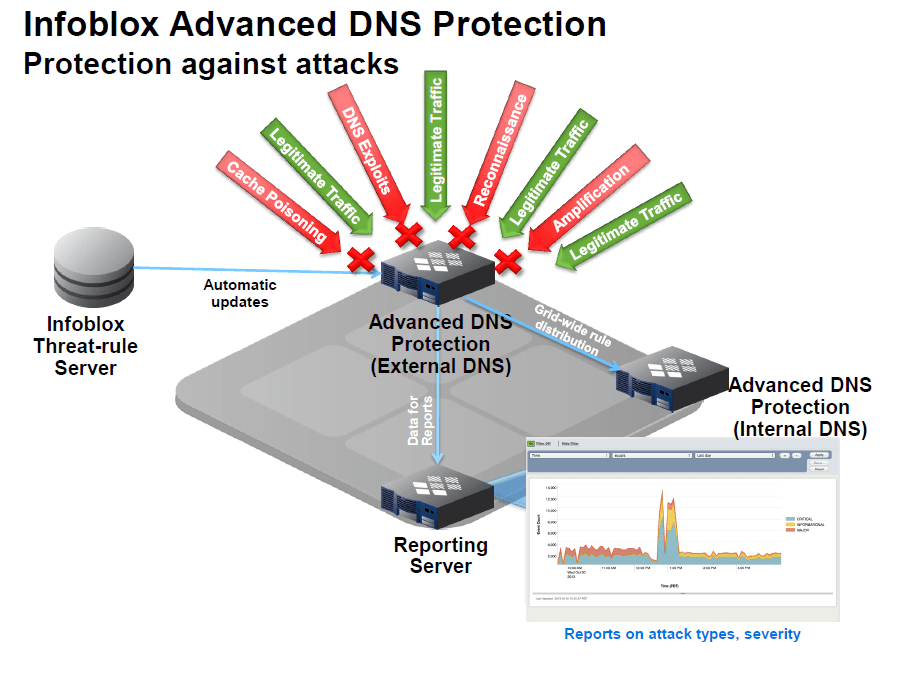
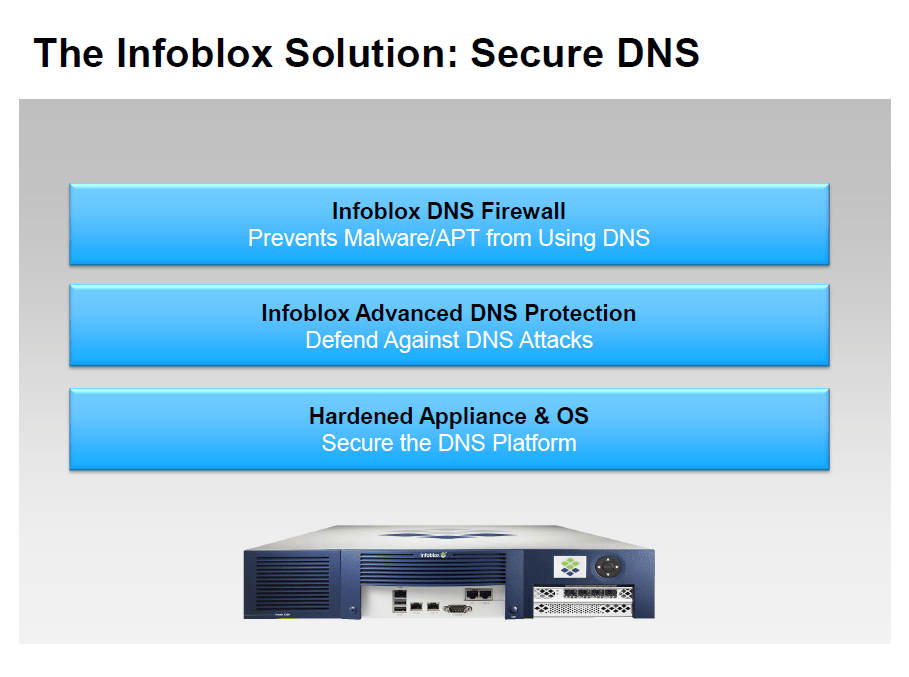
The DNS Security Solution ....
The Infoblox Secure DNS solution address the DNS security challenge. It includes our hardened appliance and OS for securing the platform, Advanced DNS Protection to defend against attacks that target the DNS and try to bring it down and finally DNS Firewall to block malware and APT from exploiting DNS to communicate with its command and control site.
The DNS Security Solution ....
The Infoblox Secure DNS solution address the DNS security challenge. It includes our hardened appliance and OS for securing the platform, Advanced DNS Protection to defend against attacks that target the DNS and try to bring it down and finally DNS Firewall to block malware and APT from exploiting DNS to communicate with its command and control site.
Combating Malware/APT with DNS Security....
- Customers shopped elsewhere because they lost faith in the retailers.
- They also had to hire a 3rd party vendor to do forensics on their environment to find out what happened.
- IT lost productivity because all servers and POS systems had to checked, updated and cleaned.
Combating Malware/APT with DNS Security....
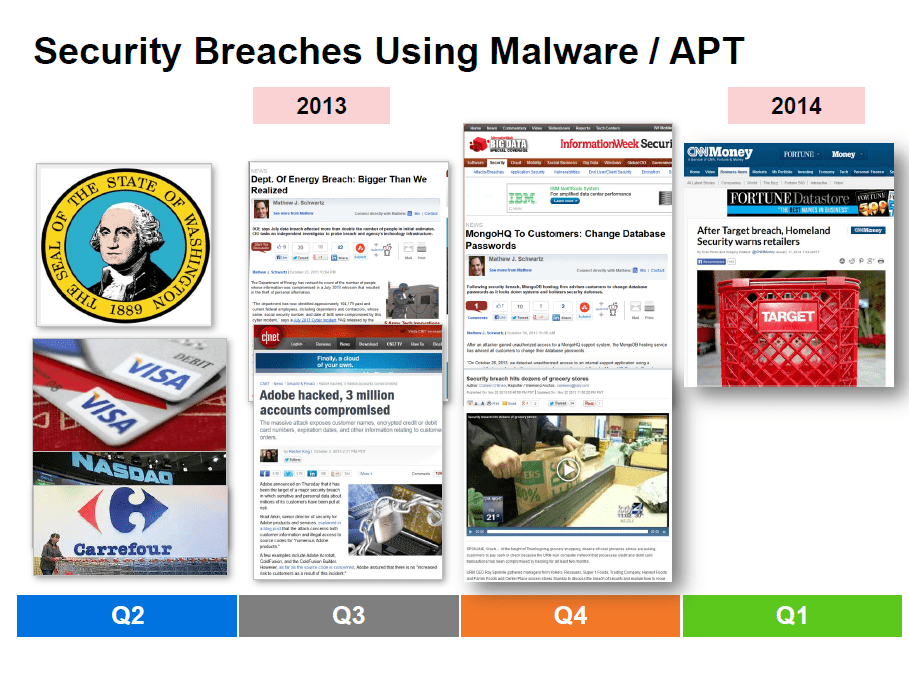
Before we talk about disrupting Malware which maybe random or targeted we need to understand the problem first. The problem is malware is used to drive security breaches around sensitive information or to steal money.
Before you on the screen right now is just some of the breaches from CQ’ 2013 into CQ1’ 2014 that used Malware extensively. Let me go through a couple of examples. In the 1st quarter, the NY Times was hacked and information exfiltrated over a period of 4 months. An outside company was brought in at great expense to clean up the NY Times infrastructure. The outside vendor found 45 different malware instances only 1 of which was caught by Anti-Virus.
In the 2nd quarter it was announced that Malware was used to steal credit card numbers and other information from the likes of VISA, JC Penneys, NASDAQ and Carrefour which totaled $300 million.
In the 3rd quarter of this year Adobe was hacked using malware and a outside security researcher discovered the breach when he found source code for 4 of Adobe’s products on a known hacker website.
- Customers shopped elsewhere because they lost faith in the retailers.
- They also had to hire a 3rd party vendor to do forensics on their environment to find out what happened.
- IT lost productivity because all servers and POS systems had to checked, updated and cleaned.
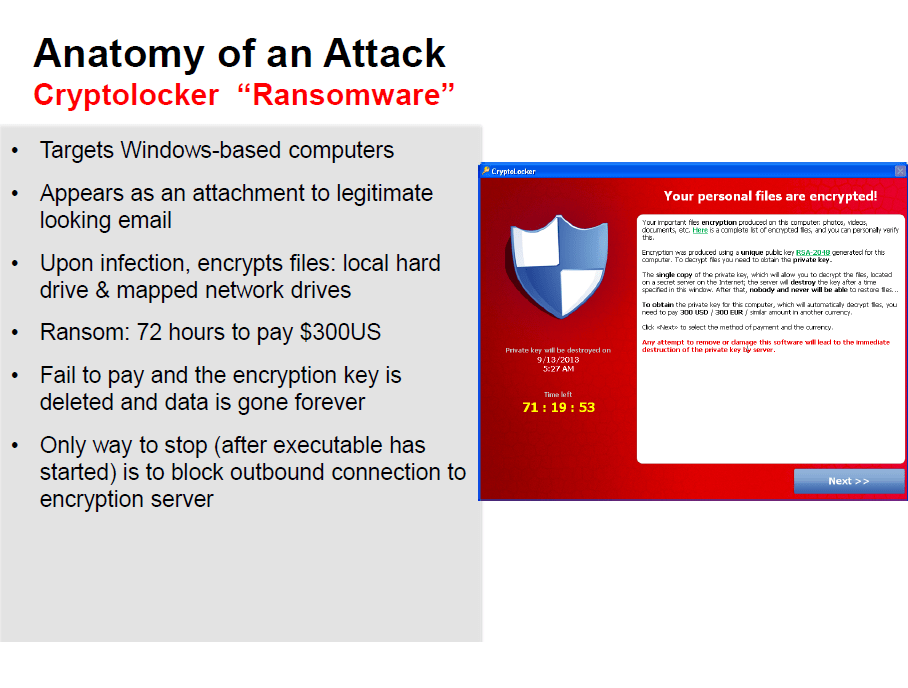
The only way to stop the encryption process is block access to the Encryption servers on the Internet. Infoblox DNS Firewall disrupts CryptoLocker by blocking DNS queries to the Encryption servers.
The only way to stop the encryption process is block access to the Encryption servers on the Internet. Infoblox DNS Firewall disrupts CryptoLocker by blocking DNS queries to the Encryption servers.
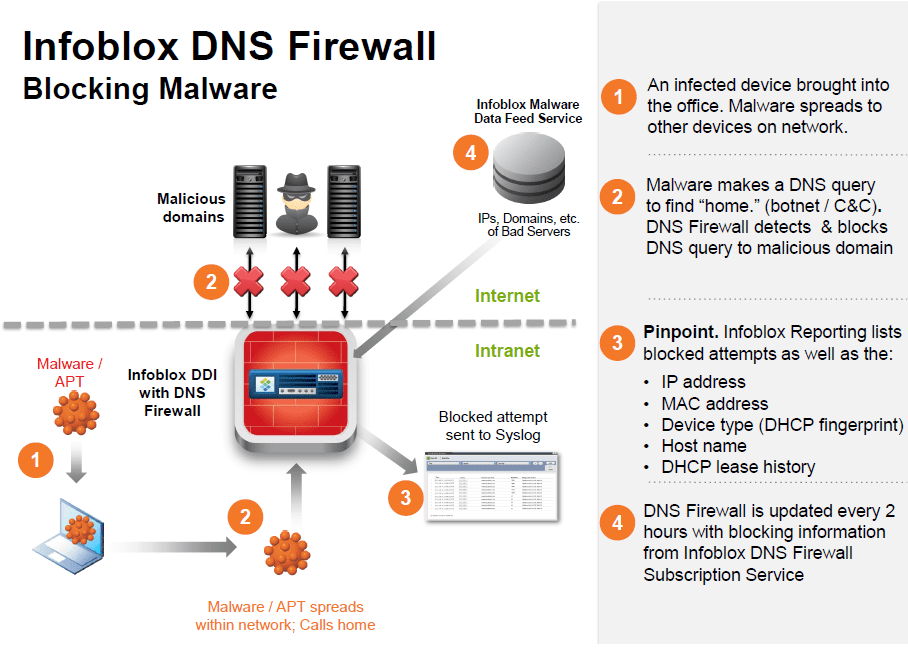
Infoblox DNS Firewall – How does it work?
- An infected mobile device is brought into the office. Upon connection, the malware starts to spread to other devices on the network.
- The malware makes a DNS query for “bad” domain to find “home.” The DNS Firewall has the “bad” domain in its table and blocks the connection.
- The DNS Server is continually updated by a reputational data feed service to reflect the rapidly changing list of malicious domains.
- Infoblox Reporting provides list of blocked attempts as well as the
- IP address
- MAC address
- Device type (DHCP fingerprint)
- Host Name
- DHCP Lease history (on/off network)
- Reputation data comes from:
- Infoblox DNS Firewall Subscription Service – blocking data on domains and IP addresses from 35+ sources throughout the world. Geo-blocking also apart of the service as well
Infoblox DNS Firewall – How does it work?
- An infected mobile device is brought into the office. Upon connection, the malware starts to spread to other devices on the network.
- The malware makes a DNS query for “bad” domain to find “home.” The DNS Firewall has the “bad” domain in its table and blocks the connection.
- The DNS Server is continually updated by a reputational data feed service to reflect the rapidly changing list of malicious domains.
- Infoblox Reporting provides list of blocked attempts as well as the
- IP address
- MAC address
- Device type (DHCP fingerprint)
- Host Name
- DHCP Lease history (on/off network)
- Reputation data comes from:
- Infoblox DNS Firewall Subscription Service – blocking data on domains and IP addresses from 35+ sources throughout the world. Geo-blocking also apart of the service as well
See also:
Solutions
Network and Infrastructure Security
Zero Trust and Private Access
Endpoint and Server Protection
Vulnerability and Patch Management
Data Protection
Application Security
Secure Software and DevSecOps
Cloud Security
Identity Access Governance
Governance, Risk and Compliance
Security Intelligence Operations
Incident Response
Accreditations


Accreditations


Dubai
Office 7, Floor 14
Makeen Tower, Al Mawkib St.
Al Zahiya Area
Abu Dhabi, UAE
Mezzanine Floor, Tower 3
Mohammad Thunayyan Al-Ghanem Street, Jibla
Kuwait City, Kuwait
+971 4 3383365
[email protected]
160 Kemp House, City Road
London, EC1V 2NX
United Kingdom
Company Number: 10276574
The website is our proprietary property and all source code, databases, functionality, software, website designs, audio, video, text, photographs, icons and graphics on the website (collectively, the “Content”) are owned or controlled by us or licensed to us, and are protected by copyright laws and various other intellectual property rights. The content and graphics may not be copied, in part or full, without the express permission of DTS Solution LLC (owner) who reserves all rights.
DTS Solution, DTS-Solution.com, the DTS Solution logo, HAWKEYE, FYNSEC, FRONTAL, HAWKEYE CSOC WIKI and Firewall Policy Builder are registered trademarks of DTS Solution, LLC.