- About Us
-
-
- About UsWe are the regional leaders in cybersecurity. We are masters in our tradecraft. We are dynamic, talented, customer-centric, laser-focused and our mission is to defend and protect our customers from cyber adversaries through advisory, consulting, engineering, and operational services.
-
-
- Solutions
-
-
- SolutionsThe cybersecurity industry is fragmented. We have carefully curated an interoperable suite of cybersecurity products and solutions that focus on improving your security compliance and risk maturity that add real business value, effectiveness, and ROI. Combined with our professional services and security engineering expertise we design, architect, implement and operate complex environments and protect your digital space.
-
- Industry
-
-
- IndustryCyber adversaries and threat actors have no boundaries. No industry is immune to cyber-attacks. Each industry has unique attributes and requirements. At DTS we have served all industry verticals since inception and have built specialization in each segment; to ensure our customers can operate with a high degree of confidence and assurance giving them a competitive advantage.
-
- Services
-
-
- ServicesOur cybersecurity services are unmatched in the region. With our unique customer-centric approach and methodology of SSORR we provide end-to-end strategic and tactical services in cybersecurity. We on-ramp, develop, nurture, build, enhance, operationalize, inject confidence, and empower our customers.
-
-
- Vendors
- Products
- Resources
- Press Center
- Tweets
- Support
- Contact
-
Threat Modelling
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.
With the completed exercise of threat modeling, DTS Solution will help utilize the threat models and attack surface analysis information to develop advance monitoring and correlation rules within your SIEM solution to ensure any attack vectors are identified proacticely through your Security Operations Center.
Threat Modelling Critical Services
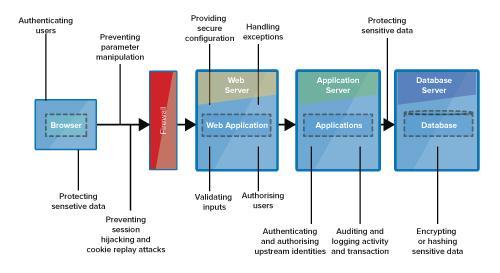
Protecting critical business services from potential cyber risks should be one of the most important task your IT security team should perform. More often that not the right approach to implementing cyber defense mechanisms to protect critical services are adhoc, inconsistent and most likely follow insecure-by-design principles due to various internal factors. Identifying the multidimensional exact attack surface of the service may not be adequately performed leaving the service vulnerable to potential external and internal cyber threats.
DTS Solution can help your organization identify critical services, perform a complete threat modeling exercise across your critical services that may compose of complex interconnected web applications, API interfaces, middleware systems, databases, authentication servers and many more that all interact with each other to deliver the service.
Threat Modelling Critical Services
DTS Solution can help your organization identify critical services, perform a complete threat modeling exercise across your critical services that may compose of complex interconnected web applications, API interfaces, middleware systems, databases, authentication servers and many more that all interact with each other to deliver the service.
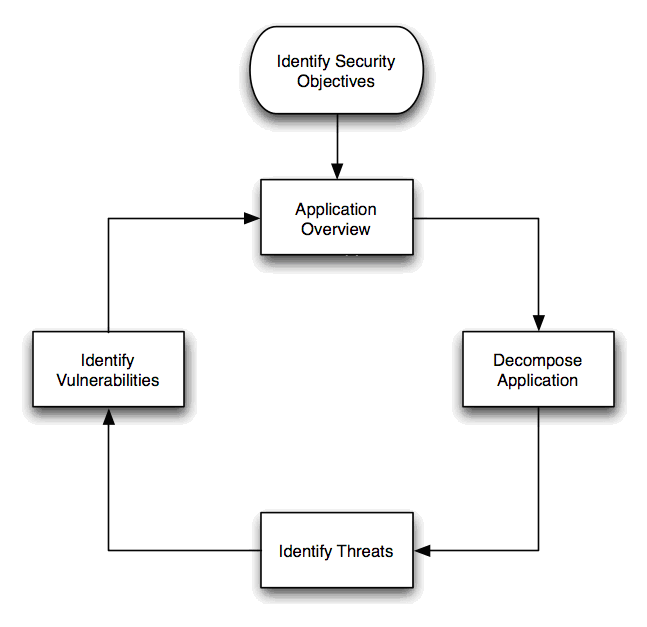
Threat Modelling Methodology
Threat Modelling Methodology
Various Threat Modeling Methodologies exist but mainly related to Software Development (DevOps) which does not provide the complete picture of how services interact as important layers such as networking, zoning, isolation, micro-segmentation, operations, administration and cyber security are not considered. OWASP Application Threat Modeling Methodology although very comprehensive only addresses application security.
Attack Surface Analysis
Attack Surface Analysis
SQL Injections, XSS, CSRF, API validation, Remote Access, Administrator Access, Authetnication using 2FA/OTP, Unauthorized Database Admin Access, Unknown 3rd party system interactions, storage of backup FTP folder to unknown location, monitoring agent using a Service Account that is not unique etc. are just some attack surface analysis performed, subsequently, identifying the appropriate countermeasures to protect against those threat vectors, leading to a “Secure-by-Design” or “Secured-by-Monitoring” environment.
Security Threat Case Monitoring
- Develop a Threat Modeling Methodology
- Perform Attack Surface Analysis
- Threat Model Templates
- Threat Trees and Attack Chaining
- Security Threat Case Monitoring
Security Threat Case Monitoring
- Develop a Threat Modeling Methodology
- Perform Attack Surface Analysis
- Threat Model Templates
- Threat Trees and Attack Chaining
- Security Threat Case Monitoring
Solutions
Network and Infrastructure Security
Zero Trust and Private Access
Endpoint and Server Protection
Vulnerability and Patch Management
Data Protection
Application Security
Secure Software and DevSecOps
Cloud Security
Identity Access Governance
Governance, Risk and Compliance
Security Intelligence Operations
Incident Response
Accreditations

Accreditations

Dubai
Office 7, Floor 14
Makeen Tower, Al Mawkib St.
Al Zahiya Area
Abu Dhabi, UAE
Mezzanine Floor, Tower 3
Mohammad Thunayyan Al-Ghanem Street, Jibla
Kuwait City, Kuwait
+971 4 3383365
[email protected]
160 Kemp House, City Road
London, EC1V 2NX
United Kingdom
Company Number: 10276574
The website is our proprietary property and all source code, databases, functionality, software, website designs, audio, video, text, photographs, icons and graphics on the website (collectively, the “Content”) are owned or controlled by us or licensed to us, and are protected by copyright laws and various other intellectual property rights. The content and graphics may not be copied, in part or full, without the express permission of DTS Solution LLC (owner) who reserves all rights.
DTS Solution, DTS-Solution.com, the DTS Solution logo, HAWKEYE, FYNSEC, FRONTAL, HAWKEYE CSOC WIKI and Firewall Policy Builder are registered trademarks of DTS Solution, LLC.