- About Us
-
-
- About UsWe are the regional leaders in cybersecurity. We are masters in our tradecraft. We are dynamic, talented, customer-centric, laser-focused and our mission is to defend and protect our customers from cyber adversaries through advisory, consulting, engineering, and operational services.
-
-
- Solutions
-
-
- SolutionsThe cybersecurity industry is fragmented. We have carefully curated an interoperable suite of cybersecurity products and solutions that focus on improving your security compliance and risk maturity that add real business value, effectiveness, and ROI. Combined with our professional services and security engineering expertise we design, architect, implement and operate complex environments and protect your digital space.
-
- Industry
-
-
- IndustryCyber adversaries and threat actors have no boundaries. No industry is immune to cyber-attacks. Each industry has unique attributes and requirements. At DTS we have served all industry verticals since inception and have built specialization in each segment; to ensure our customers can operate with a high degree of confidence and assurance giving them a competitive advantage.
-
- Services
-
-
- ServicesOur cybersecurity services are unmatched in the region. With our unique customer-centric approach and methodology of SSORR we provide end-to-end strategic and tactical services in cybersecurity. We on-ramp, develop, nurture, build, enhance, operationalize, inject confidence, and empower our customers.
-
-
- Vendors
- Products
- Resources
- Press Center
- Tweets
- Support
- Contact
-
Security Operations Center
DTS Solution can help your organization strategize, develop and build a Next Generation Security Operations Center – SOC 2.0 to protect your information assets whilst counteracting the ever changing threat landscape.
In the past, large corporations have implemented traditional security operations centers as a means to maintain visibility regarding their information security posture. The most popular model has centered on building large command centers, where numerous analysts work side by side to assess real-time security data and manually respond to it. This is what is referred to as SOC 1.0. Although this model has proven effective, the days of SOC 1.0 are numbered.
Building a Security Operations Center
With the threat landscape ever changing within the cyber world, next generation of threats and attack vectors surfacing; information assets are more vulnerable than ever before. Organizations are now having to accept that a shift in paradigm of Information Security Operations and Maintenance needs to be implemented to keep one step ahead of the intruders.
This has led to organizations to invest heavily in protecting their information assets perimeter wide – utilizing multiple security platforms such as next generation firewalls, intrusion prevention systems, data leakage prevention devices, endpoint security etc.
The huge level of investments made by CIO’s has not necessarily translated into better protection or mitigation of information theft. Year 2011 has seen a vast number of major security breaches across major corporations and industries proving that as information security awareness continues to rise the shortfalls in proactive monitoring, maintenance, management and threat mitigation of security still remains.
With the vast number of information security breaches and the increased number of high profile and well publicized security incidents have left many executives, security professionals wondering how effective the deployed controls have been.
It is difficult to imagine these large corporations (needless to mention them) did not have security mechanisms and controls in place. Indeed they did, but the matter of fact is, investing in security infrastructure to protect your assets does not by default entitle you with protection.
Information security needs to be built as a process that becomes the core of any organization. Developing and building a Security Operations Center 2.0 practice around this exact process empowers your organization to augment the different security functions across your organization; be it audit, finance, HR, network, systems, applications etc.
Building a Security Operations Center
With the threat landscape ever changing within the cyber world, next generation of threats and attack vectors surfacing; information assets are more vulnerable than ever before. Organizations are now having to accept that a shift in paradigm of Information Security Operations and Maintenance needs to be implemented to keep one step ahead of the intruders.
This has led to organizations to invest heavily in protecting their information assets perimeter wide – utilizing multiple security platforms such as next generation firewalls, intrusion prevention systems, data leakage prevention devices, endpoint security etc.
The huge level of investments made by CIO’s has not necessarily translated into better protection or mitigation of information theft. Year 2011 has seen a vast number of major security breaches across major corporations and industries proving that as information security awareness continues to rise the shortfalls in proactive monitoring, maintenance, management and threat mitigation of security still remains.
With the vast number of information security breaches and the increased number of high profile and well publicized security incidents have left many executives, security professionals wondering how effective the deployed controls have been.
It is difficult to imagine these large corporations (needless to mention them) did not have security mechanisms and controls in place. Indeed they did, but the matter of fact is, investing in security infrastructure to protect your assets does not by default entitle you with protection.
Information security needs to be built as a process that becomes the core of any organization. Developing and building a Security Operations Center 2.0 practice around this exact process empowers your organization to augment the different security functions across your organization; be it audit, finance, HR, network, systems, applications etc.
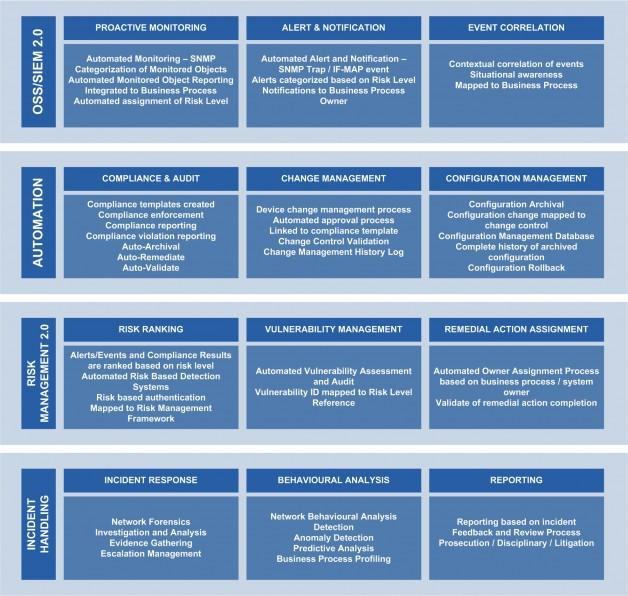
SOC 2.0 – Functional Components
- Operation Support System (OSS) / SIEM 2.0
- Automation
- Risk Management 2.0
- Incident Handling
DTS Solution – “Next Generation Security Operations Center – SOC 2.0” whitepaper can be downloaded here.
SOC 2.0 – Functional Components
- Operation Support System (OSS) / SIEM 2.0
- Automation
- Risk Management 2.0
- Incident Handling
Each of the above elements interact with one another to create a comprehensive workflow for SOC 2.0 operations. Without doubt ‘people’ operating the SOC 2.0 environment play a major role in the day to day operations; either working as part of a dedicated team or a virtual team. However the efficient and effective way in which technology is deployed single handedly determines how optimized the entire SOC 2.0 process flow actually is.
DTS Solution can help your organization carry out a feasibility study and assessment on SOC 2.0. Providing you due diligence on SOC 2.0 initiatives whilst aligning business and governance needs into the overall workflow process. Combining that with our compliance consulting expertise on ITILv3 and ISO27002 we can help your organization develop, build and operate SOC 2.0 that drastically improves the security posture of your organization whilst reducing significant costs that are ordinarily attributed to security incidents.
Solutions
Network and Infrastructure Security
Zero Trust and Private Access
Endpoint and Server Protection
Vulnerability and Patch Management
Data Protection
Application Security
Secure Software and DevSecOps
Cloud Security
Identity Access Governance
Governance, Risk and Compliance
Security Intelligence Operations
Incident Response
Accreditations


Accreditations


Dubai
Office 7, Floor 14
Makeen Tower, Al Mawkib St.
Al Zahiya Area
Abu Dhabi, UAE
Sama Tower, Floor 7
Moh. Thunayan AlGhanim Str.
Jibla, Kuwait City
Kuwait
160 Kemp House, City Road
London, EC1V 2NX
United Kingdom
Company Number: 10276574
Riyadh
Office 109, Aban Center
King Abdulaziz Road
Al Ghadir
Riyadh, Saudi Arabia
The website is our proprietary property and all source code, databases, functionality, software, website designs, audio, video, text, photographs, icons and graphics on the website (collectively, the “Content”) are owned or controlled by us or licensed to us, and are protected by copyright laws and various other intellectual property rights. The content and graphics may not be copied, in part or full, without the express permission of DTS Solution LLC (owner) who reserves all rights.
DTS Solution, DTS-Solution.com, the DTS Solution logo, HAWKEYE, FYNSEC, FRONTAL, HAWKEYE CSOC WIKI and Firewall Policy Builder are registered trademarks of DTS Solution, LLC.