Companies take great care to secure their networks, but even with responsible and sustained investments in their defenses, companies are still at risk. Hackers bypass the security controls by finding a loophole that is revealed with persistent efforts from the hackers. This is how a network is breached and can be best described as a Zero-day attack.
Zero-day attacks can be described as attacks that are unknown to vendors or software developers. The main feature of a Zero-day attack is that nobody knows the specific techniques used in the attack until it occurs. Usually, Zero-day attacks make use of Zero-day vulnerabilities and Zero-day exploits to achieve the end goal of compromising a target system. Consequently, Zero-day vulnerabilities and Zero-day exploits can be best described as vulnerabilities and exploits that have not been uncovered yet and thus are impossible to patch. It is very common for software vendors to discover a vulnerability or an effective exploit against their product only after a Zero-day attack occurs, making use of those vulnerabilities and exploits.
Companies take great care to secure their networks, but even with responsible and sustained investments in their defenses, companies are still at risk. Hackers bypass the security controls by finding a loophole that is revealed with persistent efforts from the hackers. This is how a network is breached and can be best described as a Zero-day attack.
Zero-day attacks can be described as attacks that are unknown to vendors or software developers. The main feature of a Zero-day attack is that nobody knows the specific techniques used in the attack until it occurs. Usually, Zero-day attacks make use of Zero-day vulnerabilities and Zero-day exploits to achieve the end goal of compromising a target system. Consequently, Zero-day vulnerabilities and Zero-day exploits can be best described as vulnerabilities and exploits that have not been uncovered yet and thus are impossible to patch. It is very common for software vendors to discover a vulnerability or an effective exploit against their product only after a Zero-day attack occurs, making use of those vulnerabilities and exploits.
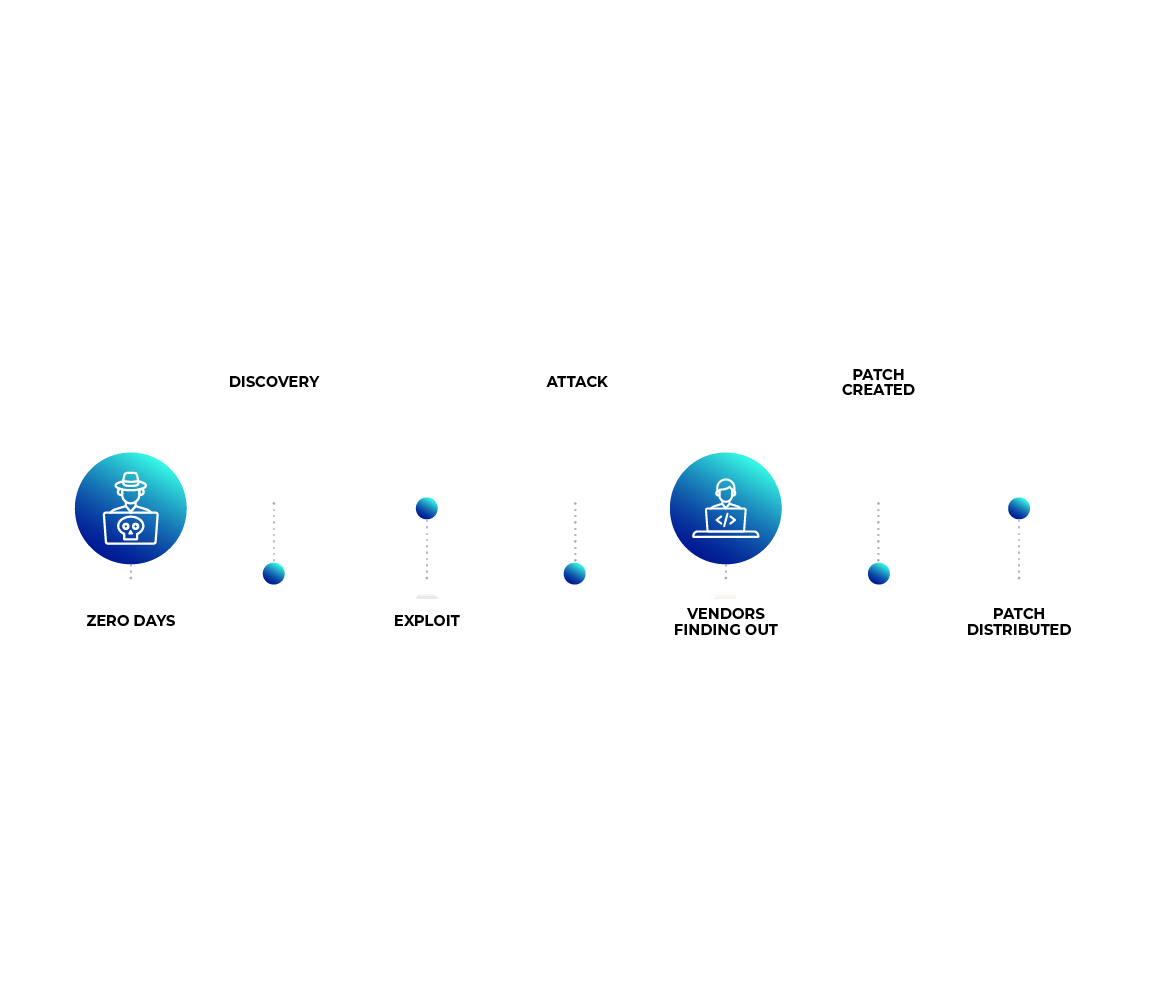
Anatomy of a Zero-day Attack
A hacker finds a zero-day vulnerability through weeks and months of painstaking efforts. Efforts that consist of scanning application code, looking for weaknesses and flaws, targeting and testing the application or a system with inputs until he reveals a small weakness in the defenses that provides him a yet unknown way to penetrate the system or application.
Once a zero-day vulnerability has been discovered, hackers could help the software vendor by providing the information on the Zero-day vulnerability. This however is a rare occurrence. Hackers instead either sell the newly found Zero-day details on the dark web or start crafting a zero-day exploit to use in an attack. Either way, the newly crafted zero-day exploit is incorporated into an attacker’s customized attack techniques before the Zero-day attack occurs.
Anatomy of a Zero-day Attack
A hacker finds a zero-day vulnerability through weeks and months of painstaking efforts. Efforts that consist of scanning application code, looking for weaknesses and flaws, targeting and testing the application or a system with inputs until he reveals a small weakness in the defenses that provides him a yet unknown way to penetrate the system or application.
Once a zero-day vulnerability has been discovered, hackers could help the software vendor by providing the information on the Zero-day vulnerability. This however is a rare occurrence. Hackers instead either sell the newly found Zero-day details on the dark web or start crafting a zero-day exploit to use in an attack. Either way, the newly crafted zero-day exploit is incorporated into an attacker’s customized attack techniques before the Zero-day attack occurs.
Zero-day attacks are advanced threats for any organization as they require enormous efforts to be identified and mitigated in time. Even when a zero-day vulnerability is made public, large collaborative efforts are needed between the software vendors and companies to create and release a patch. Unfortunately, a large percentage of companies do not patch their systems in time or have a proper vulnerability management program that is effective in its response to zero-day vulnerabilities. To make matters worse, hackers usually start testing the new patch update as soon as it is released to try to find additional vulnerabilities and exploits.
Zero-day Attacks and the Future of Zero-day Vulnerabilities and Exploits
New and emerging security tools are being created with increased capabilities, including the ability to detect zero-day attacks. Cyber security teams can analyze and contain the attacks much easier than before giving the future some badly needed hope. But with an increase in security tools comes an increase in the creation of other software and tools that are unrelated to cyber security. It is estimated that around 90 billion lines of code are produced each year, a mind-blowing figure, exacerbating the already difficult problem of finding zero-day vulnerabilities.
It is safe to say that the number of zero-day vulnerabilities and exploits will continue to rise in the future, creating a need for highly capable security tools and experienced cyber security teams.
Zero-day Attacks and the Future of Zero-day Vulnerabilities and Exploits
New and emerging security tools are being created with increased capabilities, including the ability to detect zero-day attacks. Cyber security teams can analyze and contain the attacks much easier than before giving the future some badly needed hope. But with an increase in security tools comes an increase in the creation of other software and tools that are unrelated to cyber security. It is estimated that around 90 billion lines of code are produced each year, a mind-blowing figure, exacerbating the already difficult problem of finding zero-day vulnerabilities.
It is safe to say that the number of zero-day vulnerabilities and exploits will continue to rise in the future, creating a need for highly capable security tools and experienced cyber security teams.
How to Protect Against Zero-day Attacks
Companies are already overwhelmed with designing secure networks and systems along with choosing the most suitable protection mechanisms and tools. Additional headaches arise when trying to find experienced cyber security personnel that will be able to protect the company from external attacks.
There are no immediate fixes for zero-day exploits used in a zero-day attack since developers are still unaware of their existence. This fact might seem like it is the end of the discussion on zero-day prevention, but luckily there are many actions a company can take to decrease its chances of being exploited.
Following best practices on zero-trust network design (link the Zero trust model article?), having a solid cyber security program, and continuous efforts in increasing the security of systems, all contribute to decreasing the risk of being exploited. However, one security software technology emerged that greatly assists in today’s efforts on zero-day attack mitigation.
Detection and Response security software category is comprised of security tools that base their detection mechanisms on machine learning. Contrary to traditional detection software, detection & recovery-based security tools rely on their ability to detect any anomalies that occur in a company’s networks or endpoint systems. This greatly increases the chances of a successful defense against zero-day attacks as the security software doesn’t need any prior knowledge on the zero-day vulnerability that is being exploited. The technology is far from being perfect but provides an effective security measure against zero-day attacks.
There will never be a perfect set of security measures, tools, and procedures that will keep a company safe from zero-day attacks, but there are many actions a company can take to decrease the chances of a successful cyber-attack.
Hackers and software vendors are stuck in the never-ending race of finding zero-day vulnerabilities and issuing patches for them. Due to the nature of zero-day attacks, they are most definitely representing the biggest threat to all organizations.
With billions of lines of code being written every year, the number of zero-day vulnerabilities is bound to increase in the future, continuing the never-ending cycle of zero-day attacks and zero-day mitigation actions.
With a large collaborative effort between the software vendors and their customers, everybody is racing in applying patches for the newly found zero-day, but with limited effectiveness. Luckily, many security controls can be deployed for companies to decrease their chances of being successfully breached by zero-day exploits but should keep in mind that there is no guaranteed protection.
How to Protect Against Zero-day Attacks
Companies are already overwhelmed with designing secure networks and systems along with choosing the most suitable protection mechanisms and tools. Additional headaches arise when trying to find experienced cyber security personnel that will be able to protect the company from external attacks.
There are no immediate fixes for zero-day exploits used in a zero-day attack since developers are still unaware of their existence. This fact might seem like it is the end of the discussion on zero-day prevention, but luckily there are many actions a company can take to decrease its chances of being exploited.
Following best practices on zero-trust network design (link the Zero trust model article?), having a solid cyber security program, and continuous efforts in increasing the security of systems, all contribute to decreasing the risk of being exploited. However, one security software technology emerged that greatly assists in today’s efforts on zero-day attack mitigation.
Detection and Response security software category is comprised of security tools that base their detection mechanisms on machine learning. Contrary to traditional detection software, detection & recovery-based security tools rely on their ability to detect any anomalies that occur in a company’s networks or endpoint systems. This greatly increases the chances of a successful defense against zero-day attacks as the security software doesn’t need any prior knowledge on the zero-day vulnerability that is being exploited. The technology is far from being perfect but provides an effective security measure against zero-day attacks.
There will never be a perfect set of security measures, tools, and procedures that will keep a company safe from zero-day attacks, but there are many actions a company can take to decrease the chances of a successful cyber-attack.
Hackers and software vendors are stuck in the never-ending race of finding zero-day vulnerabilities and issuing patches for them. Due to the nature of zero-day attacks, they are most definitely representing the biggest threat to all organizations.
With billions of lines of code being written every year, the number of zero-day vulnerabilities is bound to increase in the future, continuing the never-ending cycle of zero-day attacks and zero-day mitigation actions.
With a large collaborative effort between the software vendors and their customers, everybody is racing in applying patches for the newly found zero-day, but with limited effectiveness. Luckily, many security controls can be deployed for companies to decrease their chances of being successfully breached by zero-day exploits but should keep in mind that there is no guaranteed protection.
See also:
